This blog post is about Microsoft Cybersecurity Architect SC-100 exam questions that covers domains on developing and refining cutting-edge cybersecurity strategies to safeguard organizational objectives and business operations.
This exam is designed for cybersecurity professionals who are looking to advance their skills and knowledge in the field. The exam tests a candidate’s ability to design, implement, and manage secure solutions in a Microsoft environment.
Latest update:
This SC-100 Microsoft Cybersecurity Architect certificate will be retiring in Indonesian, Arabic, and Russian languages on Feb 28, 2023.
What does Microsoft Cybersecurity Architect Do?
After completing the Microsoft cybersecurity architect certification he/she will play the role of designing and implementing the security strategy inside the organization to protect the organization’s mission and business architecture.
This cybersecurity architect will build the zero trust strategy including the organization’s data, applications, identity and access management, etc.
He/she conducts the risk assessment to identify if there is any security threat to the organization. And also work closely with the team lead and practitioner in IT security, privacy, and other roles inside the organization to build a cybersecurity strategy.
In this post, we will be providing free SC-100 practice questions to help you prepare for the exam and gain a better understanding of the types of questions you will encounter on the test. So, whether you’re a cybersecurity professional looking to advance your career or just starting out in the field, this post is for you.
Exam Preparation Guide on SC-100: Microsoft Cybersecurity Architect
Let’s dive in and take a closer look at the SC-100 exam and the types of questions you’ll need to know to pass it.
Also, note that the exam syllabus covers questions from the following domains:
| Domains | Weightage |
| Designing solutions that align with best security practices and priorities | 20-25% |
| Designing security operations, identity, and compliance capabilities | 30-35% |
| Designing security for infrastructure | 20-25% |
| Designing a strategy for data and applications | 20-25% |
Let’s get started!
New Updates
Domain: Design a strategy for data and applications
Question 1 : You’re implementing a data encryption policy in your organization for data at rest. As part of the policy, you must be able to rotate keys every two months.
For the Azure SQL Managed Instance, you recommend Transport Data Encryption and Azure key vault that uses customer manage keys. Will this meet your objective? True or False.
A. True
B. False
Answer: A
The statement is true because Transport Data Encryption is a feature in Azure SQL Managed Instance, and with Azure Key Vault, you would have control over how often you rotate your keys.
Reference
Domain: Design a Zero Trust strategy and architecture
Question 2 : You have an Azure subscription, and your organization recently purchased another company with an Azure subscription.
Your company has compliance and regulatory standards that it needs to adhere to. With this recent acquisition, you must review that the Azure subscription’s new entity complies with your standards.
What should you initiate first?
- Onboard the Azure subscription in Microsoft Defender for Cloud and enable the regulatory requirements you need.
- From Microsoft Sentinel, configure the Microsoft Defender for Cloud data connector.
- Review Azure security baseline for the audit report.
- From Microsoft Defender for Cloud Apps, create an access policy for cloud applications.
Answer: A
Option A is correct because once you onboard the subscription you would have the ability to add the required regulatory standard and then you would be able to evaluate the new Azure Subscription.
Option B is incorrect because you don’t need Microsoft Sentinel to evaluate an Azure subscription with a cloud data connector.
Option C is incorrect because if you have not onboarded the Azure subscription Microsoft Defender for Cloud would not be able to evaluate it. Furthermore, you must enable the regulatory standard that is needed for your organization in order for it to be evaluated after onboarding the subscription.
Option D is incorrect because Microsoft Defender for Cloud apps is a Cloud Access Security agent and does not have the feature to identify regulatory standards.
Reference:
https://learn.microsoft.com/en-us/azure/defender-for-cloud/update-regulatory-compliance-packages
Domain: Design a Zero Trust strategy and architecture
Question 3 : Which Azure security solution can you use in a multi-cloud environment with Microsoft Defender for Cloud without onboarding the resources in Azure Arc resources? (Select TWO)
A Microsoft Defender for Containers
B Microsoft Defender for Servers
C Azure Active Directory Privileged Identity Management (PIM)
D Azure Policy
Answer: C and D
Option A is incorrect because you would need ARC to onboard the multi-cloud containers in Azure Defender for Cloud and as instructed Microsoft ARC should not be used.
Option B is incorrect because you would Need ARC to onboard the multi-cloud servers.
Option C is correct because you do not need Arc, once you add the multi-cloud resources account to Microsoft Defender for Cloud Azure Active Directory (Azure AD) Privileged Identity Management (PIM) is supported.
Option D is correct because Azure policy is a common rule engine that integrates with Active Directory.
Reference:
https://docs.microsoft.com/en-us/azure/defender-for-cloud/quickstart-onboard-aws?pivots=env-settings
https://docs.microsoft.com/en-us/azure/defender-for-cloud/defender-for-containers-introduction
Domain: Design a Zero Trust strategy and architecture
Question 4: Your organization develops an e-commerce application in its on-premise environment. The application was developed in JavaScript and used a MongoDB database.
Your organization plan to migrate the entire solution to Azure.
- The web app will be migrated to Azure App Services
- The MongoDB database will be migrated to Azure Cosmos DB
You must provide a solution that securely connects the web app and the Azure Cosmos DB.
The solution must take into consideration the zero-trust methodology.
You recommend implementing a private endpoint to the Azure App Server web application and the Azure Cosmos DB database. Does this meet the objective? True or False.
