This blog post is about Information Protection Administrator SC-400 exam questions that covers domains on implementing and managing Microsoft’s information protection solutions, data loss prevention & data governance.
Here are our newly updated 10+ Free questions on the Information Protection Administrator exam which are very similar to the SC-400 practice test as well as the real exam.
Also, note that the exam syllabus covers questions from the following domains:
- Domain 1: Implement information protection (35—40%)
- Domain 2: Implement data loss prevention (30—35%)
- Domain 3: Implement information governance (25—30%)
Let’s get started!
Domain 1: Implement Information Protection
Q1. In Whizlabs organization, the information protection team is tasked to implement an information and governance solution for Whizlabs organization, the team is newly starting their journey, whatever approach the team uses, will involve people, processes, and technology. From a process perspective, there are some major phases that the information team should follow for a successful implementation.
Arrange these phases in the correct order from the following options:
A. Define the data classification taxonomy🡪Define classification policy conditions 🡪 Create, test, and deploy the labels and policy settings 🡪 Ongoing usage, monitoring and remediation
B. Define classification policy conditions 🡪 Create, test, and deploy the labels and policy settings 🡪 Ongoing usage, monitoring and remediation 🡪 Define the data classification taxonomy
C. Define the data classification taxonomy🡪Define classification policy conditions 🡪 Ongoing usage, monitoring and remediation 🡪 Create, test, and deploy the labels and policy settings
D. Define the data classification taxonomy🡪 Create, test, and deploy the labels and policy settings 🡪 Ongoing usage, monitoring and remediation 🡪Define classification policy conditions
Answer: A
Option A is correct because, From a process perspective, here are the major phases you should follow for a successful implementation.
- Define the data classification taxonomy. The data classification taxonomy ends up as sensitivity and retention labels that will be applied to your content. These labels may surface in productivity applications, SharePoint Online sites, Microsoft Teams workspaces, and Exchange emails. They may be applied manually by users or automatically by Microsoft 365.
- Define classification policy conditions. Once you have built your taxonomy, you need to determine how you are going to find and classify the data in your environment and map it to the taxonomy.
- Create, test, and deploy the labels and policy settings. Once you determine the methods you will use to protect and govern your data, it is important to test everything thoroughly prior to deploying your configuration across the organization.
- Ongoing usage, monitoring and remediation. It is important to understand how data classification is being used and to ensure your policies are accurate and achieve the desired results.
Option B is incorrect because it is incorrect order as the process starts with a step “Define the data classification taxonomy” and not with “Define classification policy conditions”
Option C is incorrect because it is incorrect order as “ongoing usage, monitoring and remediation” should be done after the “create, test, and deploy the labels and policy settings” step.
