In today’s digital world, the volume and complexity of cybersecurity threats and attacks are continuously increasing. Endpoints, such as desktops, laptops, mobile devices, and servers, have become prime targets for cybercriminals. This is often due to the vulnerabilities and potential carelessness of end users.
Endpoint security is paramount in protecting organizations from these evolving threats. Choosing endpoint security solutions, like Microsoft Defender for Endpoint, play a crucial role in defending against these threats.
In this comprehensive blog post, we just take an overview of the features and capabilities of Microsoft Defender for Endpoint, equipping you with the knowledge to defend your organization’s security posture.
Let’s dive in and unlock the full potential of Microsoft Defender for Endpoint!
What is Microsoft Defender for Endpoint?
Microsoft Defender for Endpoint, formerly termed as Microsoft Defender Advanced Threat Protection is an enterprise-level protection platform. Through this platform, we can detect, prevent, investigate, and respond to the threats and risks that persist in enterprise networks.
To ensure the protection of the enterprise application, the Microsoft Defender for Endpoint employs some of the technologies, which may include:
- Endpoint behavioral sensors: It gathers and analyzes behavioral signals from the Windows 10 operating system, which are then securely transmitted to a dedicated and confidential cloud environment running Microsoft Defender for Endpoint.
- Cloud analytics: Through the utilization of cutting-edge technologies such as machine learning and advanced data analytics, Microsoft converts these behavioral signals into actionable threat detections, valuable insights, and recommended countermeasures.
- Threat Intelligence: To enhance its capabilities, Microsoft’s security teams and threat hunters leverage comprehensive threat intelligence collected from various sources, including ecosystem-wide data and partner contributions. This enriched threat intelligence empowers Defender for Endpoint to identify attacker tactics, techniques, and procedures (TTPs), enabling the generation of timely alerts and proactive responses.
Microsoft Defender for Endpoint: Architecture
The key components of the Microsoft Defender for Endpoint are:
Admin portal: The administration portal provides a centralized interface for monitoring endpoints, identifying security incidents, and taking appropriate actions to respond to them effectively.
Attack Surface Reduction (ASR): It evaluates attack surfaces and enforces specific rules aimed at minimizing the potential for attacks on endpoints.
Endpoint Detection and Response (EDR): EDR enables real-time detection of ongoing attacks and facilitates immediate response actions directly on the affected endpoint devices.
Behavioral blocking and containment: This feature utilizes behavioral analysis on endpoints to identify threats, even when attacks are already underway, and implements measures to contain and mitigate them.
Automated investigation and response: By employing various inspection and analysis techniques, this functionality prioritizes alerts and executes automated responses, improving incident response efficiency.
Advanced threat hunting: Through a query-based tool, advanced threat hunting enables proactive exploration of historical data from the past month to identify threat indicators and potential threat actors in the environment.
Threat analytics: Microsoft security experts compile reports on recent high-impact threats, providing valuable insights and analysis to enhance overall threat awareness and response capabilities.
Microsoft Defender for Endpoint: Features and Capabilities
In general, the Microsoft Defender for Endpoint is broken into two plans: Plan 1 and Plan 2.
You might think why it has been partitioned. The underlying reason for this partition such as:
Initially, the original version of Defender for Endpoint provided a comprehensive cybersecurity solution tailored for large enterprises with stringent security requirements. However, this extensive feature set made it less appealing and cost-effective for smaller companies that didn’t require all the functionalities.
To address this, Microsoft introduced a more accessible option called Plan 1, offering a subset of features suitable for smaller organizations. As a result, a broader range of organizations can now benefit from Defender for Endpoint. Moving forward, the full-featured version will be referred to as Plan 2, providing a clear distinction between the two offerings.
What will be included in Microsoft Defender for Endpoint Plan 1?
Plan 1 includes Microsoft 365 Defender portal, a comprehensive platform that empowers your security team to access up-to-date information regarding detected threats.
Through this portal, your team can promptly respond to threats by implementing suitable mitigation measures and centrally managing your organization’s threat protection settings. This centralized approach enhances the efficiency of threat management and allows for effective coordination of security efforts across your organization.
