The fast pace of the technology industry is driving software development companies to find new work models. Developers need to increase the delivery speed and agility of their workflow. Adopting DevOps pipelines enables organizations to overcome this challenge.
DevOps is a software development approach that focuses on collaboration between development and operations teams. The goal of DevOps is to streamline processes and deploy products faster.
Managing security risks in a DevOps environment can be challenging. Factors such as configuration changes make this task especially difficult. Compliance requirements and code vulnerabilities also make a DevOps environment vulnerable.
Preparing to become a certified DevOps professional? Check our DevOps Certifications Training Courses now!
The solution to this issue lies in integrating security practices and testing to the DevOps pipeline. This new approach is called DevSecOps, and it requires automating the testing for vulnerabilities. Read on to learn more about vulnerability management for DevOps.
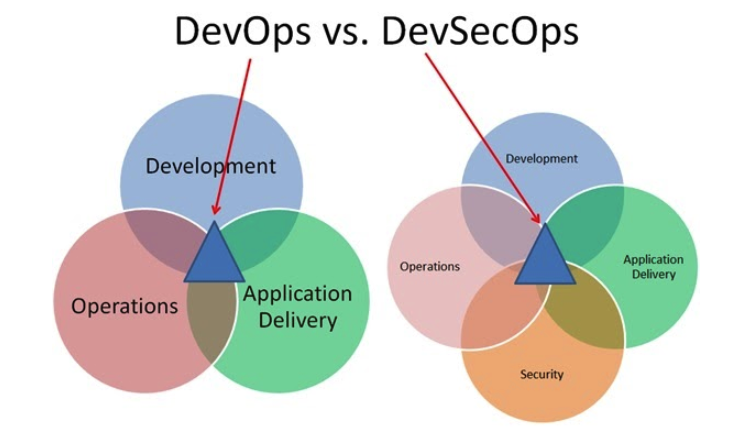
DevOps and DevSecops: An Overview
DevOps is a software development model that aims to improve the communication and collaboration between the development and operations of business units by applying agile methodology practices. The key feature of a DevOps culture is to deploy software into production quickly, fixing flaws and mistakes on-the-go.
At the core of the DevOps approach lie two methods: Continuous Integration and Continuous Delivery (CI/CD). Continuous integration means developers commit code to a central repository at given times, testing the code as they build it. This prevents integration issues. Continuous delivery gets all changes into production safely and quickly.
The goal of CI/CD is to streamline deployments into activities that can be performed on demand. To achieve this, the DevOps process includes automation, which ensures the code is ready for deployment.
Security was not included in the original DevOps approach. The clash between traditional security models with the new agile methodology produced challenges, such as stalled processes. These challenges were addressed by integrating security practices and protocols into the DevOps approach, creating the DevSecOps model.
The DevSecOps model enables developers to practice a test-driven development approach, ensuring that the code is functional before advancing to the next stage. A DevSecOps environment tests for security across the pipeline, avoiding the bottleneck effect of previous security models.
DevSecOps integrates security practices into the DevOps process by creating a culture of Security as Code. Security as Code policies integrate security protocols and testing into DevOps practices and tools, making them an integral part of the workflow. You can achieve a Security as Code culture by documenting how your team introduces changes into the code. The team can then use this mapping to place the security checks and tests on the pipeline.
DevSecOps integrates two seemingly opposite goals into a single process—delivering code fast and producing secure code. Security teams can no longer be blamed for slowing down the delivery cycle, because security was shifted left and integrated seamlessly into the workflow. Now, when the team finds a security flaw, it can be handled immediately to prevent incidents.
Must Read: Top 10 Automation Testing Tools
What Is Vulnerability Management?
The term vulnerability management refers to a set of security practices designed to prevent and mitigate the exploitation of the vulnerabilities of a system. Vulnerability management involves several steps, including detection, remediation, and mitigation.
Organizations use specialized software to scan for vulnerabilities in their systems and applications. The system identifies vulnerabilities that can be exploited by an attacker, such as insecure configurations and code flaws. Cloud environments require vulnerability scanning that provides visibility in real-time. These tools can detect vulnerability status, and detect unapproved changes.
Adding Vulnerability Monitoring to the DevOps Pipeline
Continuous monitoring is a key concept of the DevSecOps approach. A DevSecOps team uses automation tools that monitor a number of categories on a development lifecycle. For example, the team can test if an application is meeting development milestones, such as functions planning or UI/UX design.