A. True
B. False
Answer: A
You can utilize a Private Endpoint for your Azure Web App to enable clients in your private network to access the app across Private Link easily.
This solution uses an IP address from your Azure VNet address space, the network traffic traversing the private network, and the web app passes through the private link on the Microsoft backbone network, eliminating the need to cross the public Internet.
Reference:
Connect privately to an Azure Web App using Private Endpoint | Microsoft Learn
Domain: Design a strategy for data and applications
Question 5 : You are a security architect for an organization. You recently were affected by a cyber security incident. The Incident stems from an unauthorized application on one of your servers running in Azure.
You enable Microsoft Defender for Cloud. What specific feature can help mitigate future threats?
A. Adaptive application controls in Defender for Cloud
B. Azure Blueprints
C. App discovery anomaly detection policies in Microsoft Defender for Cloud Apps
D. Azure Policy Business Rules
Answer: A
Option A is correct because adaptive application control is a feature within Microsoft Defender for Cloud that allows you to allow list known to be safe applications on your servers.
Option B is incorrect because Azure Blueprints allows you to outline a repeatable deployments combination of Azure resources that adheres to an organization’s standards, patterns, and requirements, this is focused on the deployment of repeatable patterns that complies with your company standards, for example, role assignment policy assignment but it does not enforce or manage application deployment on your machines.
Option C is incorrect because app discovery anomaly detection policies in Microsoft Defender for Cloud Apps focus on app usage. It provides continuous monitoring of the use of apps in Microsoft 365
Option D is incorrect because Azure Policy Business rules assess resources in Azure by means of evaluating the properties of those resources to business rules. The business rules, defined in JSON format, are established policy definitions, and this will not meet the objective as this is a resource-level assessment, not an application-level one.
References:
https://docs.microsoft.com/en-us/azure/defender-for-cloud/adaptive-application-controls
https://docs.microsoft.com/en-us/mem/intune/apps/app-protection-policy
https://docs.microsoft.com/en-us/defender-cloud-apps/cloud-discovery-anomaly-detection-policy
https://docs.microsoft.com/en-us/security/benchmark/azure/overview
Old Questions
Domain : Design security for infrastructure
Question 1 : You are a cloud consultant working for an organization. The customer’s environment has Microsoft 365 and Azure subscriptions.
The organization has a mix of Windows, Mac OS, and Android devices.
The devices are deployed with a hybrid strategy using an on-premise data center and Azure.
You must develop a governance strategy to ensure that all the devices adhere to your compliance targets.
What solution should be included in your recommendations?
A. Microsoft Defender for Endpoint
B. Microsoft Sentinel
C. Microsoft Information Protection
D. Microsoft Endpoint Manager
Correct Answer: D
Explanation:
Option A is incorrect because Microsoft Defender for Endpoint is designed to provide enterprise network prevention and detection, and investigation to advanced threats, but not to enforce compliance targets.
Option B is incorrect because Microsoft Sentinel is a security information and event manager (SIEM) cloud platform. It supports organizations in analyzing a large amount of security data.
Option C is incorrect because Microsoft Information Protection, now known as Microsoft Purview Information Protection supports organizations with discovering, classifying and protecting sensitive information, it does not enforce compliance targets.
Option D is correct because Microsoft Endpoint Manager includes a key feature called Microsoft Intune which helps you manage your devices and implement compliance policies.
References: https://docs.microsoft.com/en-us/mem/endpoint-manager-overview, https://docs.microsoft.com/en-us/azure/defender-for-cloud/integration-defender-for-endpoint.
Domain : Design security for infrastructure
Question 2 : You are a security administrator for your organization. You have a mixed environment with Windows 11 and Windows Server 2019.
Your chief information officer has asked for a compliance report with a security baseline for improving the security posture of your device environment.
You decided to use the security baseline from the Microsoft Security Compliance Toolkit.
What solution can you use to equate the baseline to the present device configuration?
A. Microsoft Sentinel
B. Local Group Policy Object (LGPO)
C. Windows Autopilot
D. Policy Analyzer
Correct Answer: D
Explanation:
Option A is incorrect because Microsoft Sentinel is a security information and event manager (SIEM) cloud platform it supports organizations in analyzing a large amount of security data this will not meet the objective
Option B is incorrect because Microsoft’s Local Group Policy Object (LGPO) Utility is a separate tool that helps in automating the management of local security policies that will not meet the objective.
Option C is incorrect because Windows Autopilot administrations set up pre configured devices for deployment, this will not meet the objective
Option D is correct because Policy Analyzer compares group policy objects, it can identify redundant settings and internal inconsistencies which will meet the objective.
Domain : Design a Zero Trust strategy and architecture
Question 3 : You work for an organization as an Azure security Specialist,
The chief information officer has requested you to build a plan to secure SharePoint Online and Microsoft Teams, and they’re on-promise applications the security requirements are listed below.
- Provide real-time monitoring for your on-premise app applications and SaaS.
- Review high-risk users when signing on to applications, and then record their actions from inside the session.
A. Azure AD Conditional Access
B. Access reviews in Azure AD
C. Microsoft Defender for Cloud
D. Microsoft Defender for Cloud Apps and Azure Active Directory
Correct Answer: D
Explanation:
Option A is incorrect because Azure Active Directory (AD) Conditional Access provides security by allowing access to your applications across the cloud and on-premises from trusted devices. It is a policy-based strategy. When you configure a Conditional Access policy with the required conditions to use the access controls, conditions can include device type, users’ attributes, operating systems, client applications accessed over web or cloud apps, network login location, sign-in risks, etc. this will not meet your objective.
