If you are looking for Free SC-200 exam questions and preparing for SC-200 certification exam? – Then this article helps you in the exam preparation for SC-200 (Microsoft Security Operations Analyst certification exam). As we know that threats and security vulnerabilities in cloud computing are massively increasing. Effective usage of Microsoft 365 defender and Sentinel helps us to overcome such security issues and ensures healthy communication in a cloud environment.
How to prepare for the SC-200 Microsoft Security Operations Analyst Certification Exam?
Preparation for the Microsoft security operations analyst certification exam is very simple. You need to be very thorough on the exam objectives, then you have to learn the expected skills through video courses. By learning through video courses, you will be able to understand the exam objectives very clearly.
Once you are ready to take up the exam, test your earned skills by taking out these free questions on SC-200 and practice tests. If you found struggling in any topics, then re-learn and attempt the mock tests again before taking the actual exam.
These Free questions give you foundational knowledge and help in your SC-200 exam preparation. Let’s start exploring!
Domain : Mitigate threats using Microsoft 365 Defender
Q1 : You are a SOC Analyst of a company XYZ that has implemented Microsoft Defender for Endpoint. You are allocated an incident with alerts related to a doubtful PowerShell command line. You start by going through the incident and apprehend all the related alerts, devices, and evidence.
You open the alert page to evaluate the Alert and choose to perform further analysis on the device. You open the Device page and decide that you require remote access to the device to collect more forensics information using a custom .ps1 script.
Which type of information is gathered in an Investigation package?
A. Prefetch Files
B. Network transactions
C. Command History
D. Process History
Correct Answer: A
Explanation:
Network transactions, Process and Command History are not collected. Only Prefetch files are collected.
An investigation package contains the following folders when you collect it from a device as part of the investigation process. These can help us identify the present state of devices and methods used by attackers.
Autoruns, installed programs, Network Connections, Prefetch files, Prefetch folder, Processes, Scheduled tasks, Security event log, Services, Windows Server Message Block (SMB) sessions, System Information, Temp Directories, Users and Groups, WdSupportLogs, CollectionSummaryReport.xls
Domain : Mitigate threats using Microsoft 365 Defender
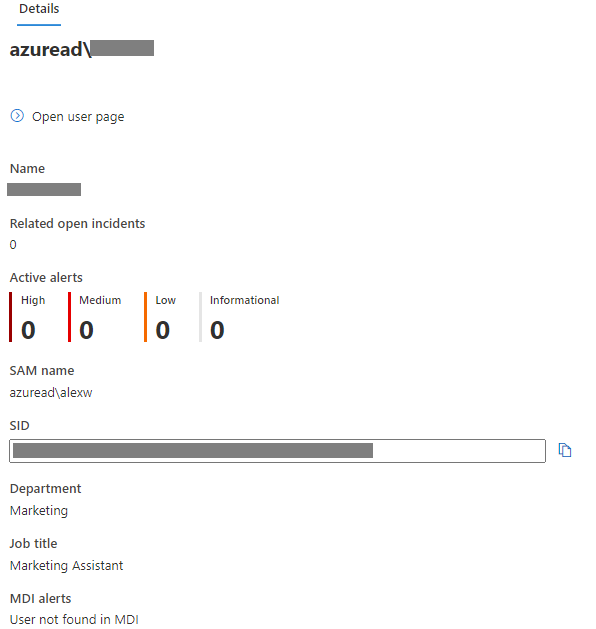
Q2 : Which information is shared on the user account page?
A. Security groups
B. Threat hunt ID
C. Associated alerts
D. All of the above
Correct Answer: C
Explanation:
The security groups, user accounts belong to and threat hunt ID is not shown.
Associated alerts are made available.
