So, how’s your preparation going on for AWS Certified Security Specialty exam? Have you prepared yourself with Infrastructure Security domain, that has maximum weight i.e. 26% in the blueprint of AWS Security Specialty exam? Here we cover the topic “How to set right Inbound and Outbound rules for security groups and network access control lists?” that addresses the Infrastructure Security domain as highlighted in the AWS Blueprint for the exam guide. So, this article is an invaluable resource in your AWS Certified Security Specialty exam preparation.
For the 24*7 security of the VPC resources, it is recommended to use Security Groups and Network Access Control Lists. AWS NACLs act as a firewall for the associated subnets and control both the inbound and outbound traffic. So, it becomes very important to understand what are the right and most secure rules to be used for Security Groups and Network Access Control Lists (NACLs) for EC2 Instances in AWS. Let’s take a use case scenario to understand the problem and thus find the most effective solution.
Problem Statement
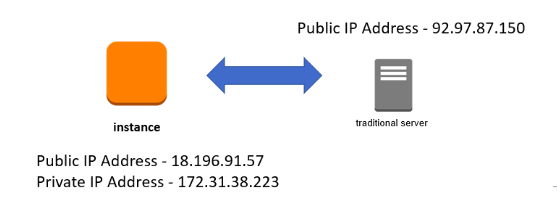
As a Security Engineer, you need to design the Security Group and Network Access Control Lists rules for an EC2 Instance hosted in a public subnet in a Virtual Private Cloud (VPC). The instance needs to be accessed securely from an on-premise machine. The on-premise machine just needs to SSH into the Instance on port 22.
The networking details are given below
- IP Address of the On-premise machine – 92.97.87.150
- Public IP address of EC2 Instance – 18.196.91.57
- Private IP address of EC2 Instance – 172.31.38.223
Which of the following is the right set of rules which ensures a higher level of security for the connection? While determining the most secure and effective set of rules, you also need to ensure that the least number of rules are applied overall.
Also Read: How to improve connectivity and secure your VPC resources?
Solution: Set Right Inbound & Outbound Rules for Security Groups and Network Access Control Lists
If we visualize the architecture, this is what it looks like:
- Now the first point we need to consider is that we need not bother about the private IP address of the Instance since we are accessing the instance over the Internet
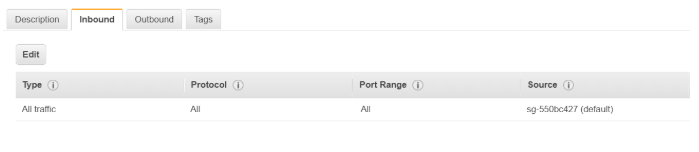
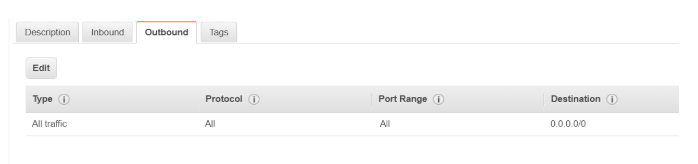
Now let’s look at the default security groups available for an Instance:
Now to change the rules, we need to understand the following
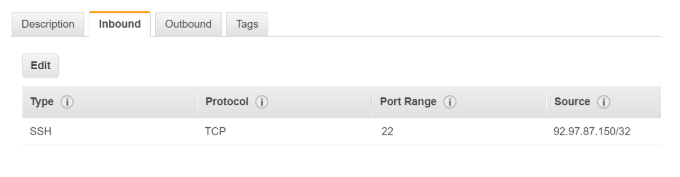
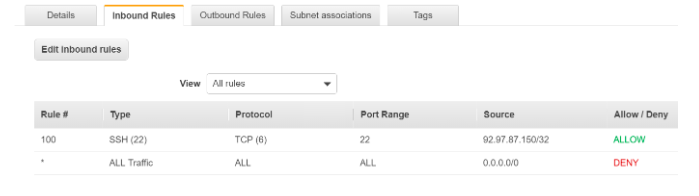
- The On-premise machine needs to make a connection on port 22 to the EC2 Instance. So, the incoming rules need to have one for port 22.
