Are you confident that your organization’s governance, risk, and compliance (GRC) strategies are up to par?
In today’s world, interconnectivity tends to increase, and it certainly makes the organization’s data subject to a wide range of threats. It significantly compromises the CIA of data, systems as well as networks. One prompt solution for this threat can be risk governance.
It can be highly possible by taking SC-100 certification, which can help you to attain geekiness in governance activities. Making yourself dive into the Governance Risk Compliance (GRC) technical and security operations strategies can produce beneficial results such as securing the assets, maintenance of the regulatory compliance and protection of the reputation.
This sort of evaluation process aims to identify the effectiveness of GRC as well as security operations in attaining the objectives, detection of potential threats and suggests measures to improvise the overall security posture.
As a cybersecurity architect, you can proactively find the security threats and can minimize the risks and assure that the organization adheres to regulatory compliance.
In this blog post, we’ll dive into the world of GRC and share the best practices for evaluating these critical strategies to keep your company safe and secure.
Let’s have a look at them!
Interpretation of compliance requirements and their technical capabilities
In general, the term “ Compliance” refers to a set of regulations, guidelines, and standards that the firm must comply with to ensure that they are acting in accordance with legal, operational, and ethical standards. It may vary on the basis of organization type, industry, and jurisdiction.
Also Read: Study Guide on SC-100: Microsoft Cybersecurity Architect
Once the risks are identified and transformed from decisions into policy statements, then the cybersecurity architect can establish a compliance strategy. The compliance strategy can be good only if the security controls are adopted in a way to map the regulatory compliance requirements. To ensure it, it is important to have clear visibility of business type, business requirements, and transactions before the establishment of a compliance strategy.
While going for governance activity, there are certain disciplines are followed and they are:
- Cost Management
- Security Baseline
- Resource consistency
- Identity Baseline
- Deployment acceleration
Considerations during compliance activity
Compliance can be categorized as per the risk type, such as regulatory or operational. Operational risk occurs when any failure occurs to internal controls of system and assurance functions and makes the organization to be subjected to defalcation, operational loss and so on.
On the other hand, compliance risk evolves when any risk causes an effect on legal or regulatory sanctions and its effects are financial loss, code of conduct and other regulatory issues. When going for a compliance strategy, it is essential to consider that the operational compliance can aid regulatory compliance.
Let’s have a glance at tools used while carry out operational compliance activity:
| Process | Tool | Purpose |
| Patch Management | Azure Automation Update Management | Management and scheduling of updates |
| Policy enforcement | Azure Policy | Policy enforcement to ensure environment and guest compliance |
| Environment configuration | Azure Blueprints | Automated compliance for core services |
| Resource configuration | Desired State Configuration | Automated configuration on guest OS and some aspects of the environment |
The compliance requirements vary according to the organization’s industry and service type.
Infrastructure compliance evaluation by using Microsoft Defender for Cloud
For the governance and compliance activity, there are various tools and services available such as Azure blueprints, Azure policy and Microsoft defender. With help of those tools, governance activity can be automated.
Among all, Microsoft defender plays a vital role in governance strategy. It helps to provide the utmost security as it can be able to do the following things:
- Offer unified view of security in varied workloads
- Aggregates, predicts and analyze the security of the data from wide range of sources such as firewalls and other some partner solutions
- Offers security recommendation to solve the issues before it gets exploited
- Can be implied to apply the security policies in the hybrid based cloud workloads for assuring compliance as per the security standards
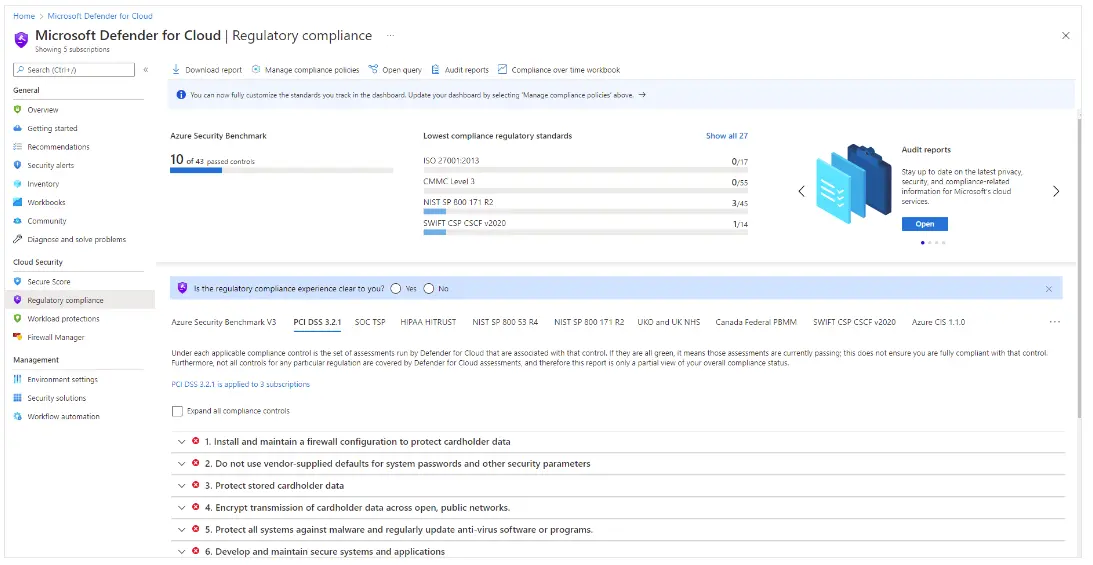
In the dashboard of the Microsoft Defender, you can be able to pick the required compliance standards and mapping of the requirements to the applied security assessments takes place.