Domain : Mitigate threats using Microsoft 365 Defender
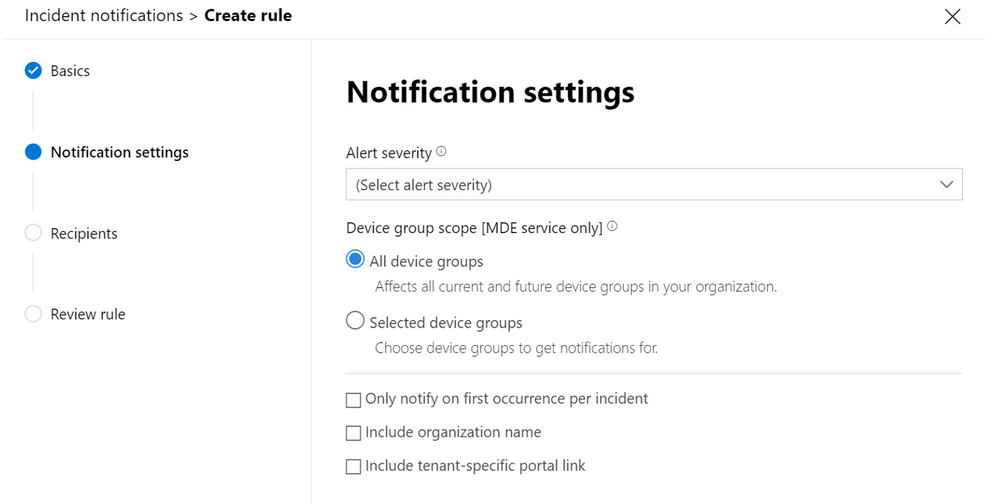
Q3 : Microsoft Defender for Endpoint gives configuration selections for alerts and detections. These include notifications, custom indicators, and detection rules. Which filter is a part of an Alert notification rule?
A. Subject IDs
B. Alert Severity
C. Account
D. Alert IDs
Correct Answer: B
Explanation:
Domain : Mitigate threats using Microsoft 365 Defender
Q4 : From which of the following can a SOC (Security Operation Center) analyst make a customized detection?
A. Alert
B. Incident
C. Advanced Hunting
D. Request
Correct Answer: C
Explanation:
Advanced hunting gives a choice to save the query as a detection, while Alert and Incident don’t provide an option to save as a detection.
Domain : Mitigate threats using Microsoft 365 Defender
Q5 : Microsoft 365 Defender gives a purpose-based UI to manage and examine security incidents and alerts across Microsoft 365 services.
You are a SOC Analyst working at a company XYZ that has configured Microsoft 365 Defender solutions, including Defender for Endpoint, Defender for Identity, Defender for Office 365, and Cloud App Security.
You are required to monitor related alerts across all the solutions as a single incident to observe the incident’s full impact and do an RCA (root cause investigation). The Microsoft Security center portal has a fused view of incidents and actions are taken on them.
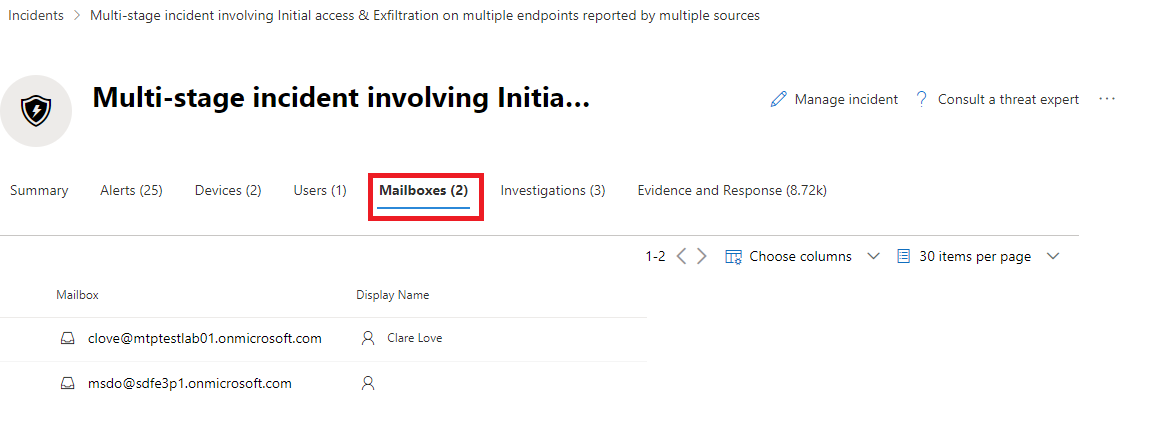
Which tab is present on the incident page when investigating a particular incident?
