Microsoft Defender for Cloud is a cloud security solution whose major role is to provide visibility and protection to an organization’s cloud environment. The solution is accessible through the Microsoft Azure portal and presents a key examinable component of the Microsoft Certified Azure Security Engineer Associate, covering 25-30% of the latest examinable components. For a better understanding of the concepts, it is recommended to read this blog alongside guidance provided in the Microsoft Azure Security Certification Guide.
Benefits of Microsoft Defender for the Cloud
Detailed below are some benefits of deploying Microsoft Defender for Cloud as part of an organization’s cloud security ecosystem:
- Improved security: The solution can be deployed to perform security assessments in the entire cloud environment, including all deployed resources, to determine the health of the entire cloud environment of the organization. Provides recommendations and valuable information that security professionals can adopt to improve cloud security in an organization.
- Enhanced protection against threats: Microsoft Defender for Cloud provides protection against emerging threats by continuously assessing the deployed cloud workloads and providing recommendations to address the loopholes identified. It also provides security alerts, which allow security professionals to act in a timely manner in remediating the identified cloud security threats.
- Improved Environment Fortification: It should be noted that Microsoft Defender for Cloud is built natively in Microsoft Azure, thus allowing its quick deployment of the tools to address threats in the cloud environment. This process ensures the existence of a resilient cloud security infrastructure in the organization.
Microsoft Defender for Cloud Features
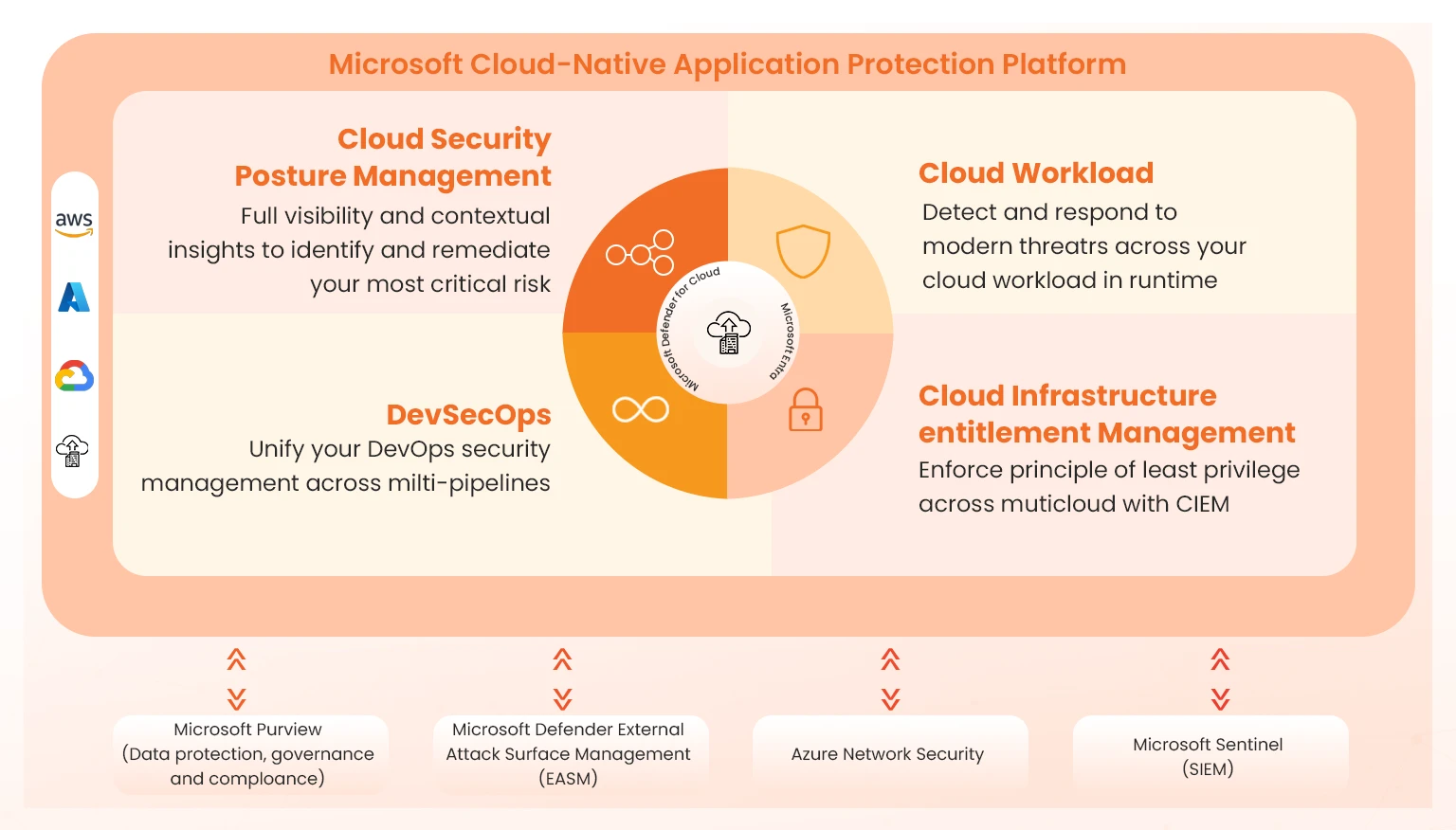
There are a variety of features that make up the Microsoft Defender for Cloud solution, and all these helps strengthen the security of the organization’s cloud data and workloads. The Microsoft Certified Azure Security Engineer Associate candidate should grasp the Cloud Native Application Protection (CNAPP) nature of Microsoft Defender for Cloud as a solution. A CNAPP merges a variety of independent cloud security tools with a single holistic platform, as shown in the figure below;
As depicted in the above diagram, Microsoft’s unified CNAPP includes:
- Unified security management: Microsoft Defender for Cloud providers an organization with merged and unified cloud infrastructure. It provides visibility of both cloud and on-premise resources, allowing organizations to better focus their cloud security control initiatives, enhancing the security of cloud resources. This consolidation of monitoring activities into a single platform allows security professionals to have a holistic view of the cloud environment and fine-tune their security management initiatives.
- Cloud Security Posture Management (CSPM): Cloud misconfiguration is one of the most common causes of cloud security breaches; hence, the deployment of the Microsoft Defender for Cloud application should lead to an improved cloud security posture of an organization. CSPM assists organizations in managing and enforcing security policies as well as in discovering and addressing misconfigurations. The secure score, which forms part of CSPM, allows an organization to evaluate the overall Azure security status and ensure optimum cloud security. Users can also monitor the security of cloud resources by leveraging Microsoft’s global threat intelligence ecosystem.
