Are you looking for a way to improve the security of your software development process? Look no further than DevSecOps.
In this blog, we’ll explore the concepts of DevSecOps, its benefits and security tools usage and how it can be implemented in your existing DevOps practices to build a strong security foundation, reduce the risk of breaches, and ultimately deliver better quality products to your customers.
The Hashicorp Certified Vault Associate certification focuses on the security aspect of DevSecOps, specifically with Hashicorp Vault. Hashicorp Vault is a popular open-source tool that helps organizations manage, secure, and control access to sensitive data.
This certification tests the candidate’s understanding of Hashicorp Vault, including its architecture, secrets management, data encryption, and security features. The certification is ideal for DevOps engineers, security professionals, and administrators who want to demonstrate their expertise in using Hashicorp Vault to secure sensitive data in a DevSecOps environment.
By gaining the Hashicorp Certified Vault Associate certification, professionals can validate their knowledge and skills in DevSecOps, and demonstrate their commitment to securing sensitive data in their organizations.
What is Devsecops?
DevSecOps is an approach that aims to integrate security into the software development and operations process, commonly known as DevOps.
It aims to ensure that development and operations teams can work together seamlessly while ensuring that the applications and systems being developed are secure and compliant. This is achieved by including security testing and validation as an integral part of the software development process.
DevOps Vs DevSecOps
DevOps refers to a method in which the software developers and operational team work together to produce a highly agile and streamlined software development framework. On the other hand, DevSecOps aims to automate every security task by the usage of the security controls and processes into the workflow of DevOps. DevSecOps tends to extend the culture of DevOps of shared responsibility to add security practices.
In some of the aspects, DevOps and DevSecOps are found similar such as automation usage and continuous process to deliver collaborative development life cycle. However, DevOps tends to prioritize the delivery speed whereas DevSecOps carry out shifting security left or else moving security to the earliest possible areas in the development process.
Need for DevSecOps
The need for DevSecOps arises from the fact that the traditional approach to software development often prioritizes speed and efficiency over security. With DevOps, organizations are able to release new features and updates faster than ever before. However, this increased speed of development can lead to security vulnerabilities being overlooked or ignored.
Also Check: Top DevOps Certifications
DevSecOps addresses this issue by integrating security testing and validation as an integral part of the software development process. By doing so, organizations can identify and address security vulnerabilities early on in the development process, before they make it to production. This allows for the rapid development of software while still ensuring that it is secure and compliant.
Additionally, with the increasing amount of data and the complexity of systems used by organizations, there is an ever-growing need for secure software development. DevSecOps approach allows organizations to build a strong security foundation and also to comply with various regulations and standards in a timely manner.
Major components of DevSecOps
Organizations need to integrate technical and cultural transit in their approach into the DevSecOps services to find the real-time security threats in an efficient way.
DevSecOps approach has six major components and they are:
Collaboration
The collaboration starts with engaging shared responsibility mindset people relevant to the security across the organization. Collaboration mainly comes up with an objective in development and release of the high-quality product in an efficient manner and also ensuring security and compliance requirements.
Security teams carry out their task just by being familiar with the DevOps practices and integrating them to enhance the security level. Some of the examples such as delivering security capabilities in smaller and frequent installments and automation of the security tasks can be made wherever possible. Software developers, in turn, learn about the best security practices, needs, threat awareness and tools.
Communication
The communications gap between the software developers and security pros needs to be fulfilled. Security pros need to communicate the control requirements and benefits of compliance in terms of developers aspects. For example, discussion about the security risks in terms of delays in projects and extra work for the software developers can be able to address those risks.
Developers need to clearly understand the security-related responsibilities so they can fully indulge in their role and they intend to develop a secure and compliant based organization.
Compliance Management
Compliance management can be obtained with regulations and standards such as SOC 2, PCI-DSS, HIPAA, and ISO 27001 and it will be an integral part of DevOps.
Security Testing
Automated security testing tools such as vulnerability scanners, penetration testing, and static code analysis can be used to find and address the security vulnerabilities in an earlier stage during the development process.