A. Machines
B. Mailboxes
C. Networks
D. Incidents
Correct Answer: B
Explanation:
Domain : Mitigate threats using Microsoft 365 Defender
Q6 : Insider risk management in Microsoft 365 benefits organizations by addressing internal risks, such as Intellectual Property theft, fraud, sabotage, etc. A credit card database admin’s unencrypted work laptop got stolen at a home in a burglary. Sensitive data for 1000 users was on the laptop. Which type of internal risk is this an example of?
A. Sabotage
B. Data leak
C. IP Theft
D. Regulatory compliance violation
Correct Answer: D
Explanation:
Option D is correct. If a business handles the personal, medical, sensitive, or classified data of individuals or government organizations, the law requires you to follow strict compliance regulations.
Options A and C are incorrect. Sabotage and IP Theft include acting to harm specific individuals, the organization, or the organization’s data systems or daily business operations.
Option B is incorrect. There is a potential data leak situation here. However, there is an internal risk due to actions or non-actions before a leak might occur.
Domain : Mitigate threats using Azure Sentinel
Q7 : You are using Azure Defender and Azure Sentinel to protect your cloud workloads and monitor your environment.
You need to use the Kusto Query Language (KQL) to construct a query that identifies Azure Defender alerts.
What query should you write to meet this requirements? To answer, complete the query by selecting the correct options from the drop down menus.
| where ProductName == “________________________”
A. Azure Security Center
B. Azure Security Sentinel
C. Security Alert
D. Security Events
Correct Answer: A
Explanation:
You should complete the query as follows:
| where ProductName == “Azure Security Center”
This completes a basic query to identify all security alerts in Azure Security Center. Placing SecurityAlert first queries the SecurityAlert table, and then using | where ProductName ==”Azure Security Center” afterwards ensures that in that SecurityAlert table you are only looking for entries where the ProductName column has a value of Azure Security Center.From here, you can expand. For example, you could use KQL to specify time frames or specific devices to query. Kusto Query Language (KQL) is the language you will use when building queries in Azure Sentinel. Queries serve as a way to search through the massive amount of data Azure Sentinel has access to.
You should not begin the query with Azure Security Center. The structure of a query requires that you first identify the key table you will be querying. The SecurityAlert table includes the security alerts that are being digested by Azure Sentinel. You should first query this table, then narrow the search to the alerts coming from the Azure Security Center product.
You should not begin the query with Azure Sentinel. Again, the structure of a query requires that you first identify the key table you will be querying. In this case, that would be the SecurityAlert table. More importantly, while Azure Sentinel is the solution aggregating this data and performing the query, it should not be used as the ProductName. This should be specified as the Azure Security Center.
You should not end the query with Azure Sentinel. As mentioned in the paragraph above, the ProductName (solution source) for the SecurityAlert (alerts) table you should query is Azure Security Center. The query would be run in Azure Sentinel, but do not confuse the solution being queried with the one running the query.
You should not end the query with SecurityAlert. Here you need to name the solution you want to query. In this case, that is Azure Security Center. SecurityAlert would not be a valid ProductName.
Reference: https://docs.microsoft.com/en-us/azure/sentinel/connect-azure-security-center
Domain : Mitigate threats using Azure Sentinel
Q8 : You are threat hunting using Azure Sentinel. You have created a query designed to identify a specific event on your domain controller. You need to create several similar queries because you have multiple domain controllers and want to keep each query separate. The solution should minimize administrative effort.
Which three actions should you perform in sequence to clone a query? To answer, move the appropriate actions from the list of possible actions to the answer area and arrange them in the correct order.
Create a list in the correct order.
-
Choose Clone query by clicking the ellipsis icon at the end of the row.
-
On the Hunting page of Azure Sentinel. Select New query.
-
On the Create Custom query, make your edits then click the Create button.
-
Select the ellipsis in the line of the query you want to modify, and select Edit query.
-
On the Hunting page of the Azure Sentinel, find the query you wish to clone.
A. A->C->E
B. D -> C -> A
C. C -> E -> A
D. E -> A -> C
Correct Answer: D
Explanation:
You should perform the following tasks in order:
- On the Hunting page of Azure Sentinel, find the query you wish to clone.