Option D is incorrect because it is in incorrect order as the “Define classification policy conditions” step should be performed after the first step i.e., “Define the data classification taxonomy” and not as the last step.
Reference: To learn more, refer to this Microsoft documentation at https://docs.microsoft.com/en-us/learn/modules/m365-compliance-information-governance/introduction?ns-enrollment-type=LearningPath&ns-enrollment-id=learn.wwl.implement-information-protection
Domain 1: Implement Information Protection
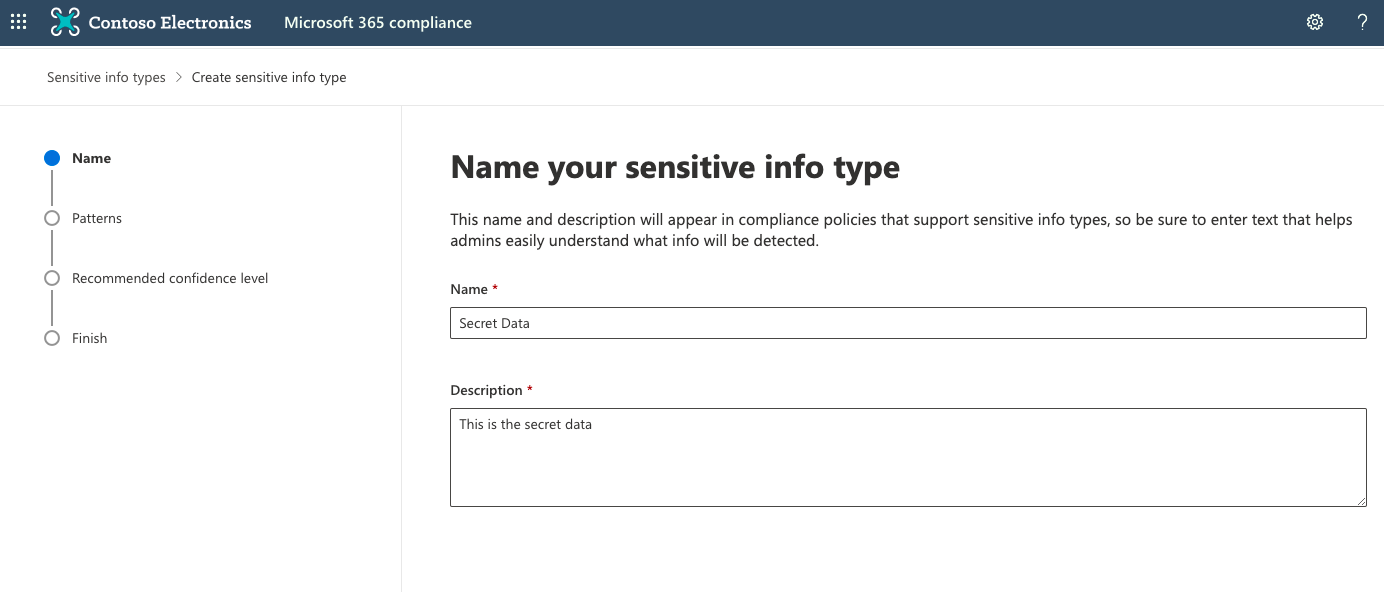
Q2. Which of the following are not the parts of Sensitive Information Type?
A . Primary pattern
B. Additional checks
C. Character proximity
D. Confidence level
E. Character length
Answer: E
Option A is incorrect because it is a part of the sensitive information type (shown in the screenshot) as, Primary pattern helps to search patterns for detection, consisting of keywords or regular expressions.
Option B is incorrect because it is a part of sensitive information type (shown in the screenshot) as Additional checks is a second search pattern for higher matching accuracy of the primary pattern, consisting of keywords.
Option C is incorrect because it is a part of sensitive information type (shown in the screenshot) as Character Proximity is used as a detection window in characters of primary patterns and additional evidence.
Option D is incorrect because it is a part of the sensitive information type (shown in the screenshot) as Confidence level is a supporting level of pattern and evidence matching accuracy.
Option E is correct because the character length component does not exist in the sensitive information types.
Reference: To learn more refer to this Microsoft documentation at https://docs.microsoft.com/en-us/microsoft-365/compliance/sensitive-information-type-learn-about?view=o365-worldwide
Domain 1: Implement Information Protection
Q3. Whizlabs is having an amount of sensitive data to be protected. So, the compliance administrator is tasked with applying sensitive data controls and investigating suspicious activity in the organization’s data. What are the steps a compliance administrator should follow to accomplish the task?
A. Detect sensitive information
B. Apply controls
C. Investigate suspicious activities
D. Create policies
E. Create Alerts
Answers: A,B,C
Option A is correct because it is the first step for applying sensitive data controls and investigating suspicious activity in the organization’s data
Option B is correct because it is the second step for applying sensitive data controls and investigating suspicious activity in the organization’s data
Option C is correct because it is the last step for applying sensitive data controls and investigating suspicious activity in the organization’s data
Option D is incorrect because it is not a part of the process of given task accomplishment
Option E is incorrect because it is not a part of the process of given task accomplishment as the compliance administrator is not tasked to create alerts.
To learn more, visit this link https://aka.ms/AAbfsel and microsoft documentation link
Case Study: Q.4 to Q.5
In Whizlabs organization, the information protection team is tasked to protect the organization’s sensitive data with Microsoft information protection which can help the team to discover sensitive and business-critical content across the organization, classify information, and protect content whenever it stays at the location or travels to another location.
