In this blog let’s discuss the various protection measures against DDoS attacks including the AWS Shield in its various forms, edge locations, resilient infrastructure, and integration of best security practices. We will also learn how the AWS Certified Security Specialty certification equips professionals with the tools and knowledge necessary to proactively protect their cloud environments.
In a DDoS attack, malicious actors using multiple machines generate large volumes of packets or requests that overwhelm the target system and aim to disrupt the normal traffic of a targeted system.
AWS cloud environments are susceptible to the adverse effects of distributed denial-of-service (DoS) attacks which attempt to affect the availability of a targeted system to legitimate end users.
Amazon Shield
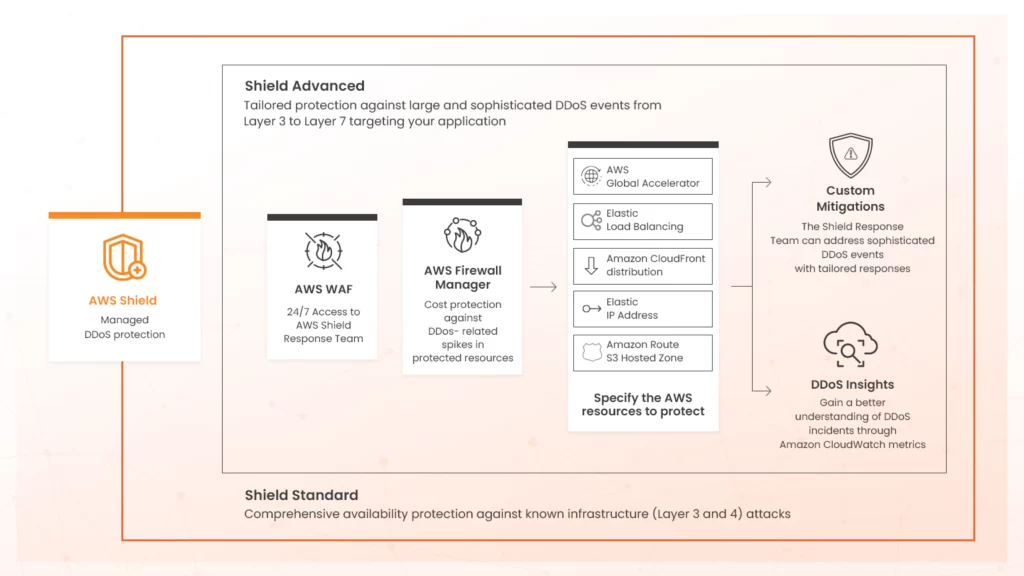
AWS offers a managed DDoS protection service called AWS Shield, which is dedicated to preventing or mitigating the effects of DDoS attacks by automatically detecting and responding to such attacks. AWS Shield comes in two versions, namely Shield Standard and Shield Advanced, as shown below
Amazon Shield Standard
The AWS Shield standard protects the organization against all known layer 4 DDoS attacks. It integrates seamlessly into the entire AWS environment and automatically protects all AWS customers at no additional cost. The protection covers DDoS attacks for various resources including Amazon Route 53 hosted zones, Amazon CloudFront distributions, and AWS Global Accelerator standard accelerators. AWS Shield comprises the following capabilities.
- Static threshold DDoS protection: The AWS Shield Standard provides continuous network flow monitoring, inspecting incoming traffic to AWS services. It uses a combination of analytical techniques such as traffic signatures and anomaly algorithms to detect DDoS malicious traffic in real time. However, the protection thresholds set for each AWS Shield Standard service are static and the services do not provide custom protections to applications.
- Inline attack mitigation: This comprises built-in automated mitigation techniques that provide the underlying AWS services with protection against common and frequently occurring infrastructure attacks. The automatic mitigations are deployed inline to protect AWS services against DDoS attacks which eliminates any latency impact. This enables faster detection and resolution of DDoS attacks thereby contributing to a secure AWS environment.
Amazon Shield Standard
AWS Shield Advanced offers a more extensive service and incorporates a support team, AWS Wireless Application Firewall (WAF), and AWS Firewall Manager. It comes with an additional cost and provides a higher level of protection.