- Choose Clone query by clicking the ellipsis icon at the end of the row.
- On the Create custom query page, make your edits, then click the Create button.
First, you should find the query you wish to clone. You will do this by navigating to the Hunting page within Azure Sentinel and then looking through the list of queries. This will allow you to ensure the right initial query is cloned in the next step.
Next, you should choose the Clone query option. This is accessible via the ellipsis at the end of the row for the query you found in step one. This will make a copy of the query you identified in the first step and take you to the page where you can make changes to that copy.
Finally, you should make your edits, then click the Create button. These edits will be made on the Create custom query page, which is the page you are taken to after selecting the Clone query in step two. This will allow you to tweak the copy to your needs. When you click Create, the initial query you copied will still exist in its original state, and a new query with the changes you make in this step will be generated/saved.
This process would allow you, for example, to alter the IP or hostname in the query to match your other domain controllers (DCs) but keep the rest of the query the same. As mentioned above, it also leaves the original query untouched/as-is. This is a fast, efficient way to make several related queries but require minor tweaks to meet the desired outcome. Starting each query from scratch would take much longer and would be more likely to result in human error in the query syntax.
You should not select New query on the Hunting page of Azure Sentinel. While this option could ultimately be chosen to generate the queries for your other DCs, you would be starting from scratch, as mentioned above. If you only need to change a few minor things in your query, going to New query is a waste of time as the clone option gives you a better starting point.
You should not select the ellipsis in the line of the query you want to modify and select the Edit query. This would allow you to edit an existing query, but it would not create a copy of it. Any edits made here would alter the original query. With the Clone query option, you leave the original unaltered while efficiently creating new queries based on it.
Reference: https://docs.microsoft.com/en-us/azure/sentinel/hunting
Domain : Mitigate threats using Azure Defender
Q9 : By which of the following Azure Defender’s main role can be described?
A. Cloud configuration management
B. Cloud security posture management
C. Cloud workload protection
D. Cloud Security Management
Correct Answer: C
Explanation:
Azure Defender is for Cloud workload protection, not for Cloud Security posture, security, and configuration management. Hence, only option C is correct.
Options A, B, and D are incorrect.
Reference: https://docs.microsoft.com/en-us/azure/security-center/azure-defender
Domain : Mitigate threats using Azure Defender
Q10 : Which selection helps you ensure Azure Defender is enabled over all the resources in a Subscription?
A. Continuous assessments
B. Coverage type
C. Automatic provisioning
D. Azure Arc
Correct Answer: C
Explanation:
Option C is correct as Automatic provisioning will install the required agent for the resources.
Options A & B are incorrect as such feature is not present under Continuous assessments and coverage.
Reference: https://docs.microsoft.com/en-us/azure/security-center/azure-defender
Domain : Mitigate threats using Azure Defender
Q11 : You are a SOC (Security Operations Center) Analyst working at a company that is in the process of deploying cloud workload protection with Azure Defender.
You are the SOC team member working with the application and infrastructure teams to architect the resource architecture for the new web application that uses containers and Azure SQL. You are accountable for ensuring the workloads are secure with Azure Defender and offer options for non-protected workloads.
Which attribute of Azure Defender inspects registries and files of application software, operating system, and others for any changes that might point out an attack?
A. File integrity monitoring
B. Adaptive application controls
C. Adaptive network hardening
D. Log Inspection
Correct Answer: A
Explanation:
Option A is correct. File integrity monitoring examines files.
Option B is incorrect. This option is related to Applications.
Option C is incorrect. This option is related to Network Security Groups.
Option D is incorrect. This option is not related to Azure Defender.