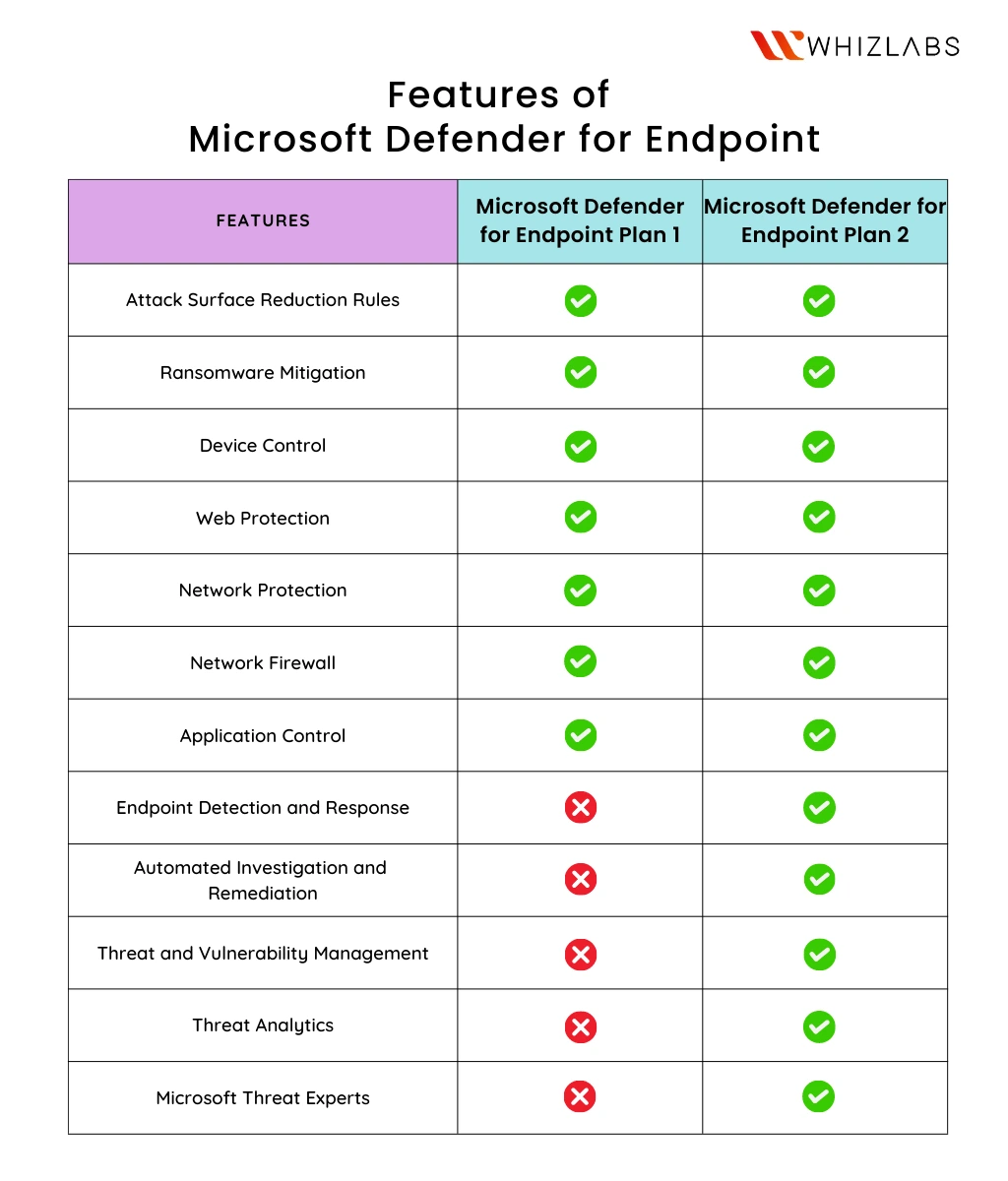
Features of Microsoft Defender for Endpoint: Plan 1
Here are some features included in the Microsoft Defender for Endpoint Plan 1:
Attack Surface Reduction Rules: Defender for Endpoint implements measures to minimize the attack surface of your systems by identifying and blocking software behaviors commonly associated with malware. While these behaviors may have legitimate uses, their prevalence in malicious code makes them potential avenues for attacks. By preventing these behaviors from running, Microsoft Defender for Endpoint reduces the potential attack surfaces and enhances your system’s security.