Option B is incorrect because Azure Active Directory access reviews help organizations to efficiently control group members, access to enterprise applications, and role tasks. User access can be examined routinely to ensure the right users have continued access.
Option C is incorrect because Microsoft Defender for Cloud is a Cloud Security Posture Management and Cloud Workload Protection Platform (CWPP) for your Azure, on-premises. This includes multi cloud (Amazon AWS and Google GCP) resources. Defender for Cloud meets three critical demands as you deal with the security of your assets and workloads in the Cloud and on-premises, this will not meet your objective.
Option D is correct because the Microsoft Defender for Cloud Apps is used as Cloud Access Security Broker (CASB) this will provide the Provide real-time monitoring for your on-premise app applications and SaaS.
Azure Active Directory can provide the identity management that is required in this scenario.
Domain : Design security for infrastructure
Question 4 : Your Chief Information Officer, Has asked you to develop interactive dashboards that gather information from these different Azure data sources; he would also like the ability to interact with these dashboards.
What tool in Microsoft Defender for Cloud can facilitate this request and can also provide templates to build and modify to your needs?
A. Security Posture Dashboard
B. Security solutions
C. workbooks
D. workflow automation
Correct Answer: C
Explanation:
Option A is incorrect because the Security Posture Dashboard in Microsoft Defender for Cloud’s Dashboard is a collaborative dashboard that delivers a cohesive view of the security posture of your multi-cloud and hybrid cloud workloads. It will not allow you to create custom dashboards; therefore, this will not meet the objective.
Option B is incorrect because Security Solution in Microsoft Defender for Cloud provides you with the ability to integrate with external security solutions a (SIEM) security information event management system, this will not meet your objective in this scenario.
Option C is correct because Workbooks in Microsoft Defender for Cloud deliver the ability to create dashboards with data collected from different Azure resources; it also comes with templates you can build upon or customize for your needs. This solution meets the objective in this scenario.
Option D is incorrect because Workflow automation in Microsoft Azure Defender for Cloud enables organizations to trigger workflows to respond to incidents and events in their environment.
This assists with security personnel overhead as minor events and happenings can be handled by automation; this solution will not meet your objective in this scenario.
Reference: Workbooks gallery in Microsoft Defender for Cloud | Microsoft Learn
Domain : Design security for infrastructure
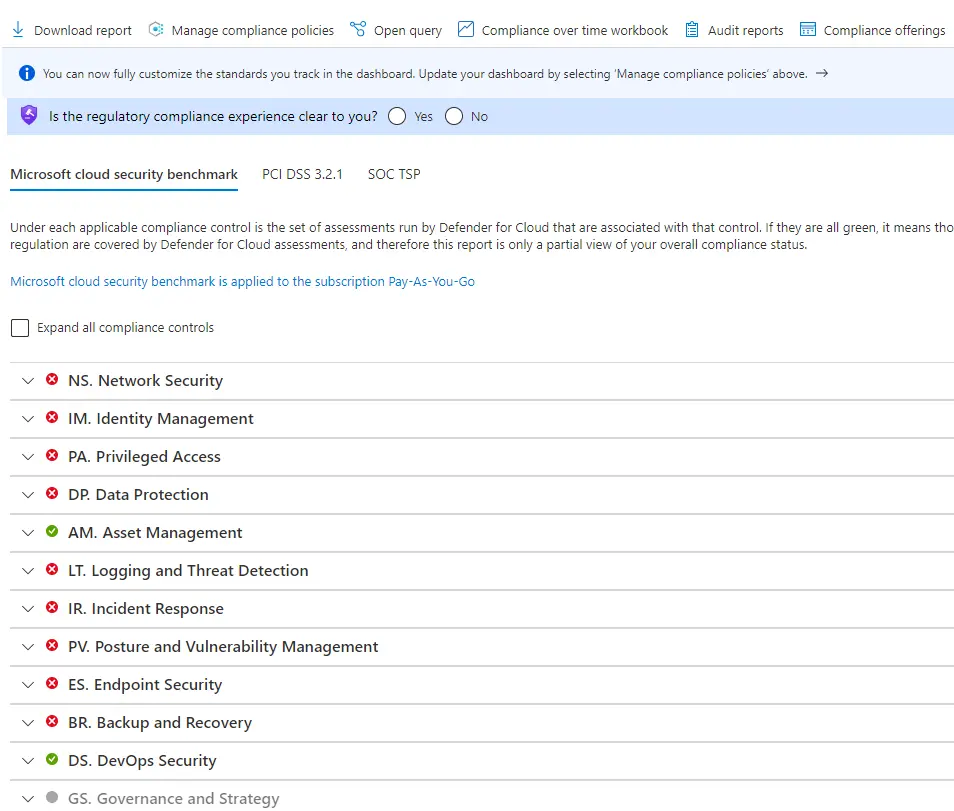
Question 5 : You are managing an Azure subscription. You enable Microsoft Defender for Cloud.
You are assessing the Azure Security Benchmark report as shown in the below exhibit.
You need to confirm whether all Azure subscriptions have e-mail information for all security-related issues. Which compliance control should you evaluate?