Interpretation of compliance scores and recommending actions to resolve issues or improve security
The data in the regulatory compliance dashboard of Microsoft Defender can be utilized for the enhancement of the compliance posture by making some recommendations directly within the dashboard.
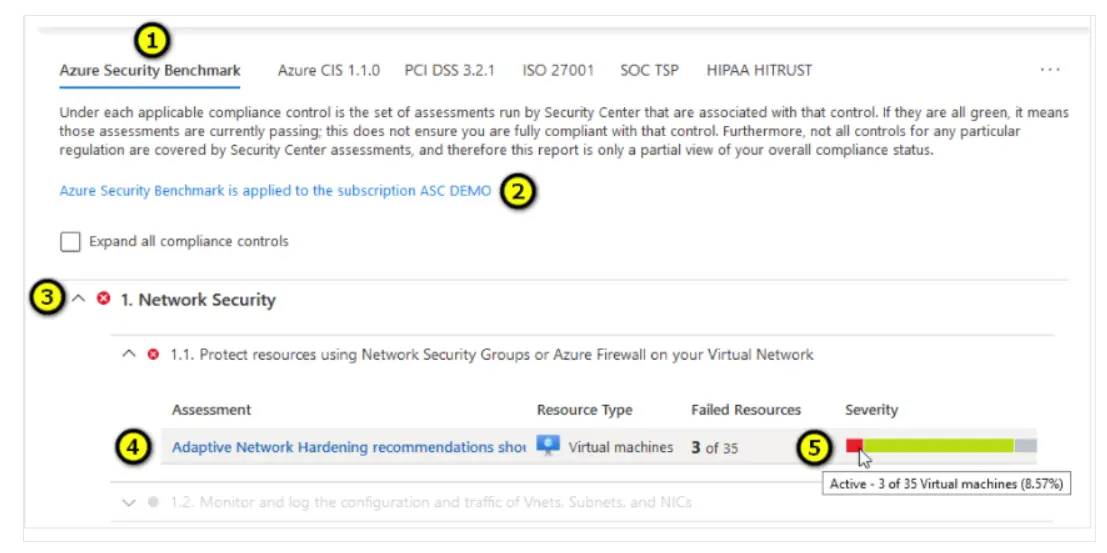
To accomplish this, you need to select any one of the failing assessments that displays in the dashboard and you can see various recommendations.
The recommendations contain a set of remediation sets to eliminate the issue.
The below shown steps can be followed to resolve the compliance recommendations:
- Select a compliance standard tab and pick the one that suits for your organization
- Then you can select the subscription for those standards
- You can select list of controls for the chosen standard
- For applicable controls, you can seek information of passing as well as failing assessment associated with that control
- You can also see the resource number that are get affected by that assessment
Designing and validating Azure policies
In the cloud computing environment, the continuous monitoring process is necessary as the workload tends to vary. New workloads are produced on a daily basis, which becomes crucial to assure these workloads are in a secure state.
To ensure security to those workloads, continuous monitoring process becomes significant.
When designing Azure policy, certain considerations must be taken into account to satisfy the organization needs from an infrastructure perspective. By making tailored policies, one can be able to minimize the audit time.
In the following ways, the Azure policies has been designed and validated:
Setting guardrails
Setting guardrails for the entire data resources can help to ensure compliance, eliminate misconfiguration and practice consistent governance activity. The number of external approval can be minimized by means of Azure policy.
There are certain conventions established for the resources by the Azure policy. A condition can compare the property field of resources or a value to the required value. The resource property field can be accessed with usage of aliases. When a resource property field is in an array, then special array aliases can be implied to select the values from array members and conditions will be applied for each one.
Cost control
The cost control can be achieved by just defining the conventions and it can make management of the resources easier. For instance, you can define that only certain types of virtual machines can be allowed.
It has been found that policy assignments get inherited by child resources. It means if any policy assignment applied to a resource group, it will be applicable to all resources in the resource group.
Validating new policy
The new policy designed can be validated by the following steps such as:
- Tightly defining the policy
- Auditing the existing resources
- Audit new or updated resource requests
- Deployment of policy to resources
- Continuous monitor
Designing data residency requirements
Data sovereignty can be ensured by means of data residency. Data sovereignty suggests rules and requirements for those who have control over the consumer data that resides in the cloud. In certain cases, the customer data will be subjected to legal and regulatory laws of the country in which the information is stored. It has a direct effect on the data accessing for customer initiated requests or platform maintenance.