If you prefer the DevOps model, you can still improve your security posture through the use of automated vulnerability monitoring. Often, these systems don’t require much effort on your part and provide quick and fast implementation. The goal is to enable you to check for vulnerabilities in your application without interrupting the flow of delivery. These systems to that by looking for two main types of vulnerabilities:
- Known vulnerabilities—these vulnerabilities are public knowledge. Some organizations such as the National Vulnerability Database (NVD), maintain an updated list helping organizations to keep track of their appearance in their products.
- Top-level code vulnerabilities—such as SQL injections, these vulnerabilities usually appear as a result of insecure coding practices. These vulnerabilities are considered critical because they enable attackers to take control of the applications and servers.
You should monitor your application for configuration changes. This will enable you to have a baseline of what your application development should look like. However, achieving a status of continuous monitoring requires the automation of vulnerability scans that historically have run only on a set schedule. Automation prevents human errors and time gaps between scans, effectively monitoring the development process.
Applying continuous monitoring practices for vulnerability scanning can enhance your vulnerability management program, keeping your pipeline constantly under surveillance. It will help you detect vulnerabilities earlier, and determine the effectiveness of your remediation practices.
Kubernetes certifications are among the top 5 DevOps certifications. Read our previous blog to know about Top DevOps Certifications.
Vulnerability Management for DevSecOps
For security purposes, it is important to integrate vulnerability management before the application goes into production. A DevSecOps model involves testing for vulnerabilities across the development and integration pipeline and again once the software is sent to production. This helps security teams patch flaws on time and prevent exploits.
Security teams need to detect and manage vulnerabilities in a number of categories across the development process. They should search for vulnerabilities that may be present in code, containers and in the cloud. The following explains why it is critical to verify vulnerabilities present in these three categories:
- Vulnerability management in code—code scans analyze the code to detect specific vulnerabilities early in the software development lifecycle (SDLC). Developers can use vulnerability scans to ensure the code they are writing is secure before committing it.
- Vulnerability management in containers—containers require scanning before deployment. You should ensure that container vulnerabilities assessment is part of your automated toolchain.
- Vulnerability management in the cloud—cloud services usually have strong security policies in place that ensure they provide secure hosting. Organizations should monitor the cloud platform policy configurations continuously to prevent policy violations such as credential misuse or theft.
Automated Vulnerability Management
The key to automating vulnerability detection is introducing security at the source. This means scanning applications while they run in production to detect vulnerabilities in the source code. This type of security testing tool is called a Dynamic Application Security Testing (DAST). DAST can help you detect configuration flaws, as well as architectural weaknesses.
Pros and cons of DAST tests:
- Pros—the scanners simulate an attack by probing the application with the goal to identify a discrepancy from the result set. DAST tests can scan for vulnerabilities without depending on the language the application is written.
- Cons—since the tool performs dynamic testing, it doesn’t cover the entirety of the application’s source code. In addition, the tool performs the testing according to a predefined list of attacks, covering a limited number of variations for a particular vulnerability.
Wrap Up
Testing the security of web applications is an essential part of cyber security. According to a report from 2019, the majority of application vulnerabilities are in the source code. This finding is in line with DevSecOps practices, which place importance on introducing security scans early in the software development lifecycle.
Automated monitoring can also benefit DevOps pipelines, without impacting the speed of delivery. With automated vulnerability testing, you can produce secure code from the start. When you combine dynamic application security testing with a continuous monitoring process, you can detect security vulnerabilities, and respond in time to avoid a breach. The result is an efficient and secure development process.
If you are a DevOps professional and want to validate your skills, it’s the right time to go for a DevOps certification. Check out our DevOps certification training courses and prepare yourself to become a certified DevOps professional.
- Top 10 Highest Paying Cloud Certifications in 2024 - March 1, 2023
- 12 AWS Certifications – Which One Should I Choose? - February 22, 2023
- 11 Kubernetes Security Best Practices you should follow in 2024 - May 30, 2022
- How to run Kubernetes on AWS – A detailed Guide! - May 30, 2022
- Free questions on CompTIA Network+ (N10-008) Certification Exam - April 13, 2022
- 30 Free Questions on Microsoft Azure AI Fundamentals (AI-900) - March 25, 2022
- How to Integrate Jenkins with GitHub? - March 22, 2022
- How to Create CI/CD Pipeline Inside Jenkins ? - March 22, 2022