Reference: https://docs.microsoft.com/en-us/azure/security-center/azure-defender
Domain : Mitigate threats using Azure Defender
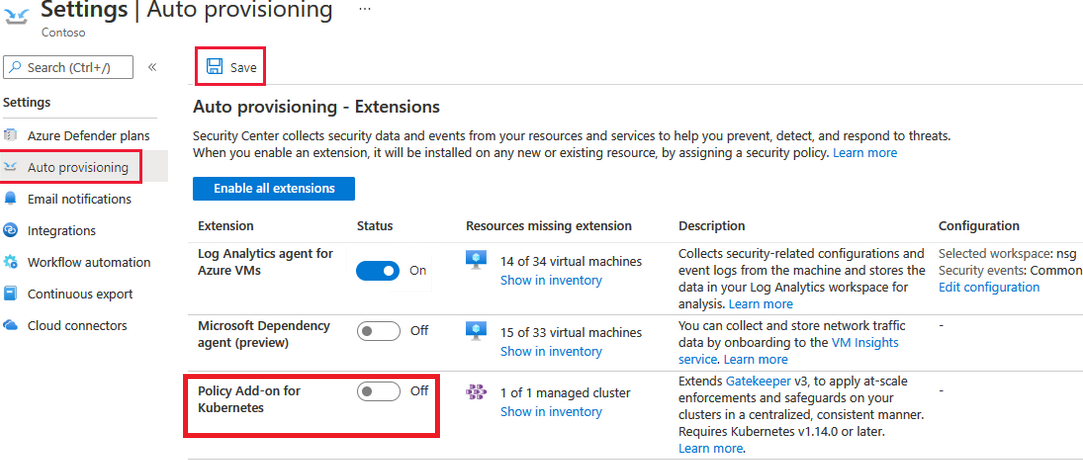
Q12 : You are a SOC Analyst for company XYZ that is deploying cloud workload protection with Azure Defender. Your work is to ensure Azure Defender automatically protects the Azure resources. Your organization has a small number of Azure virtual machines that are not part of the auto-provisioning scheme. You must manually configure protection for these Azure resources.
Which of the below is an extension of auto-provisioning?
A. Windows Events
B. Policy for Azure Policy
C. Policy Add-on for Kubernetes
D. Policy for DNS
Correct Answer: C
Explanation:
Option C is correct as we get to provision policies for Kubernetes under the settings tab.
Options A, B and D are incorrect as we don’t get them to provision automatically using Security Center.
Reference: https://docs.microsoft.com/en-us/azure/security-center/azure-defender
Domain : Mitigate threats using Azure Sentinel
Q13 : You are a SOC Analyst employed at a company that has set up cloud workload protection with Azure Defender. You are in charge of remediating security alerts created by Azure Defender detections.
You get an alert regarding a container; the alert offers information to manually remediate the issue and what you can do in the future to stop further attacks. You work with the infra team to resolve the issue. The infrastructure team provides recommendations for making automated remediation tasks for future alerts regarding the same problem.
You are requested to provide a report containing tools, tactics and procedures. Which of the following feature will you use to leverage to do the same?
A. Incident
B. Threat Intelligence
C. Secure Score
D. Threat Score
Correct Answer: B
Explanation:
Option B is correct. The threat intelligence report contains attacker information if available.
Options A, C, and D are incorrect as we don’t have the feasibility of downloading the report.
Reference: https://docs.microsoft.com/en-us/azure/security-center/security-center-threat-report
Domain : Mitigate threats using Microsoft 365 Defender
Q14 : You need to give a manager, [email protected], the ability to read events in the security center, but prevent them from making any changes. Which command should you use?
A. Add-MsolRoleMember -RoleName “Security Administrator” -RoleMemberEmailAddress [email protected]
B. Add-MsolRoleMember -RoleName “Security Reader” -RoleMemberEmailAddress [email protected]
C. Add-MsolRoleMember -RoleName “Global Administrator” -RoleMemberEmailAddress [email protected]
D. Add-MsolRoleMember -RoleName “Global Reader” -RoleMemberEmailAddress [email protected]
Correct Answer: B
Explanation:
Option B is correct. Read-only access is granted to users with a Security Reader role in Azure AD. Always follow the principle of least privilege.
Option A is incorrect. A security administrator can read security information and reports and manage configuration.
Option C is incorrect. A global admin can manage all aspects of Azure and Microsoft services that use Azure identities.
Option D is incorrect. A global reader can read everything that a Global Administrator can.
Reference: https://docs.microsoft.com/en-us/microsoft-365/security/defender-endpoint/rbac?view=o365-worldwide
Domain : Mitigate threats using Azure Defender
Q15 : If you have a security recommendation that is not applicable for your environment, and you don’t want to negatively affect your secure score, which option is the most appropriate to use?