Security Automation
With the usage of automation tools and scripts such as intrusion detection and prevention, and security incident management, it is possible to implement and enforce security policies.
How to implement DevSecOps?
DevSecOps can be integrated into a single streamlined process by the incorporation of the security at code level itself. It can ensure application and procedure safety at all the phases of the process chain.
The five prominent features of the DevSecOps such as:
- Mandatory security at every stage
- Thorough analysis of security
- Security-related changes at code level
- Automation of all the processes
- Continuous monitoring via dashboard and alerts
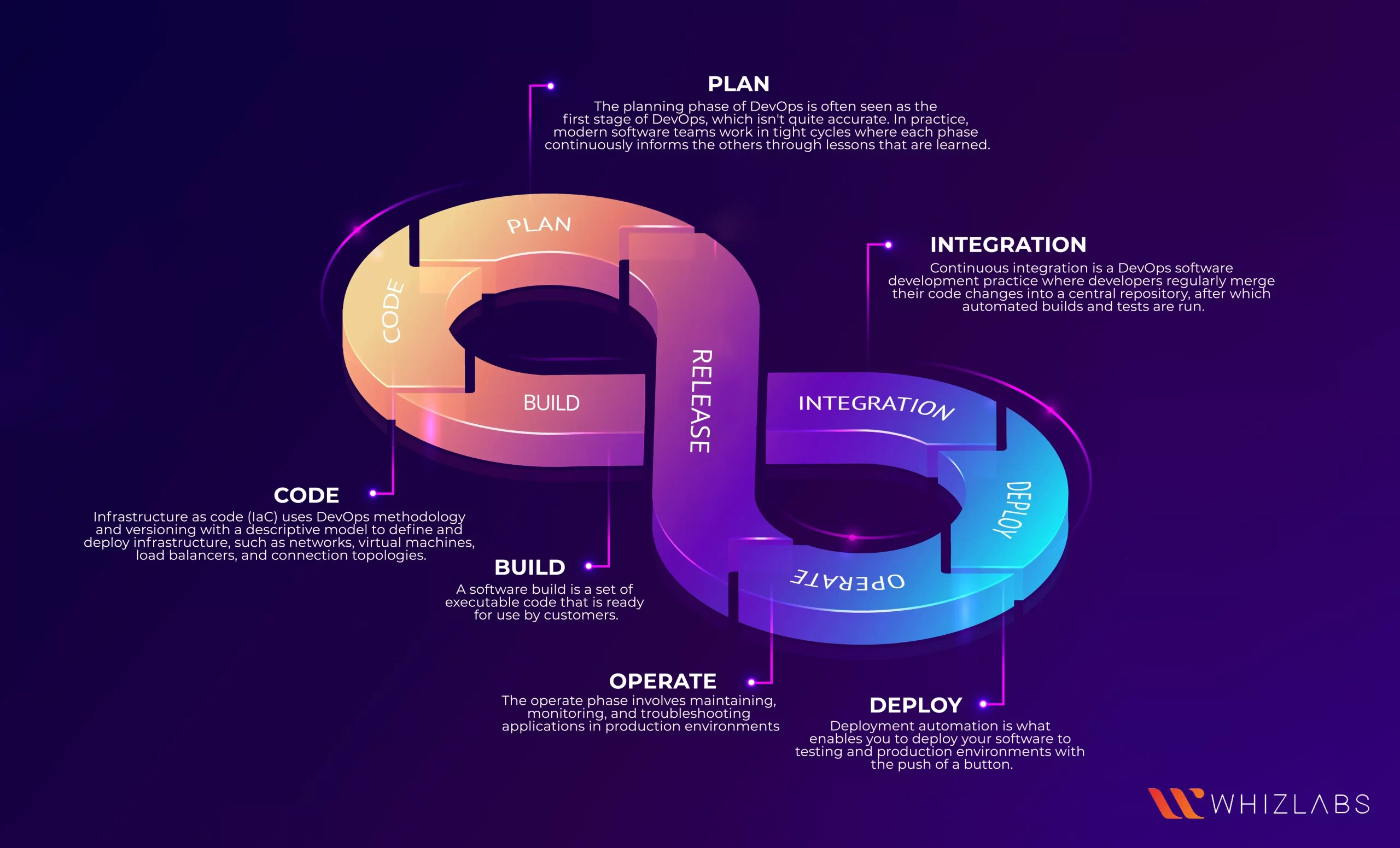
The CI pipeline is broken into six phases or stages known as Code, Build, store, Prep, deploy and Run.