- Advanced DDoS detection and mitigation techniques: AWS Shield Advanced employs advanced detection and mitigation techniques against complex DDoS attacks based on traffic patterns. It provides customized detection based on traffic patterns to protect elastic IP addresses, ELB, CloudFront, Global Accelerator, and Route 53 resources. This includes protection against DDoS attacks that target the application layer, such as HTTP floods and DNS query floods, which may not be adequately mitigated by the AWS Shield Standard. It adds region- and resource-specific monitoring techniques to detect and alert an organization of smaller DDoS attacks. This feature allows organizations to detect, understand, and respond to DDoS threats more efficiently and effectively.
- Integration with AWS WAF: AWS Shield Advanced seamlessly integrates with AWS WAF, providing an additional layer of DDoS protection at no additional cost. This integration allows for a more comprehensive defense strategy, protecting against more nuanced and sophisticated threats targeting application vulnerabilities. An organization can easily create customized mitigations against illegitimate requests which may indicate impending DDoS attacks. AWS Shield Advanced can create, evaluate, and deploy WAF rules in Web ACLs to automatically mitigate a DDoS attack, or an organization can activate them in count-only mode. The AWS Firewall Manager can also be configured to provide centralized management of security policies at no additional cost.
- Autoscaling: DDoS attacks often aim to overwhelm resources by flooding them with traffic. An effective countermeasure is to design the system architecture for scalability. Using AWS Shield’s auto-scaling capabilities ensures that infrastructure can handle sudden spikes in traffic without compromising performance or availability. This not only helps absorb the impact of the DDoS attack but also ensures that legitimate traffic is not adversely affected.
- AWS Shield Response Team (SRT): AWS Shield Advanced subscribers can also effectively deal with DDoS attacks 24/7 and have direct access to the AWS SRT. This team provides guidance and support, helping to manage and mitigate attacks as they occur. For example, once an organization identifies an indication of a DDoS attack, it can quickly contact the AWS SRT and instantly get the necessary guidance for mitigating it. An organization can also engage directly with the AWS SRT to place custom AWS WAF rules on behalf in response to an application layer DDoS attack. The team will diagnose the attack and, with permission, apply mitigations on behalf of the organization. This reduces the length of time that applications might be affected by an ongoing DDoS attack
- Health-based detection: AWS Shield Advanced uses the health of applications to improve responsiveness and accuracy in attack detection and mitigation. Health checks associated with the application improve the detection sensitivity of Shield Advanced. An organization can define a health check in all resource types that Shield Advanced supports such as Elastic IP, ELB, CloudFront, Global Accelerator, and Route 53, and associate it with a resource protected by AWS Shield Advanced through the console or API. This allows AWS Shield Advanced to detect attacks that affect application health more quickly and at lower traffic thresholds, improving the resiliency of the DDoS application and preventing false positive notifications.
Implement Resilient DDoS-Resistant Architecture
When building applications, it is critical to ensure a resilient architecture that can prevent DDoS attacks. This architecture should provide an additional layer of network infrastructure that is crucial in mitigating DDoS attacks. This is referred to as edge location DDoS mitigation and is achieved through the use of Amazon CloudFront, Amazon Global Accelerator, and Route 53.
Amazon CloudFront: To mitigate against DDoS attacks, an organization can deploy Amazon CloudFront as a Content Delivery Network (CDN) to distribute web application content globally. Amazon CloudFront captures content at edge locations, reducing latency, improving overall application performance, and serving static content from edge locations. This provides DDoS protection at the edge, helping to mitigate common attacks such as SYN floods and UDP reflection attacks. This also helps protect the backend by reducing the load on origin servers during DDoS attacks. Amazon CloudFront also has geo-blocking features to block specific regions if an organization identifies patterns of DDoS attacks originating from those particular regions. One crucial benefit of Amazon CloudFront is that it automatically scales to manage larger DDoS attacks, thus providing an even more resilient architecture.
Amazon Global Accelerator: The Amazon Global Accelerator can be deployed to access applications from the edge, as it provides static IP addresses that function as a fixed entry point to the application. This feature directs traffic over the AWS global network to the optimal AWS endpoint, reducing latency and improving availability. It integrates with AWS Shield, combining the benefits of any mapped IP address from AWS Global Accelerator with AWS Shield DDoS protection. It can also be deployed as an alternative to Amazon CloudFront and improves the DDoS resilience of the application when serving any type of application traffic from edge locations distributed around the world. An organization can run an application in any AWS Region and use these services to protect application availability and optimize the performance of the application for legitimate end users. This is useful in mitigating larger volumetric DDoS attacks, which can reach the terabit scale.