A. Create an exemption for the recommendation
B. Disable the recommendation
C. Create a new resource group and exempt the recommendation from the resource group
D. Create a custom recommendation
Correct Answer: B
Explanation:
Option B is correct. It is recommended for disabling recommendations when they’re inapplicable in your environment.
Options A, C & D are incorrect. It is not possible and appropriate to do them.
Reference: https://docs.microsoft.com/en-us/azure/security-center/security-center-recommendations
Domain : Mitigate threats using Azure Defender
Q16 : When configuring GCP Connector in Azure Defender, which component is mandatory to have already configured in GCP?
A. GCP Security Command Center
B. Security Hub
C. Google Cloud Console API
D. All the options above
Correct Answer: A
Explanation:
Option A is correct. The integration of GCP in Azure Defender leverages Google Security Command Center and is required for data to be available.
Option B,C & D are incorrect. These are later steps when configuring the GCP connector in Azure Defender.
Reference: https://docs.microsoft.com/en-us/azure/security-center/quickstart-onboard-gcp
Domain : Mitigate threats using Azure Defender
Q17 : When reviewing Just-in-Time VM access, you noticed that some VMs appear under “Not Applicable”. What are the reasons that must be present for a VM to be considered not applicable?
A. The VM is not assigned to a network security group
B. The VM is not protected by a Firewall
C. The VM has JIT already enabled
D. VM has been deployed through ARM (Azure Resource Manager)
Correct Answers: A and B
Explanation:
Options A & B are correct.
JIT is not supported on VMs where:
It is missing a network security group (NSG) or Azure Firewall.
Deployed as classic VM – JIT only supports VMs deployed through ARM, not ‘classic deployment’. Hence, Option D is incorrect.
Other – Your VM might be in this tab if the JIT solution is disabled in the security policy of the subscription or the resource group.
Option C is incorrect. JIT is already enabled.
Reference: https://docs.microsoft.com/en-us/azure/security-center/just-in-time-explained
Domain : Mitigate threats using Azure Defender
Q18 : What capabilities given below are part of Azure Defender for Servers?
A. Adaptive Application Control
B. Integration with Qualys for Vulnerability Assessment
C. Adaptive Network Hardening
D. Fileless attack detection for Windows
E. Vulnerability assessment for Azure Container Registries
Correct Answers: A, B, C and D
Explanation:
Options A, B, C and D are correct. They are capabilities of Azure Defender.
Option E is incorrect as it is not a feature of Azure Defender.
Reference: https://docs.microsoft.com/en-us/azure/security-center/defender-for-servers-introduction
Domain : Mitigate threats using Azure Sentinel
Q19 : Azure Sentinel for SAP only supports cloud-based implementations of SAP.
A. True
B. False
Correct Answer: B
Explanation:
Domain : Mitigate threats using Azure Sentinel
Q20 : Which of the following APIs should be used to assist with managing content through a CI/CD pipeline?
A. Security Graph API
B. Query API
C. Azure Sentinel Management API
D. Threat intelligence API
Correct Answer: C
Explanation:
Option C is correct. Azure Sentinel API can be used in CI/CD pipeline for content management.
Option A is incorrect. The Microsoft Graph Security API is an intermediary service (or broker) that provides a single programmatic interface to connect multiple Microsoft Graph Security providers (also called security providers or providers).
Option B is incorrect. Query API sends a query to the service.
Option D is incorrect. Threat intelligence API is responsible for threat intelligence feeds and data.
Reference: https://techcommunity.microsoft.com/t5/azure-sentinel/azure-sentinel-api-101/ba-p/1438928
Domain : Mitigate threats using Azure Sentinel
Q21 : What does the “h” in front of a string literal such as h’my string’ mean?
A. The string is considered hot path data
B. The string is a hyperlink
C. The string is obfuscated
D. Nothing – this character is always ignored
Correct Answer: C
Explanation:
Option C is correct. An obfuscated string literal can be formed by taking a “regular” string literal and prepending an h or an H character in front of it.
Options A, B, and D are incorrect as ‘h’ is used only for obfuscation.