- Code : The first step in the development approach such as coding the segments in both secured and trusted ways.
- Build : Coding process will be completed and comprehensive container images will be delivered, It contains core OS, run time services and application dependencies and it will need a secure process.
- Store : Off-Shelf technology stack was considered to be at risk in today’s cybersecurity landscape. At this point, each off-shelf app or back end services must be checked in a continuous manner. Fortunately, the developers must pull the dependencies securely with the application and scan for any vulnerabilities in the container image.
- Prep : Before the deployment, the firm needs to ensure that the application complies with the security policies. To attain this, validation of the configurations against the security policies of the organization is carried out before entering the next stage of the development cycle. This kind of configuration can tell how much workload must be run by simply providing key insights into the potential vulnerabilities. They must also set subsequent stages of CI or CD pipeline for the successful deployment process.
- Deploy : Scans will be delivered in the previous stages and can provide organizations with comprehensive understanding of security of the application. The misconfiguration in the development process must be identified and thus allow the organization to fix the issues and define some of the stronger security standards for the promotion of effective security posture.
- Run : As the deployments run, the DevSecOps teams can use active deployment analytics, automation and monitoring to assure the compliance while mitigating the vulnerabilities.
Security tools used in DevOps
In order to implement the DevSecOps, firms need to consider using various application security testing tools and it will be integrated in various stages of CI/CD process. Some of the commonly used security tools such as:
Static application security testing (SAST)
SAST tools are primarily employed for scanning the customized codes to detect the errors in code and design flaws that can lead to major weaknesses. SAST tools include Coverity can be used primarily during build, code and development phases of the software.
Software Composition analysis(SCA)
SCA tools including Black Duck can be able to share the scan code and binaries to predict the known vulnerabilities in the third-party and open source components. It also provides insights into the various security risks to leverage remediation and prioritization efforts. It can be integrated into CI or CD processes to detect the open-source vulnerabilities from the integration phase to the pre-production release.
Interactive application security testing(IAST)
It will work in background during the functional testing made in manual or automated manner to analyze the web application in runtime behaviors for instance, the Seeker IAST tools can use the instrumentation to seek the response or request interaction, dataflow and behavior. It also detects the vulnerabilities and replays and tests in an automated way, delivering detailed insights to the software developers down to the line of code in which it occurs. It enables the software developers to concentrate mainly on the time and effort on the vulnerabilities.
Dynamic application security testing(DAST)
It is an automated opaque testing method that can mimic like a hacker to make interaction with the web application or API. It also tests the application over networking connection and examination of clients in rendering of applications such as pen testers. It does not need any access to the source code and they can interact with the website and predict the vulnerabilities with less false positive rates. For instances, Synopsys API scanner tools can identify the vulnerabilities on the web applications such as internet- connected devices such as IoT devices, mobile back end servers, RESTful APIs etc.,
Challenges in deploying DevSecOps
The deployment of the DevsecOps can bring various challenges such as:
The first challenges will be engaging people and culture. It means it is significant to retrain the people about the DevOps team so that they can be able to understand the security best practices and know how to handle the security tooling. In the cultural aspect, the team must truly come into the mindset that they are solely responsible for software security they have been built and deployed.
The second challenge will be selecting an apt security tool and integrating it with the DevOps workflow. If the tool selected is highly automated, then it will be easy to integrate with the CI/CD pipeline and thus less training as well as cultural shift will be needed.