A. Asset Management
B. Posture and Vulnerability Management
C. Incident Response
D. Endpoint Security
Correct Answer: C
Explanation:
Option A is incorrect because Asset Management covers controls to guarantee security visibility and governance over Azure resources, including recommendations on authorizations for security personnel, security access to asset inventory, and handling approvals for services and resources (inventory, tracking. This will not meet your objective.
Option B is incorrect because Posture and Vulnerability Management focus on controls for assessing and improving Azure security posture, including vulnerability scanning, penetration testing, and remediation, as well as security configuration tracking, reporting, and correction in Azure resources.
Option C is correct because Incident Response covers controls in the incident response life cycle. You will also be able to verify if the subscriptions have e-mail contact information for security-related issues.
Option D is incorrect because Endpoint Security covers controls in endpoint detection and response, concerning e-mail contact; this will not meet your objective.
Reference: The regulatory compliance dashboard in Microsoft Defender for Cloud | Microsoft Learn
Domain : Evaluate Governance Risk Compliance (GRC) technical strategies and security operations strategies
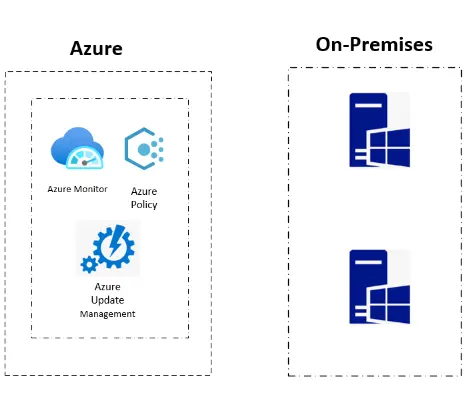
Question 6 : Your company recently invested in a hybrid infrastructure.
Organization data and applications traverse the cloud environment regularly.
The image below shows how the organization’s network is managed.
You are now tasked with designing security operations to support this hybrid environment.
There are two objectives that you must meet which are listed below:
- Provide governance over the virtual servers in the hypervisor and across multiple environments
- Impose standards for all the resources throughout all the environments using Azure Policy.
Please select two answers from below that should be part of the recommendations for the on-premises network.
A. On-premises Power Platform data gateway
B. Microsoft Azure VPN Gateway
C. Guest configuration in Azure Policy
D. Microsoft Azure Arc
Correct Answers: C and D
Explanation:
Option A is incorrect because an On-premises data gateway is designed for Power BI to provide a bridge to access secure data quickly; this will not meet your objective.
Option B is incorrect. An Azure VPN Gateway is used to link your on-premises network to Azure, but it will not provide the governance requirement needed in this scenario.
Option C is correct because Azure Policy’s guest configuration feature delivers the native capability to audit or configure operating system settings as code for machines running in Azure and hybrid Arc-enabled machines. Azure Policy can use this ability directly per machine or at scale orchestrated by Azure Policy.
Option D is correct because Azure Arc is a channel that expands the Azure platform to support you build applications and services with the tractability to run throughout data centers, at the edge, and in multi-cloud environments.
References: https://techcommunity.microsoft.com/t5/azure-developer-community-blog/azure-arc-for-servers-getting-started/ba-p/1262062, https://docs.microsoft.com/en-us/azure/cloud-adoption-framework/manage/hybrid/server/best-practices/arc-policies-mma, https://docs.microsoft.com/en-us/azure/governance/policy/concepts/guest-configuration
Domain : Design security for infrastructure
Question 7 : Your organization has an Azure Subscription that consumes Azure Storage.
The company intends to distribute specific Azure BLOB storage with external vendors.
You need to advise a solution to provide the external vendors with secure access to specific Azure BLOB storage without exposing the blobs publicly.
The access must be time controlled.
What should you include as a solution?
A. Configure Azure Private Link connections
B. Configure encryption by enabling customer-managed keys (CMKs)
C. Share the connection string from the access key
D. Create shared access signatures (SAS)
Correct Answer: D
Explanation:
Option A is incorrect because Azure Private Link allows you to access Azure PaaS Services and Azure-hosted customer-owned and partner services traversing a private endpoint in your virtual network. It will not give you the ability to time strict access.
Option B is incorrect because Azure Storage encrypts all data within a storage account at rest. By default, data is encrypted with Microsoft-managed keys. For further management over encryption keys, you can control your keys. Customer-managed keys must be collected in Azure Key Vault, or Key Vault Managed Hardware Security Model (HSM); this will not provide time-restricted access to the storage.
Option C is incorrect because a connection string incorporates the authorization information needed for your application to gain access to data in an Azure Storage account at runtime; utilizing Shared Key authorization will not meet the objective.
Option D is correct because a shared access signature (SAS) offers secure delegated access to resources within your storage account. With SAS, you have granular management over how a user can access your data.
Reference: https://docs.microsoft.com/en-us/azure/storage/common/storage-sas-overview
Domain : Design security for infrastructure
Question 8 : You are a security solution architect for your organization.
Your chief information officer has tasked you with building a hybrid cloud infrastructure.
Listed below are the hybrid cloud requirements.
- Manage Azure subscription at scale.
- Manage multi cloud environments.
Please select two of the needed solutions to meet the requirements above.