Reference: https://docs.microsoft.com/en-us/azure/data-explorer/kusto/query/scalar-data-types/string
Domain : Mitigate threats using Azure Sentinel
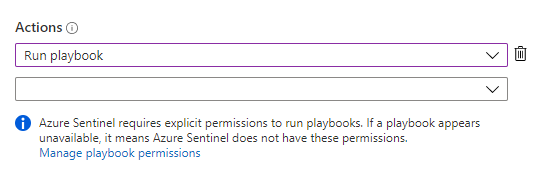
Q22 : Additional permissions are required to launch a playbook from automation rules.
A. True
B. False
Correct Answer: A
Explanation:
Option A is correct. Azure Sentinel requires explicit permissions to run playbooks.
Option B is incorrect. If playbook shows unavailable, it means that Azure Sentinel does not have these permissions.
Reference: https://docs.microsoft.com/en-us/azure/sentinel/tutorial-respond-threats-playbook
Domain : Mitigate threats using Azure Sentinel
Q23 : Which of the following data connectors have automation support in the Azure Sentinel PowerShell Module, Az.SecurityInsights?
A. Dynamics 365
B. Cisco ASA
C. AWS Cloudtrail
D. Office 365
E. Azure Active Directory
Correct Answers: C, D and E
Explanation:
All supported data connectors are:
| Name | Description |
| AADDataConnector | Represents AAD (Azure Active Directory Identity Protection) |
| AATPDataConnector | Represents AATP (Azure Advanced Threat Protection) |
| ASCDataConnector | Represents ASC (Azure Security Center) |
| AwsCloudTrailDataConnector | Represents Amazon Web Services CloudTrail |
| MCASDataConnector | Represents MCAS (Microsoft Cloud App Security) |
| MDATPDataConnector | Represents MDATP (Microsoft Defender Advanced Threat Protection) |
| OfficeDataConnector | Represents Office 365 |
| TIDataConnector | Represents threat intelligence data |
Domain : Mitigate threats using Azure Sentinel
Q24 : In the query
“extend ProcessEntropy = -log2(PCoHValue/TPCoHValue)*(PCoHValue/TPCoHValue)”
PCoHValue means the ProcessCountOnHost value.
A. True
B. False
Correct Answer: A
Explanation:
Entropy calculation is used to help identify Hosts where they have a high variety of processes (a high entropy process list on a given Host over time). This helps us identify rare processes on a given Host. Rare here means a process that shows up on the Host relatively few times in the last 7days.
Domain : Mitigate threats using Azure Sentinel
Q25 : Which of the following are valid parsers in the ASIM?
A. Source-agnostic
B. All of the options listed
C. Source-explicit
D. source-gnostic
Correct Answer: A
Explanation:
Option A is correct. ASIM includes two levels of parsers: source-agnostic and source-specific parsers.
Options B, C & D are incorrect. These parsers are invalid.
Reference: https://docs.microsoft.com/en-us/azure/sentinel/normalization-about-parsers
Summary
If you spend more time on the above SC-200 questions which have detailed explanations, you will become very confident on trying out your real exams. But still, it is recommended to take the SC-200 practice tests before starting your actual certification journey. Practice tests can help you in assessing your skill gaps clearly, in which you can re-learn and fill-in such gaps before attempting the actual exams.
Hope you have enjoyed these questions. Stay tuned to this blog for more updates!
- Which AWS Certification is Best For Developers - December 5, 2023
- Top Popular Hands on Labs for Google Cloud Platform (GCP) - October 29, 2023
- 7 Exam Tips for Google Cloud Database Engineer Certification - September 21, 2023
- What Is Azure Web Application Firewall (WAF)? - September 8, 2023
- The 5 Best Team Chat Apps for Business in 2024 - August 10, 2023
- What is Microsoft Cybersecurity Reference Architectures? - July 31, 2023
- How to Secure & Migrate your SAP Environment on AWS - July 26, 2023
- A Comparison of SUM-DMO and SWPM - July 21, 2023


Question 9 is partially correct (Q9 : By which of the following Azure Defender’s main role can be described?). If you follow the link you have listed, Microsoft says this on the first line, “Microsoft Defender for Cloud is a Cloud Security Posture Management (CSPM) and Cloud Workload Protection Platform (CWPP)…” It should be B and C (Cloud security posture management & Cloud workload protection).