Now, by using this solution, a compliance administrator from the team has created a sensitivity information type named “Secret Data” adding the pattern with keyword list as a primary and supporting element. (shown in the screenshot).
From the Information Protection menu in the compliance center, a compliance administrator added one sub-label named “Highly Secret Data” as shown in the screenshot. This label will now detect sensitive information related to highly confidential data and suggest appropriate labeling to the end-user.
Domain 1: Implement Information Protection
Q 4. After this label is created, it won’t be available for use until a policy is created to either publish or auto-apply it. Is this correct?
A. Yes
B. No
Answer: Yes
Option A is correct because, whenever a label is created, we cannot use it until we publish or auto-apply it and when we start to publish the created label, we will be asked to create the policy for the label during the process.
Option B is incorrect because we cannot use the label before publishing the created label.
Domain 1: Implement Information Protection
Q.5 The first step in creating a label policy is to publish the label.
A. True
B. False
Answer: True
Option A is correct because, when the compliance administrator starts the process of publishing the label then automatically it will redirect to the process of creating the label policy.
Option B is incorrect because the given statement is true, i.e., the first step in creating a label policy is to publish the label.
Domain 2: Implement Data Loss Prevention
Q.6 In Whizlabs organization, the compliance administrator is tasked with configuring data loss prevention for endpoints in your organization. Endpoint Data Loss Prevention settings create a framework in which Endpoint Data Loss Prevention policies work; a compliance administrator wants to limit where you can work with protected files. Which of the following settings, a compliance administrator explore to accomplish the task?
A. File path exclusions
B. Unallowed apps
C. Unallowed Browsers/Service Domains
D. Advanced classification scanning and protection
Answer: B
Option A is incorrect because File path exclusions are applied to all Endpoint DLP policies and allow you to limit where your policies are in effect.
Option B is Correct because Unallowed apps are applied when a policy blocks unallowed apps and allows you to limit where you can work with protected files.
Option A is incorrect because Unallowed Browsers/Service Domains are applied when a policy blocks unallowed browsers and allows you to limit where you can share protected files.
Option D is incorrect because advanced classification scanning and protection can use Exact Data Match and named entities in your Data Loss Prevention policies.
https://docs.microsoft.com/en-us/microsoft-365/compliance/endpoint-dlp-using?view=o365-worldwide
Domain 2: Implement Data Loss Prevention
Q.7 The information protection team wants to get overview of Data Loss Prevention violations from Data Loss Prevention reports which includes Data Loss Prevention policy matches, Data Loss Prevention incidents, and Data Loss Prevention false positives and user overrides reports. All these are used to fine-tune your policies and identify configurations. The team needs this reports quickly within 5-10 mins, is it possible to get these reports?
A. Yes
B. No
Answer: No
Option A is incorrect because DLP Reports which provides an overview of DLP violations can take up to 24 hours to update, hence it is not possible to get the reports in 5-10minutes.
Option B is correct because, for getting an update on the requested reports can take up to 24 hours.
Reference: https://docs.microsoft.com/en-us/microsoft-365/compliance/view-the-dlp-reports?view=o365-worldwide
Domain 2: Implement Data Loss Prevention
Q 8. Which of the following, the information protection team should use to get individual alerts to provide a deeper insight into Data Loss Prevention violations?
A. Data Loss Prevention Reports
B. Data Loss Prevention Alerts Dashboard
C. Microsoft Defender for Cloud Apps Dashboard
D. Azure Portal
Answer: B
Explanation:
Option A is incorrect because, Data Loss Prevention Reports provides an overview of DLP violations
Option B is Correct because, Data Loss Prevention alerts Dashboard provides a deeper insight into Data Loss Prevention violations, displays individual alerts and can aggregate alerts to spot patterns more easily
Option C is incorrect because Microsoft Defender for Cloud Apps Dashboard displays alerts of Defender for Cloud file policies and shows alerts of all your Defender for Cloud DLP policies
Option D is incorrect because the information protection team can not access insights of data loss prevention policies from Azure portal directly.