A. Azure Lighthouse
B. Azure AD B2C
C. Azure Arc
D. Microsoft Azure Stack Hub
Correct Answers: A and C
Explanation:
Option A is correct because Azure Lighthouse offers unified, cross-tenant subscription management without the overhead of maintaining guest accounts.
Option B is incorrect because Azure AD B2C is a customer identity access management (CIAM) solution that maintains millions of users and billions of authentications daily; this will not meet the objective.
Option C is correct because Azure Arc streamlines governance and management by providing a consistent multi-cloud and on-premises management platform.
Option D is incorrect because Microsoft Azure Stack Hub is a hybrid cloud platform that provides services from your data center; this will not suffice your needs.
References: https://docs.microsoft.com/en-us/azure/active-directory-b2c/overview, https://docs.microsoft.com/en-us/azure/azure-arc/overview, https://docs.microsoft.com/en-us/azure/lighthouse/concepts/cross-tenant-management-experience
Domain : Design security for infrastructure
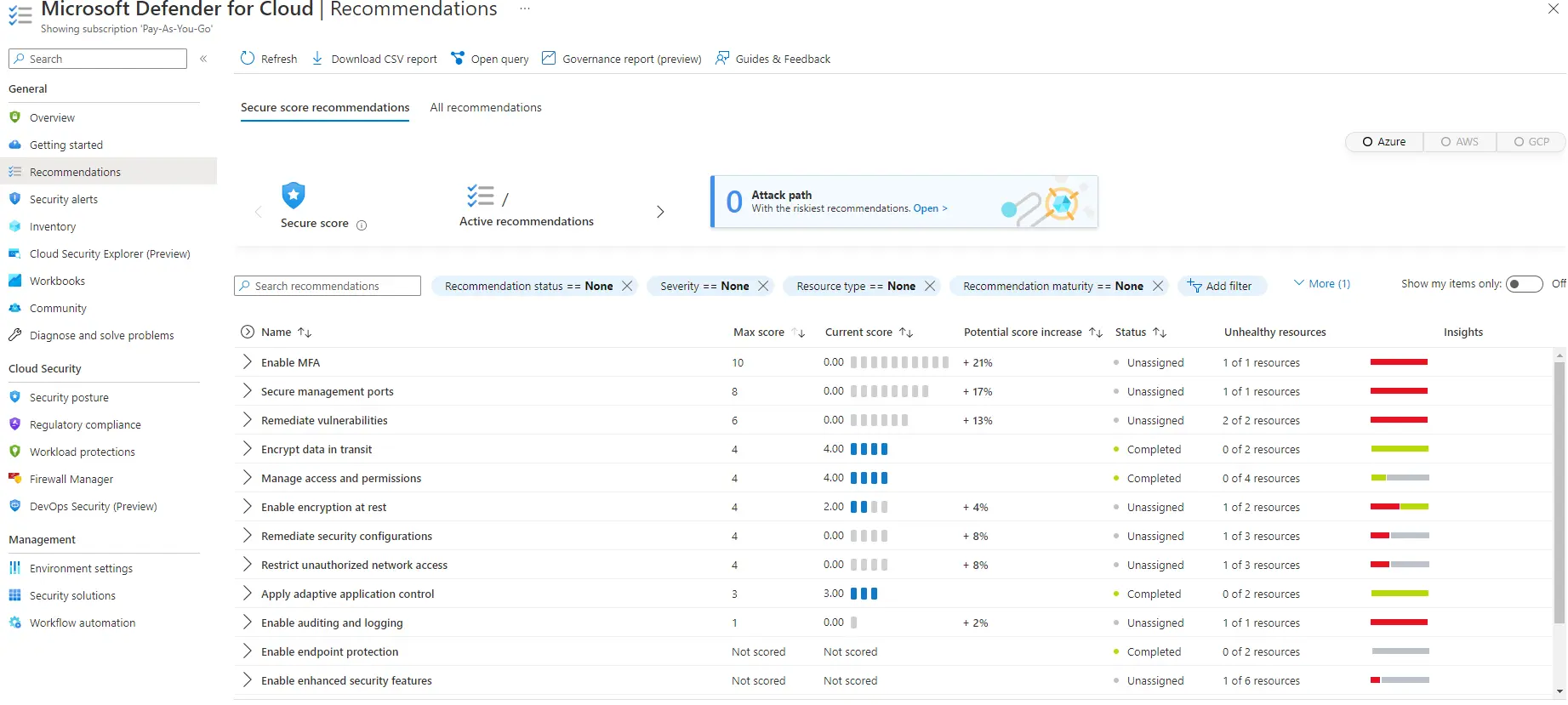
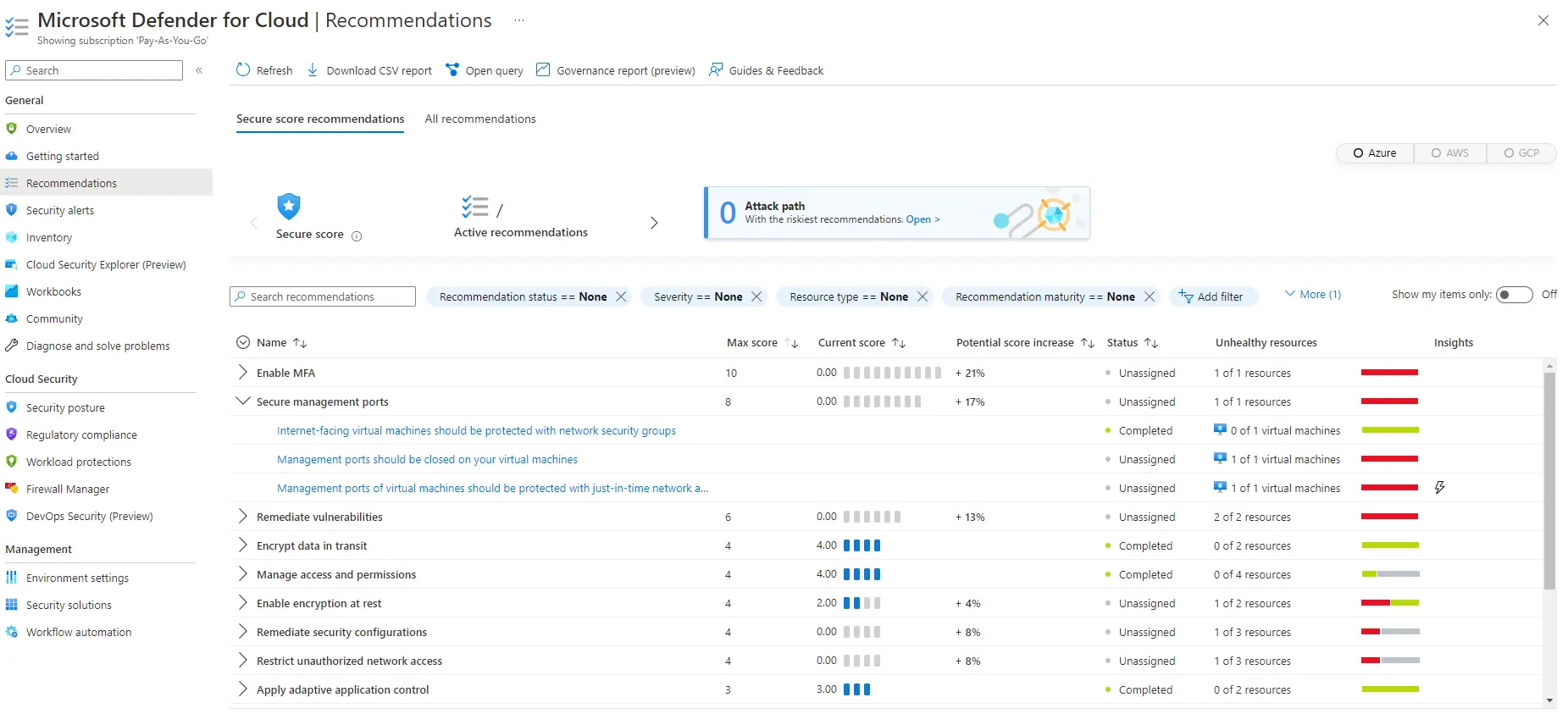
Question 10 : Based on the image below, you would find recommendations on securing your Internet-facing VM under enabling endpoint security recommendations. State True or False.
A. True
B. False
Correct Answer: B
Explanation:
The answer is false you will have to review secure management ports to see recommendations securing your Internet-facing VM protection
The answer is false: you will have to review secure management ports to see recommendations about securing your Internet-facing VM protection.
References: https://techcommunity.microsoft.com/t5/microsoft-defender-for-cloud/security-control-secure-management-ports/ba-p/1505770, https://learn.microsoft.com/en-us/azure/defender-for-cloud/recommendations-reference
Domain : Design security for infrastructure
Question 12 : As a Security Administrator, you implemented an Azure Storage Account. You need to create an access strategy for external applications on the Internet to your Azure Storage Account.
You must implement a secure solution for the external Internet application to access the Azure Storage provision in the storage.
What service and solution below will meet your objective?