- Cloud Infrastructure Entitlement Management (CIEM): CIEM is the integration between Microsoft Defender for Cloud and Microsoft Entra Permissions Management for the purpose of managing and managing an organization’s user entitlements in the cloud. CIEM enforces that users adhere to the Principle of Least Privilege (PoLP). The PoLP stipulates that users or workload identities, such as applications and services, should be provisioned with only the least amount of access necessary to perform their tasks. This approach leads to a significant reduction in the attack surface and a consequent reduction in cloud security threats.
- Cloud Workload Protection (CWP): This Microsoft Defender for Cloud feature protects a variety of cloud resources. This functionality protects the cloud workloads and applications of the organization and is composed of various functions such as threat detection and vulnerability management. It can also provide advanced threat protection for the organization’s on-premise environment, thus ensuring comprehensive security coverage.
- DevSecOps: The DevSecOps feature consists of a central console that assists in the protection of applications and resources from code to cloud across multiple Continuous Deployment/Continuous Integration (CD/CI) pipeline environments. These multiple pipeline environments include GitHub. With the implementation of DevSecOps, security professionals have clear visibility into the entire DevSecOps environment that enables them to strategy security intervention. Infrastructure-as-Code (IaC) templates and container images can also be configured to minimize cloud misconfigurations extending into the production environment. Microsoft Defender for Cloud Integrations.
Microsoft Defender for Cloud is typically integrated with the features detailed below, thus further enhancing its effectiveness.
- External Attack Surface Management (EASM): The EASM capability performs external attack surface management and scans on multicloud environments for security threats. The feature is integrated with CSPM by default; therefore, its use does not require a separate license and takes advantage of Microsoft’s crawling technology to discover and scan digital assets of an organization online. Through this scanning process, a security professional can discover new risky connections and promptly rectify them. EASM also generates attack surface information that highlights critical information related to an organization’s cloud environment. Armed with this information, cloud security teams can identify and prioritize risks and eliminate threats.
- Azure network security: Azure Network Security performs a continuous assessment of Azure network resources against specified principles such as Zero Trust. It provides organizations with granular segmentation, intelligent threat protection, and traffic encryption, features that enhance cloud security. It can also provide private access links between an organization’s cloud infrastructure and its on-premise network resources, as well as the necessary recommendations to improve cloud network security.