Route 53: Route 53 is a scalable and universally available Domain Name Service (DNS) web service that provides fast and reliable domain name resolution at the edge through a global network of DNS servers. It includes built-in DDoS protection, helping to mitigate DNS-based DDoS attacks. It automatically scales to manage large volumes of queries, providing resiliency against DDoS attacks targeting the DNS infrastructure.
AWS Security Best Practices
The following best practices provide another layer for DDoS attacks and should form part of the overall security architecture of an organization.
- Reduce attack surface area: Minimizing the DDoS attack surface limits the available options for attackers and allows an organization to concentrate on its mitigation efforts. Reducing the attack surface can be achieved through several techniques including the following.
- Deny unexpected requests: Rules can be implemented to reduce the attack surface of the application by denying any unexpected request patterns. This can be achieved by writing rules to deny requests with URLs that do not adhere to API URL requirements including requests with HTTP verbs that are not supported by API and host header values that are not part of domain names. Such rules block undesired traffic immediately reducing the likelihood of DDoS attacks.
- Implement rate-limiting rules: These aggregate requests according to a configured dimension such as IP, then block traffic if the aggregated request volume exceeds configured thresholds within a certain duration. Rate limits block offending traffic until their volume drops below configured thresholds This functionality can be implemented in AWS WAF and significantly reduces the risk of DDoS attacks.
- Enforce bot control: The objective of bot control is to protect against DDoS attacks caused by evasive bots such as HTTP floods. Bot Management is achieved through several functionalities techniques provided by AWS WAF Bot Control including behavioural detections, ML-based detection, and CAPTCHA challenges. Detection and mitigation of DDoS attacks using bot control occur instantly.
- Deploy Amazon CloudWatch: It is also crucial to configure Amazon CloudWatch alarms for AWS Shield and AWS WAF to receive notifications when an organization is under DDoS attacks. Amazon CloudWatch provides real-time monitoring and logging, setting up alarms for unusual activity allowing the organization to take immediate actions to prevent further damage.
- Deploy AWS Cloud Trail: AWS CloudTrail should be incorporated for the continuous logging, monitoring, and retention of account activity related to actions across the AWS infrastructure. This feature provides deep insight into the operation of the system and potential DDoS threats.
- DDoS Resiliency Assessment Runbook: To audit the configuration of AWS Shield Advanced, the organization should run the in-DDoS Resiliency Assessment Runbook in AWS Systems Manager. The runbook collects and analyses a variety of AWS resources including Amazon Route 53, Amazon CloudFront, AWS Global Accelerator, and AWS Elastic IPs. It examines their configuration settings in accordance with the recommended best practices that are geared toward DDoS mitigation.
- Perform regular systems updates: Regularly updating and patching systems, encrypting data in transit and at rest, and employing robust authentication and authorization mechanisms are also critical in safeguarding exposed clouding resources against DDoS attacks.
- Develop an Incident Response Plan (IRP): Despite the best preventive measures, the possibility of a DDoS attack cannot be entirely ruled out in AWS Cloud environments. It is therefore critical to have a well-structured incident response plan as a playbook during these critical times. The IRP should detail the steps to be taken in the event of a DDoS attack and the procedures to be followed in restoring operations.
- Test for DDoS resilience: Regular drills and simulations of potential DDoS attack scenarios are also crucial in ensuring that the organization is well prepared to respond effectively and efficiently in a real-world DDoS track situation. An organization can run a simulated DDoS attack in production traffic with an approved AWS Partner or conduct a synthetic simulated DDoS attack with the AWS Shield Response Team.
Conclusion
DDoS protection is a critical activity in the AWS cloud environments and there are a number of features to achieve this purpose. The major method of protection is to deploy AWS Shield with its standard and advanced features. The other important method is to protect DDoS attacks at the edge mainly through the deployment of the Amazon CloudFront and the AWS Global Accelerator. These should be deployed in unison to achieve a DDoS-resilient architecture. Best security practices such as reducing the attack surface, performing regular updates, and undertaking continuous monitoring also play a key role in DDoS protection.
- Mitigating DDoS Attacks on AWS with Security Specialty Certification Knowledge - October 17, 2024
- How to Connect AWS Lambda to Amazon Kinesis Data Stream? - October 3, 2024
- Deploying and Optimizing Machine Learning Models on AWS - September 3, 2024
- How to Pass Microsoft Azure Administrator Associate Exam on Your First Attempt - August 29, 2024