A. Implement Managed rule sets from the Azure Web Application Firewall (WAF) policies
B. Configure Inbound rules in Network Security Groups (NSGs)
C. Configure firewall rules for the storage account
D. Configure the Application Security Group (ASG)
Correct Answer: C
Explanation:
Option A is incorrect because implementing Managed rule sets from the Azure Web Application Firewall (WAF) policies focus on traffic traversing your Azure web applications, not your Azure storage.
Option B is incorrect because an Azure network security group manages traffic traversing your Azure virtual network and Azure resources; this will not meet your objective of providing secure access to external applications.
Option C is correct because a storage firewall rule focuses on the public endpoint of the storage account; therefore, no firewall access rule is required to grant traffic destined to the endpoint of the storage account; this approach will meet your objective.
Option D is incorrect because an application security group helps you group virtual machines in which you can apply security policies limiting traffic to the security group; this will not support your secure access strategy for your storage.
Reference: Configure Azure Storage firewalls and virtual networks | Microsoft Learn
Domain : Design security for infrastructure
Question 13 : Your organization recently migrated its application to Azure App Services. You also implemented Azure Front Door. You need to recommend a solution allowing access to Azure App Services through a specific Azure Front Door instance.
You propose access limitations based on HTTP headers identified as Azure Front Door ID.
Will this meet your objective? True or False.
A. True
B. False
Correct Answer: A
Explanation:
The answer is true you can restrict traffic using the below methods
Azure Front Door ID headers:
Traffic from Microsoft Azure Front Door to your application comes from a well-known collection of IP ranges specified in the AzureFrontDoor.Backend service tag. Utilizing a service tag restriction rule, you can limit traffic to only come from Azure Front Door. To guarantee traffic only originates from your specific Azure Front Door instance, you can additionally filter the inbound requests created in the particular HTTP header that Azure Front Door sends Azure Front Door Service tags.