Azure region and its service features can offer customers with varied avenues so that they can be able to select and limit the data access and residency. This sort of flexibility with the data residency requirements can make the customers in a regulated manner. It can make the industries run the mission critical workloads in the cloud to run successfully by making use of Microsoft hyperscale cloud benefits.
Personal data
Most of the Azure services are deployed in a regional manner and allows you to specify where the customer data can be stored and processed. Examples of such regional services such as VMs, storage, and SQL Database.
To achieve resiliency, Microsoft uses variable network paths that sometimes cross geo boundaries. However, replication of customer data between regions can be transmitted over encrypted network connections.
Considering Azure policy
When designing a data residency solution, the Azure policy usage must be taken into consideration. You can also use the Azure policy for the implementation of the governance over the cloud data and infrastructure..
To restrict resources and data to specified Azure regions, users can use allowed location policy. Once it gets established, the newly deployed resources get checked whether it is in alignment with the policies and also ensure that older resources are scanned in a periodic manner to ensure compliance.
Considering Azure blueprints
Another way to achieve data residency such as usage of Azure blueprints. It can be used when you require templates to create, deploy and update the governed cloud to standards that meet regulatory requirements.
If you want to ensure that the data is retained only in the chosen region, you can pick any one of the following options:
- Data storage for regional services: The majority of Azure services are regionally distributed, and you can choose the location where the service will be installed. With the exception of a few regional services and Trial services as detailed on the Azure data location page, Microsoft won’t keep your information outside the region you choose. This promise aids in ensuring that the region in which your data is stored will stay the location in which it is stored.
- Data storage for non-regional services: As stated on the data location page, some Azure services do not allow you to define the region in which the services will be deployed.
The data is always mirrored in an Azure Storage account to help ensure durability and high availability.
Translation of privacy requirements into requirements for security solutions
Microsoft has a long-standing commitment to data privacy, and Microsoft Azure was designed from the ground up with this commitment in mind. To protect your data in the cloud, including the kinds of personal data listed under specific security or privacy requirements, Microsoft built Azure with industry-leading security controls, compliance tools, and privacy policies. Additionally, they aid you in adhering to other significant national, international, and regional privacy laws and regulations, including ISO/IEC 27018, EU Model Clauses, EU-U.S. Privacy Shield, HIPAA/HITECH, and HITRUST.
By more easily attaining compliance and enabling privacy-sensitive cloud scenarios, like financial and health services, you can speed your transition to the cloud when you built on Azure’s secure foundation. According to the industry and compliance norms that must be followed, many organisations will demand varying levels of privacy requirements. Strong data security is offered to clients by Azure by default on both its own infrastructure and for customer-enabled services.
What is the SC-100 exam?
The SC-100 exam includes subject matter experience in developing cybersecurity strategies to safeguard an organization’s goals and operational procedures throughout all facets of the enterprise architecture.
You may demonstrate your proficiency in designing cybersecurity solutions using the entire spectrum of Microsoft cybersecurity services and features by just passing the SC-100 Microsoft Cybersecurity Architect Expert exam.
What is governance, risk, and compliance in security?
GRC is a structured method for coordinating IT with business objectives while controlling risks and adhering to all applicable statutory and regulatory requirements.
What are the GRC skills?
The abilities needed for GRC include automating and continually monitoring information security rules, exceptions, risks, and testing. GRC stands for governance, risk, and compliance. Furthermore, it aids in the creation of reporting metrics, dashboards, and artefacts of evidence.
Is getting SC-100 Certification worth it?
SC-100 broadly covers the topics relevant to cybersecurity. It doesn’t mean that only those who intend to learn cybersecurity only must be chosen in this field. It can be taken by the people who work in application development and IT. Today, the scope for cybersecurity professionals is enormous. And thus pursuing a career in this field will be worth it.
Conclusion
Passing the SC-100 exam demonstrates that an individual has a strong understanding of GRC technical strategies and security operations strategies and can apply this knowledge to mitigate risks and protect organizational assets effectively.
It is an important certification for those seeking to demonstrate their expertise in the GRC and security operations domains and advance their career in the field of cybersecurity.
Having any doubts, please contact us experts today!
- A Tour of Google Cloud Hands-on Labs - December 12, 2023
- Mastering Azure Basics: A Deep Dive into AZ-900 Exam Domains - December 4, 2023
- Exploring the Benefits of Validation Feature in Hands-on Labs - October 10, 2023
- 20+ Free MD-102 Exam Questions on Microsoft Endpoint Administrator - September 27, 2023
- 20+ Free MS-102 Exam Questions on Microsoft 365 Administrator Certification - September 25, 2023
- AWS Certified Developer Salary in 2024 - September 19, 2023
- Guide to SharePoint, OneDrive, and Teams External Sharing in Teams - September 10, 2023
- What is Cross-Tenant Synchronization | MS-700 Certification - August 31, 2023