Reference : To learn more about data loss prevention alerts dashboard, visit here https://docs.microsoft.com/en-us/microsoft-365/compliance/dlp-alerts-dashboard-get-started?view=o365-worldwide
Domain 3: Implement Information Governance
Q 9: The information protection team has created a retention label for email and documents in the library for 6 years and published it. The published label will be available at the location where it has been published by the team which is to be assigned manually, which of the following locations the label can be applied?
A. Exchange mail
B. SharePoint sites
C. OneDrive accounts
D. Microsoft 365 Groups
E. Skype for Business,
F. Teams and Yammer
Answer: A, B, C, and D
Option A is correct because, Exchange mail support retention labels
Option B is correct because SharePoint sites, support retention labels
Option C is correct because OneDrive accounts, support retention labels
Option D is correct because Microsoft 365 Groups support retention labels
Option E is incorrect because Skype for Business does not support retention labels.
Option F is incorrect because Teams and Yammer messages do not support labels.
retention labels
Domain 3: Implement Information Governance
Q 10: You have a requirement in your organization to create a file plan to group the creation of labels, auto-apply label policies, and additional metadata tags together in records management. Which of the following steps do you need to follow to achieve the requirement?
A. Create a retention label and specify the retention period in the retention settings and publish the label to use.
B. Create a retention label and specify the retention period in the retention settings and publish the label. Then, use export file plans as CSV files and import them into other tenants
C. Create a retention label and do nothing
D. Create a retention label and specify the retention period in the retention settings and publish the label. Then, use export file plans as CSV files and import them into other tenants and use trainable classifiers to identify content it should match.
Answer: D
Option A is incorrect because the process of file plan creation given in this option in incomplete.
Option B is incorrect because, this answer is incomplete.
Option C is incorrect because it is an incomplete answer.
Option D is correct because this is the correct process to create a file plan.
Reference: To know more about the steps followed in this process, visit here https://docs.microsoft.com/en-us/microsoft-365/compliance/file-plan-manager?view=o365-worldwide
Domain 3: Implement Information Governance
Q.11 You are tasked to create a new custom OME configuration and create a transport rule to apply the OME configuration to all mails sent from the finance department of your organization. To create a new OME configuration, which of the following PowerShell commands should you use?
A. New-OMEConfiguration -Identity “finance department”
B. Set-OMEConfiguration -Identity “finance department”
C. Install-Module ExchangeOnlineManagement
D. Neither A nor B
Answer: A
Option A is correct because, to create a new OME configuration New-OMEConfiguration -Identity “finance department” is used.
Option B is incorrect because, Set-OMEConfiguration -Identity “finance department” Is used to change the execution policy.
Option C is incorrect because Install-Module ExchangeOnlineManagement is used to install the latest Exchange Online PowerShell module version.
Option D is incorrect because, New-OMEConfiguration -Identity “finance department” is used to create the new OME configuration.
Reference: refer to this link for the same https://github.com/MicrosoftLearning/SC-400T00A-Microsoft-Information-Protection-Administrator/blob/master/Instructions/Labs/LAB_AK_01_Lab1_Ex2_message_encryption.md
Summary
The Information Protection Administrator Certification is the advanced level of certification offered by Microsoft which is intended for experienced professionals. We hope the above list of SC-400 exam questions on Microsoft Information Protection Administrator are helpful for you to prepare.
It is strongly recommended to ensure that we have covered all the objectives of the certification exam, so that you can pass the exam at ease and in your first attempt. Hence, keep practicing until you are confident to take the real exams. You can also try Whizlabs newly updated SC-400 practice test on Microsoft Information Protection Administrator exam.
- 7 Pro Tips for Managing and Reducing Datadog Costs - June 24, 2024
- Become an NVIDIA Certified Associate in Generative AI and LLMs - June 12, 2024
- What is Azure Data Factory? - June 5, 2024
- An Introduction to Databricks Apache Spark - May 24, 2024
- What is Microsoft Fabric? - May 16, 2024
- Which Kubernetes Certification is Right for You? - April 10, 2024
- Top 5 Topics to Prepare for the CKA Certification Exam - April 8, 2024
- 7 Databricks Certifications: Which One Should I Choose? - April 8, 2024