Domain : Design a Zero Trust strategy and architecture
Question 14 : You have an Azure subscription with Azure Management Groups, and you recently implemented Microsoft Defender for Cloud and Microsoft Azure Sentinel.
When an alert is triggered, you need the ability to analyze the security event and receive remedial suggestions.
What solution below will fulfill your objective?
A. Microsoft Sentinel threat intelligence workbooks and Threat intelligence reports in Defender for Cloud
B. Microsoft Sentinel Notebooks
C. Threat intelligence reports in Microsoft Defender for Cloud and workload protections in Defender for Cloud
D. Workload Protections in Defender for Cloud
Correct Answer: A
Explanation:
Option A is correct because Microsoft Sentinel threat intelligence workbooks facilitate a wide range of monitoring and investigation based on the data collected.
Microsoft Defender for Cloud provides surveillance on security information from your Azure resources; it also facilitates connection to partner security solutions, which can be used to identify potential threats; it also includes a suggestion to mitigate against security threats; information is provided in a threat analysis report which consolidates all the security information in a single report.
Option B is incorrect because Microsoft Azure Sentinel Notebooks is mainly offering security insights with actions to examine inconsistencies and hunt for malicious actions.
Option C is incorrect because Microsoft Defender for Cloud workload protection provides a catalog of advanced threat intelligent protection for specific resources; once enabled, this will not provide the holistic view and action needed in this scenario.
Option D is incorrect because Microsoft Defender for Cloud workload protection provides a host of advanced threat intelligent protection of specific resources; once enabled, this will not offer the holistic view and action needed in this scenario.
References: https://docs.microsoft.com/en-us/azure/sentinel/understand-threat-intelligence, https://docs.microsoft.com/en-us/azure/defender-for-cloud/defender-for-cloud-introduction, https://docs.microsoft.com/en-us/azure/defender-for-cloud/threat-intelligence-reports, https://docs.microsoft.com/en-us/azure/sentinel/notebooks
Domain : Design a Zero Trust strategy and architecture
Question 15 : You have an Azure subscription, and recently implemented Microsoft Sentinel.
Your Chief Technical Officer has asked you for a solution to automate and optimize mitigation action to your security alert responses received in Microsoft Azure Sentinel.
Which solution will suffice the requirements above?
A. Microsoft Azure Sentinel Notebooks
B. Microsoft Azure Sentinel Playbooks
C. Microsoft Azure Sentinel Workbooks
D. Microsoft Defender for Cloud workload protection
Correct Answer: B
Explanation:
Option A is incorrect because Microsoft Azure Sentinel Notebooks it is mainly used for machine learning data analyzing and visualizing the data; this solution will not provide the orchestration functionality you need to achieve your objective.
Option B is correct Microsoft Azure Sentinel Playbooks can support organizations with automating and orchestrating their response to security threats, this will meet your objective as you can configure Microsoft Azure Sentinel Playbooks, to automate mitigation action against security.
Option C is incorrect because Microsoft Azure Sentinel Workbooks support the organization by providing the backdrop for data analysis and the creation of visuals within the confines of the Azure portal it integrates multiple sources data, unifying data in which users can interact, this feature will not meet your objective.
Option D is incorrect because Microsoft Defender for Cloud workload protection provides a host of advanced threat intelligent protection of specific resources; once enabled, this will not offer the holistic view and action needed in this scenario.
Reference: Use playbooks with automation rules in Microsoft Sentinel | Microsoft Learn
Domain : Evaluate Governance Risk Compliance (GRC) technical strategies and security operations strategies
Question 16 : You have an Azure subscription with Azure App Service and Azure virtual machines. Your landing zone is configured in a Hub and spoke model, and the Azure subscriptions are placed into an Azure Management Group.
You must ensure that any new Azure subscription has Microsoft Defender for Cloud enabled.
You implemented an Azure Policy effect of DeployIfNotExists to ensure that any new Azure subscription has Microsoft Defender for Cloud enabled.
Will this meet your objective, True or False?
A. True
B. False
Correct Answer: A
Explanation:
The answer is correct because Using the Azure policy effect of DeployIfNotExists will ensure Microsoft Defender for Cloud is enabled on all subscriptions being added to the Azure Management Group. This will meet your objective.
Reference: Azure landing zone frequently asked questions (FAQ) – Cloud Adoption Framework | Microsoft Learn
Domain : Design security for infrastructure
Question 17 : You are managing a multi-cloud environment; you deployed AWS resources and planned to use Microsoft Defender for Cloud to extend your security abilities within AWS. Azure Arc will not be deployed.
Which feature can you utilize in Microsoft Defender for Cloud without enabling Azure arc?
A. Microsoft Azure Policy
B. Microsoft Defender for Cloud Containers
C. Microsoft Defender for Storage
D. Microsoft Defender for Servers
Correct Answer: B
Explanation:
Option A is correct because once you register your AWS account in Microsoft Defender for Cloud, without Azure Arc, you will be able to implement Azure policies to the resources In AWS.
Option B is incorrect because you need to deploy Azure Arc on the AWS containers to enable Microsoft Defender for Cloud Containers.