- Microsoft Purview: Microsoft Purview is one of the crucial components of Microsoft Defender for Cloud and its major role is to assess the extent of regulatory compliance in the organization. It provides information on the requirements of a variety of industry standards, such as ISO/IEC 27001:2022, SOC 2, and PCI-DSS and assesses the organization’s level of compliance with such frameworks. It also offers actionable recommendations that allow an organization to meet requirements and maintain compliance.
Microsoft Defender for Cloud Security Best Practices
The Microsoft Certified Azure Security Engineer Associate should understand the important contribution that implementing sound security practices within Microsoft Defender for Cloud makes in ensuring the integrity, confidentiality, and availability of critical data and applications. This also improves the cybersecurity processes of an organization. The following are some best security practices for implementation.
- Implement the Principle of Least Privilege (POLP): Enforce the principle of least privilege, which involves granting users the minimum permissions necessary to perform their specific tasks. Also, use role-based access control (RBAC) to assign granular permissions to cloud users, as this helps reduce the attack surface.
- Implement multifactor authentication (MFA): Implement and enforce mandatory MFA for all user accounts that access cloud resources. This security approach can lead to a significant reduction in the risk of unauthorized access, even where credentials are compromised.
- Implement Zero-Trust access: Implement a Zero-Trust security model that requires continuous verification for all accesses, irrespective of the entity’s location and network origin. The environment should be configured in such a way that access is only granted after a successful verification process has been completed.
- Implement resource hardening: Implement Microsoft Defender for Cloud’s built-in security recommendations on all the organizations connected cloud resources. The advantage of resource hardening is that it addresses common cloud vulnerabilities without incurring additional effort and resources.
- Monitor configurations: Establish and continuously monitor cloud security baselines for all cloud resources of the organization. These security baselines should help security professionals detect and rectify any deviations. An organization can also implement other Azure monitoring solutions such as Azure Policy and Azure Monitor to ensure effective cloud security monitoring and prompt correction of identified misconfigurations.
- Just-in-Time (JIT) access: Use Just-in-Time (JIT) to limit access to sensitive organizational resources and reduce incidents of breaches by granting temporary access only when needed and automatically revoking such access immediately afterwards.
- Implement incident response: Regardless of the perceived resilience of an organization’s cloud technological controls provided by Microsoft for the Cloud, sometimes incidents occur unexpectedly. Therefore, it is imperative for security professionals to establish and operate an incident response plan (IRP) to provide guidance in such situations. The IRP should be regularly evaluated and tested to ensure its effectiveness in the handling of security incidents.
- Implement cybersecurity hygiene: Cybersecurity hygiene refers to the security technique that ensures that clous users practice security on a personal level to ensure the security and overall security of the organization’s cloud system. The advantage of cloud security hygiene processes is that they are preventive which assists in the reduction of costs. Cloud security hygiene actions include:
- Establishing the level of privileges for individuals based on defined roles to prevent privilege creep.
- Regular review and update of access controls to ensure that they remain relevant.
- Regularly installing security patches in the cloud
- Extending organizational security controls to the organization’s third parties.
Conclusion
As discussed in this log, safeguarding the Azure cloud environment requires a strategic approach. Microsoft Defender for Cloud delivers a host of sophisticated inbuilt controls meant to secure Azure cloud environments. The concepts covered in this log are crucial in assisting students pass the Microsoft Certified Azure Security Engineer Associate exam and become involved in the improvement of the overall security set-up of the organization. It also assists in fostering a culture of security resilience in an organization. Try our Hands-on labs to gain real-time experience that helps you in boosting your knowledge and ace the certification.
- How to Enable CORS for Azure Functions? - January 24, 2025
- How Microsoft Entra ID Simplify Developer Authentication? - January 21, 2025
- What Role Does Azure Redis Cache Play in Reducing Latency? - December 27, 2024
- Master Cloud Management with Azure Resource Architecture - December 2, 2024
- Microsoft Defender: Your Key to Azure Security Management - November 26, 2024
- What is Microsoft Entra ID and How It Enhances Security - November 26, 2024
- How to Build Secure Networks with Azure Virtual Networking - November 20, 2024
- Step-by-Step Nginx Deployment on Azure Kubernetes Service - November 13, 2024