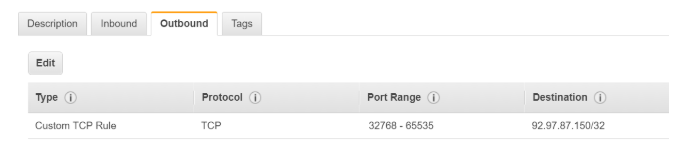
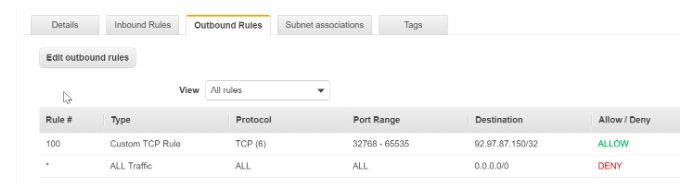
- Now, since SSH is a stateless protocol, we also need to ensure that there is a relevant Outbound rule. The EC2 Instance would connect to the on-premise machine on an ephemeral port (32768 – 65535)
- And here the source and destination is the on-premise machine with an IP address of 92.97.87.150
Hence, the rules which would need to be in place are as shown below:
Now, we need to apply the same reasoning to NACLs.
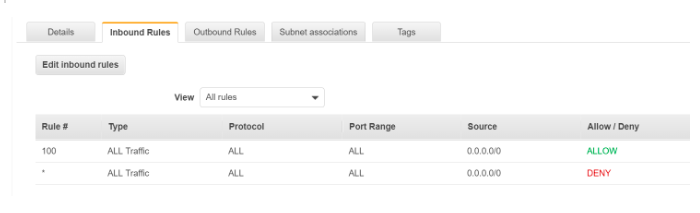
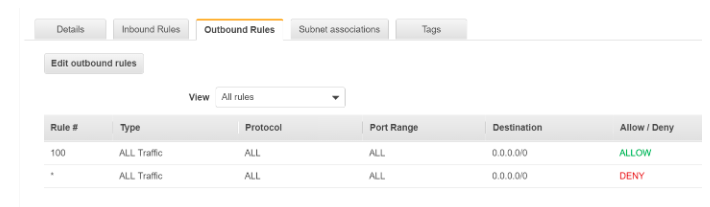
Let’s have a look at the default NACLs for a subnet:
Let us apply below-mentioned rules to NACL to address the problem.
- Allow incoming traffic on port 22 and outgoing on ephemeral ports (32768 – 65535).
- Allow source and destination as the public IP of the on-premise workstation for inbound & outbound settings respectively.
We would have below rules for NACL:
Other Related Resources:
How to Use a Central CloudTrail S3 Bucket for Multiple AWS Accounts?
Working with IAM and Bucket Policies
How to Grant Access to AWS Resources to the Third Party via Roles & External Id?
Summary
- Consider the source and destination of the traffic.
- Consider both the Inbound and Outbound Rules.
- Always consider the most restrictive rules, it’s the best practice to apply the principle of least privilege while configuring Security Groups & NACL.
- And set right inbound and outbound rules for Security Groups and Network Access Control Lists.
So, here we’ve covered how you can set right inbound and outbound rules for Security Groups and Network Access Control Lists. Getting prepared with this topic will bring your AWS Certified Security Specialty exam preparation to the next level. If you think yourself fully prepared for the exam, give your preparation a check with AWS Certified Security Specialty Practice Tests. The Whizlabs practice test series comes with a detailed explanation to every question and thus help you find your weak areas and work on that.
So, join us today and enter into the world of great success!
- Top 20 Questions To Prepare For Certified Kubernetes Administrator Exam - August 16, 2024
- 10 AWS Services to Master for the AWS Developer Associate Exam - August 14, 2024
- Exam Tips for AWS Machine Learning Specialty Certification - August 7, 2024
- Best 15+ AWS Developer Associate hands-on labs in 2024 - July 24, 2024
- Containers vs Virtual Machines: Differences You Should Know - June 24, 2024
- Databricks Launched World’s Most Capable Large Language Model (LLM) - April 26, 2024
- What are the storage options available in Microsoft Azure? - March 14, 2024
- User’s Guide to Getting Started with Google Kubernetes Engine - March 1, 2024


Security Group Outbound Rule is not required.
Hi Vijay,
Thanks for your comment. Yes, your analysis is correct that by default, the security group allows all the outbound traffic. So we no need to modify outbound rules explicitly to allow the outbound traffic. But here, based on the requirement, we have specified IP addresses i.e 92.97.87.150 should be allowed. So we no need to go with the default settings.