Option C is incorrect because you need to deploy Azure Arc on the AWS Storage to enable Microsoft Defender for Cloud Storage.
Option D is incorrect because you need to deploy Azure Arc on the AWS Servers to enable Microsoft Defender for Cloud Servers.
References: https://docs.microsoft.com/en-us/azure/defender-for-cloud/quickstart-onboard-aws?pivots=env-settings, https://docs.microsoft.com/en-us/azure/defender-for-cloud/defender-for-containers-introduction
Domain : Evaluate Governance Risk Compliance (GRC) technical strategies and security operations strategies
Question 18 : You are an Azure administrator. You have several departments of units that manage their Azure subscription.
You recently noticed that departments are deploying Virtual Machines over the resource specifications for the workloads. You would also like to implement security standards when resources are being deployed.
Requirements:
- Avoiding resource allocations mismatch, to application needs
- Implement security standards when resources are being deployed.
Which Azure solution can meet the above requirements?
A. Microsoft Azure Blueprint
B. Microsoft Azure Policy
C. Microsoft Azure RBAC
D. Microsoft Defender for Cloud Just-in-time (JIT) VM Access
Correct Answer: A
Explanation:
Option A is correct because Azure Blueprint helps you design repeatable deployments perimeters.
You can identify predefined application workloads that match the correct cloud computing resources needed to run the application efficiently without wasting computing resources.
Each department can use these repeatable deployments to avoid using the incorrect infrastructure. You can also include security design specifications for the deployment, which will meet your objective.
Option B is incorrect because Azure Policies support the enforcement of standards and assess compliance. Compliance information is consolidated in the compliance dashboard; it provides a cohesive view of the overall compliance health of your Azure resources; this will not meet your objective.
Option C is incorrect because Microsoft Azure RBAC is used for cloud resource access management. This solution will not meet your objective.
Option D is incorrect because Microsoft Defender for Cloud Just-in-time (JIT) VM access supports your organization by providing authorization control access to your Virtual Machine; this will not meet your objective as your primary focus is managing what is deployed in your Azure environment.
Reference: Overview of Azure Blueprints – Azure Blueprints | Microsoft Learn
Domain : Design a Zero Trust strategy and architecture
Question 19 : You are an Azure security consultant for an organization; the organization currently has a subscription and uses Azure Active Directory; you are asked to provide this solution that can support the Security Operations Team in reviewing group membership access to the organization’s enterprise applications. The review must also include role assessment.
You recommended Azure policy. Will this meet your objective, True or False?
A. True
B. False
Correct Answer: B
Explanation:
Azure AD access review supports your organization by controlling memberships, access to your enterprise applications, and role assignments. User access can be evaluated routinely to ensure the right users have constant access to your enterprise application
Reference: https://learn.microsoft.com/en-us/azure/active-directory/governance/access-reviews-overview
Domain: Design a Zero Trust strategy and architecture
Question 20 : You are a security analyst for an organization; you are asked to develop an identity management strategy.
The organization’s current infrastructure includes
- Microsoft Active Directory
- Azure Active Directory
Please match the appropriate requirements to the Solution
| Requirements | Solution | ||
| 1 | Microsoft Active Directory Connect | A | External customer to use their social media accounts to authenticate to your services |
| 2 | Azure Active Directory B2B | B | External business partners to access Azure resources using their organization domain account. |
| 3 | Azure Active Directory B2C | C | The ability to unify on-premise Active Directory user accounts Azure Active Directory |
Correct Answer: 1-C, 2-B and 3-A
Explanation:
Azure AD Connect allows the organization to unify its on-premise Active Directory with Azure Active Directory; this will meet the objective of unifying the organization’s identities.
Azure Active Directory B2B allows organizations to collaborate with business partners using their original domain account while accessing resources in Azure.
Azure Active Directory B2C provides an identity feature allowing customers to use their social media accounts to access your organization’s application seamlessly; this also can be used with an Application Programming Interface.
Reference: Overview of Azure Active Directory Domain Services | Microsoft Learn
Summary
In conclusion, the Microsoft Cybersecurity Architect (SC-100) certification exam is a valuable asset for cybersecurity professionals looking to advance their skills and knowledge in the field. By providing Microsoft SC-100 free practice questions, we aim to help you prepare for the exam and gain a better understanding of the types of questions you will encounter on the test.
We hope that this post has been helpful in your journey to become a Microsoft Cybersecurity Architect. Remember to keep studying and practicing, and don’t hesitate to reach out for additional resources if you need.
Take the first step towards becoming a Microsoft Cybersecurity Architect by trying our FREE Practice Test for the SC-100 exam now!
- Top 25 DevSecOps Interview Question and Answers for 2024 - March 1, 2023
- How to prepare for VMware Certified Technical Associate [VCTA-DCV] Certification? - February 14, 2023
- Top 20 Cloud Influencers in 2024 - January 31, 2023
- 25 Free Question on SC-100: Microsoft Cybersecurity Architect - January 27, 2023
- Preparation Guide on MS-101: Microsoft 365 Mobility and Security - December 26, 2022
- Exam tips to prepare for Certified Kubernetes Administrator: CKA Exam - November 24, 2022
- Top Hands-On Labs To Prepare For AWS Certified Cloud Practitioner Certification - October 27, 2022
- Why do you need to upskill your teams with the Azure AI fundamentals? - October 11, 2022