In some cases, selection of automated versions of security tools will not be suitable. Because the development environment changes in drastic manner over the past decades. And modern software applications consist of 70% open-source software. The accurate detection of the vulnerabilities in the open-source software cannot be carried out by the traditional security tools.
Similarly, the cloud native applications used in the containers will spin up and down in a quicker manner. The traditional security tools used in the production department cannot assess applications risks which are running in the containers.
Benefits of DevSecOps
Of course, many companies cannot bypass security measures to gain revenue, but that’s a gamble that can backfire in a catastrophic manner. And it significantly causes app rollout to be compromised and it primarily affects company growth. Then there will be a risk of various security issues after the launch of the product and thus the end users will be dissatisfied by using this product.
Also Read : How to Become Microsoft Azure DevOps Engineer?
In order to address the challenges of DevOps security, DevSecOps were introduced. Let’s dig in to know the benefits of adopting the DevSecOps:
- By means of process automation, the rate of occurrences of mistakes and administration failures will be reduced
- Better collaboration and communication between the teams
- High flexibility in managing the sudden changes during the software development lifecycle
- Various significant opportunities for the automated builds and quality assurance testing
- Better Return On Investment(ROI) in the existing security infrastructure of an organization
Due to the increased demand, the number of DevSecOps Certifications are becoming famous. They are mainly applied to the DevSecOps jobs such as Managers, specialists, DevSecOps Engineers, consultants, software developers, IT managers, IT professionals, auditors and so on. These kinds of certifications can help the professionals to expand their knowledge in DevSecOps and future careers.
Real-time application of DevSecOps
DevSecOps will be significant in the today business world to mitigate the evolving cyber-attacks. By the implementation of the security initiatives in earlier manner, application in the following industries can attain the following benefits:
- Government : The applications managing the highly sensitive data were highly targets for the cyber-attacks. By hardening those applications with a security first-development approach can help in reduction of the cyber-attacks.
- Healthcare : The DevSecOps were highly preferred as it satisfies application design in the healthcare sector. As the organization needs to follow the HIPAA, it is clear that a security first approach can minimize the likelihood of patient records becoming exploited or exposed.
- Finance : DevSecOps can help in the development practices in the finance industry. Finance becomes a major target for the hackers and thus the development companies must use the DevSecOps method to limit sensitive data to be accessible to hackers.
What skills required to become DevSecOps Engineer
The DevSecOps engineers require the technical skills of IT professionals and knowledge on DevOps. They must also require in-depth knowledge of cybersecurity such as knowing the latest trends and threats.
And some of the major skills that are required such as:
- Clear understanding of DevOps principles and culture
- Strong communication and teamwork skills
- Good understanding of risk assessment techniques as well as threat modeling
- Up-to-date information on cybersecurity threats, best practices
- Working knowledge of DevOps and DevSecOps tools such as Ansible, chef, Aqua, Puppet and Kubernetes.
Summary
Hope this blog provides key insights of DevSecOps methodology and its key features, working, applications etc. However, you must be familiar with DevOps before diving into DevSecOps.
Finally, DevSecOps is an approach that aims to integrate security into the DevOps process, ensuring that development and operations teams can work together seamlessly while ensuring that the applications and systems being developed are secure and compliant.
The DevSecOps approach can lead organizations to build a strong security foundation and also help in achieving compliance regulations in a timely manner.
If you have further queries or doubts on this post, please feel free to comment us!
- How to make highly available websites with the usage of AWS Global Infrastructure? - May 18, 2023
- Top Cybersecurity Certifications for Beginners - May 8, 2023
- How to prepare for MS-700: Managing Microsoft Teams? - April 5, 2023
- Examining the future of cybersecurity and importance of SC-100 certification - March 27, 2023
- Preparation Guide on Certified Information System Security Professional(CISSP) Exam - February 17, 2023
- Preparation Guide on SC-900: Microsoft Security, Compliance, and Identity Fundamentals Exam - February 6, 2023
- What is Devsecops? - January 30, 2023
- Preparation Guide on CompTIA A+ 220-1102 (Core 2) - January 27, 2023