Ransomware Mitigation: To protect your data from ransomware attacks, Microsoft Defender for Endpoint enables you to control which processes have access to critical folders. Limiting unauthorized access, prevents ransomware from taking over important files and holding them hostage, ensuring the integrity of your data.
Device Control: Microsoft Defender for Endpoint helps mitigate the threat of malicious code being introduced through unauthorized peripherals such as USB drives. By restricting access to these devices, it prevents potential malware from infiltrating your systems, reducing the risk of security breaches.
Web Protection: Microsoft Defender for Endpoint offers web protection to safeguard against various online threats. It automatically blocks access to known malicious websites, including phishing sites and exploit sites. Additionally, you can customize web access by blocking specific categories of risky sites, such as adult content or leisure sites that may impact productivity, further enhancing your organization’s security.
Network Protection: Building upon web protection, network protection extends security measures to the operating system level. It prevents applications from secretly accessing the internet and potentially causing harm to your machine. This comprehensive protection ensures that your internet-enabled applications and the overall system remain secure.
Network Firewall: Microsoft Defender for Endpoint provides a network firewall that allows you to exert greater control over incoming and outgoing network traffic. By creating and implementing custom rules, you can reduce the risk of network security threats and protect sensitive data by regulating the flow of network communications.
Application Control: To encounter the threat posed by malicious applications, Microsoft Defender for Endpoint offers application control capabilities. It allows you to limit the execution of applications on your system based on various criteria, such as code-signing certificates, application reputation, and launching process. This control mechanism ensures that only trusted applications are allowed to run, reducing the risk of cyberattacks.
What will be included in Microsoft Defender for Endpoint Plan 2?
Microsoft Defender for Endpoint Plan 2 includes everything in Plan 1 but it has some additional features as follows.
Features of Microsoft Defender for Endpoint: Plan 2
Here are some features included in the Microsoft Defender for Endpoint Plan 2:
Endpoint Detection and Response: Microsoft Defender for Endpoint delivers advanced threat protection by effectively detecting, investigating, and responding to threats that have managed to bypass initial security measures. It empowers users with a query-based tool to proactively uncover breaches and create custom automatic detections to enhance threat identification.
Automated Investigation and Remediation: While alerting human operators about potential threats is crucial, it still leaves room for threats to persist until a manual intervention occurs. With Microsoft Defender for Endpoint’s automated investigation and remediation capabilities, threats can be swiftly shut down within minutes, minimizing their impact and reducing response time.
Threat and Vulnerability Management: Within large organizations, the responsibility for threat detection and remediation is often distributed among multiple teams. Threat and vulnerability management in Microsoft Defender for Endpoint enables improved coordination among these teams, akin to how project management tools enhance productivity. This streamlined collaboration enhances response time, allowing for more efficient threat mitigation.
Threat Analytics: Leveraging the power of big data, advanced algorithms in Microsoft Defender for Endpoint can detect patterns that may go unnoticed by humans and automatically respond to them. The comprehensive threat analytics captured by Defender for Endpoint provides the necessary data to identify threats swiftly and generate alerts faster, enhancing overall threat detection capabilities.
Microsoft Threat Experts: Defender for Endpoint Plan 2 offers access to Microsoft’s team of skilled threat experts. Users can engage directly with these experts through the Defender Security Center, receiving timely and accurate answers to security queries. Additionally, users benefit from managed threat monitoring and analysis services, ensuring quicker alerts for security threats that manage to evade other defense mechanisms.
Also know : New Microsoft Azure Certifications Path in 2023 [Updated]
Microsoft Defender for Endpoint: Pros and Cons
Here are some Pros and Cons of the Microsoft Defender for Endpoint solution.
Pros
- The free Basic edition of Microsoft Defender is available for all Windows endpoints.
- It offers extensive compatibility with various endpoints, including Windows 10, Windows Server, Linux, macOS, iOS, and Android.
- With a single license, you can protect multiple Microsoft solutions such as Exchange Online, SharePoint, Microsoft Teams, OneDrive, Azure Active Directory (AD), and Azure Identities.
- Microsoft Defender is mapped against the MITRE ATT&CK knowledge base, enabling it to detect indicators of compromise (IoC) based on MITRE definitions.
- By leveraging billions of signals gathered from Office 365 applications, Microsoft Defender enhances its threat intelligence and detection capabilities.
- It generates a graphical attack timeline that consolidates all relevant data associated with a particular attack, aiding in comprehensive threat analysis.
- Advanced threat hunting is facilitated through the use of the KQL (Kusto Query Language) query language, empowering users to perform in-depth investigations.
- The system retains log data for 180 days, ensuring extensive historical data for analysis and forensic purposes.
Cons
- Currently, web filtering is not available for macOS in Microsoft Defender for Endpoint.
- Microsoft has introduced a simplified onboarding process for macOS endpoints using Microsoft Intune. Previously, it required configuring multiple profiles, but now it can be deployed as an app, streamlining the setup process. However, for older macOS Sierra versions using the older extensions, the onboarding process still requires multiple steps to onboard to Microsoft Defender for Endpoint.
- Integration of the Microsoft Cloud app into the new dashboard of Microsoft Defender for Endpoint is necessary to enhance the overall user experience and provide seamless access to Microsoft Cloud services.
- Efforts are being made to reduce the memory overhead of the mdatp agent running on Linux systems, aiming to optimize performance and resource utilization.
FAQs
What are the characteristics of Defender for endpoint servers?
Defender for Servers and Defender for Endpoint offers robust features for threat detection and protection at the operating system (OS) level. These solutions excel at identifying and mitigating various types of threats, including virtual machine behavioral detections and fileless attacks.
What are the advantages of Microsoft Defender for Endpoint?
Microsoft Defender for Endpoint offers several advantages that enhance endpoint security and protect against various threats. Some of these advantages include web and network protection to ensure protection for web-based applications.
Which type of tool is Microsoft Defender?
Microsoft Defender is a comprehensive security solution offered by Microsoft. It is designed to provide protection against various cyber threats and attacks. Microsoft Defender includes multiple tools and services that work together to detect, prevent, investigate, and respond to security incidents.
How does Microsoft Defender work?
When operating in active mode, Microsoft Defender Antivirus functions as the primary antivirus application on the device. It conducts file scans, addresses identified threats, and logs detected threats in your organization’s security reports and within the Windows Security app.
Conclusion
Hope this article has provided an overview of Microsoft Defender for Endpoint, highlighting its key features, architecture, benefits, and considerations. As a comprehensive security solution, Microsoft Defender for Endpoint offers robust protection against various threats, including malware, ransomware, and advanced attacks.
If you are looking to further enhance your knowledge about Microsoft Defender for Endpoint at a basic level, then taking the AZ-900 exam will be a great choice.
By clearing the AZ-900 exam, you can deepen your knowledge of Azure’s core services, security features, and management tools, which are essential components of Microsoft Defender for Endpoint. This certification can serve as a valuable credential, demonstrating your expertise in Azure fundamentals and showcasing your commitment to staying updated with the latest technologies in endpoint security.
Apart from nurturing your theoretical knowledge, it is essential to focus on practical skills via hands-on labs and sandboxes.
If you have any queries on this blog post, feel free to comment to us!
- Top 20 Questions To Prepare For Certified Kubernetes Administrator Exam - August 16, 2024
- 10 AWS Services to Master for the AWS Developer Associate Exam - August 14, 2024
- Exam Tips for AWS Machine Learning Specialty Certification - August 7, 2024
- Best 15+ AWS Developer Associate hands-on labs in 2024 - July 24, 2024
- Containers vs Virtual Machines: Differences You Should Know - June 24, 2024
- Databricks Launched World’s Most Capable Large Language Model (LLM) - April 26, 2024
- What are the storage options available in Microsoft Azure? - March 14, 2024
- User’s Guide to Getting Started with Google Kubernetes Engine - March 1, 2024