Planning to take AZ-801:Configuring Windows Server Hybrid Advanced Services Certification? Then you must have pratical skills to gain confidence in passing the exam.
We have compiled 20+ free AZ-801 practice questions to provide you with complete knowledge on configuring Windows Server. These practice exam questions looks alike practice questions in the real exam format.
Once you become familiar with the AZ-801 exam pattern and difficulty, you’re in a perfect position to ace your exam at first time. AZ-801 practice exams help you to identify your strengths and weaknesses so that you know where to focus your study when preparing for your AZ-801 certification exam.
What is AZ-801:Configuring Windows Server Hybrid Advanced Services Certification?
AZ-801:Configuring Windows Server Hybrid Advanced Services certification intends mainly for IT professionals who excel in managing and operating hybrid environments that integrate Windows Server and Azure. AZ-801 practice questions are designed to evaluate the candidate’s expertise in various aspects of Windows Server hybrid services, including configuring and managing Azure services, implementing robust Azure security, optimizing Azure solutions, and managing hybrid identities.
By preparing diligently and mastering critical topics such as Azure virtual machines, Azure Active Directory, Azure networking, and more, candidates can position themselves for success and achieve their career goals.
Read More : Preparation Guide for AZ-801: Configuring Windows Server Hybrid Advanced Services Certification exam
Domain: Secure Windows Server On-premises and Hybrid Infrastructures
Question 1 : You have an Azure VM named VM2 that runs Windows Server. You are planning the deployment of a new LOB (line-of-business) application to VM2. You must ensure that the application is not capable of creating the child processes. What would you configure on VM2?
A. Microsoft Defender SmartScreen
B. Microsoft Defender Credential Guard
C. Exploit Protection
D. Microsoft Defender Application Control
Correct Answer: C
Explanation:
Exploit protection helps in protecting against malware that utilizes exploits to infect devices and spread. It consists of several mitigations that you can apply to either the operating system (OS) or individual apps. Exploit Protection also allows users to block particular applications from creating the child processes or executing Win32k system calls.
Option A is incorrect. Microsoft Defender SmartScreen helps you in identifying reported phishing and malware websites and making informed and wise decisions about downloads.
Option B is incorrect. It utilizes virtualization-based security for isolating the secrets to allow only the privileged system software to access them.
Option C is correct. Exploit Protection allows the users to block particular applications from creating the child processes.
Option D is incorrect. It is designed for protecting PCs against malware and other untrusted software. It is not the right solution to make the apps not capable of creating the child processes.
Reference:
To know more about Exploit protection, please visit the below-given link: https://docs.microsoft.com/en-us/microsoft-365/security/defender-endpoint/enable-exploit-protection
Domain: Secure Windows Server On-premises and Hybrid Infrastructures
Question 2 : Would you recommend someone to deploy a Windows Defender Application Control policy with Enforcement Enabled and then later deploy a policy with Audit-Only to the same device?
A. Yes
B. No
Correct Answer: B
Explanation:
Windows Defender Application Control is built for protecting PCs against malware and other untrusted software. It is recommended not to deploy a policy with Enforcement Enabled, and then later deploy a policy with Audit-Only to the same device. This type of configuration may result in untrusted software being allowed to run.
Reference:
To know more about Windows Defender Application Control, please visit the below-given link: https://docs.microsoft.com/en-us/mem/configmgr/protect/deploy-use/use-device-guard-with-configuration-manager
Domain: Secure Windows Server On-premises and Hybrid Infrastructures
Question 3 : In which of the following attacks, automated tools are used by the hackers to enter lists of credentials against many different company login portals?
A. Brute force attack
B. Dictionary attack
C. Password spraying attack
D. Credential stuffing attack
E. Spidering
Correct Answer: D
Explanation:
Credential stuffing attack is one of the techniques used by hackers where the hackers utilize automated tools to enter lists of credentials against many different company login portals.
Option A is incorrect. In this type of attack, the hackers try many different potential password combinations until they hit upon the right one.
Option B is incorrect. A dictionary attack is a specific type of brute force attack that includes trying words found in the dictionary as possible passwords.
Option C is incorrect. In this type of attack, a hacker enters a known username or other account identifier and tries several common passwords to know if they work.
Option D is correct. In this type of attack, automated tools are used by the hackers to enter lists of credentials against many different company login portals.
Option E is incorrect. In Spidering, the Malicious users gather as much information as possible about a hacking target and then try the various password combinations formed using that data.
References:
To know more about how to set and manage Active Directory Password Policy, please visit the below-given links: https://docs.microsoft.com/en-us/previous-versions/windows/it-pro/windows-server-2012-r2-and-2012/hh994572(v=ws.11), https://blog.netwrix.com/2021/07/14/active-directory-password-policy/
Domain: Secure Windows Server On-premises and Hybrid Infrastructures
Question 4 : Application, network, and NAT are three different types of rule collections supported by the Azure Firewall. Out of these, which rule type defines the protocol, destination port, source IP address and destination IP address.
A. Application Rules
B. Network Rules
C. NAT Rules
D. None of these
Correct Answer: B
Explanation:
Network rules contain source addresses, protocols, destination ports, and destination addresses as a means to control the flow of network traffic.
Option A is incorrect. Application rules configure FQDNs that can be accessed from a subnet.
Option B is correct. Network Rules define the protocol, destination port, source IP address and destination IP address.
Option C is incorrect. NAT rules are used to configure DNAT (Destination Network Address Translation) rules to allow incoming Internet connections.
Option D is incorrect. Network rules defines the protocol, destination port, source IP address and destination IP address.
Reference:
To know more about Azure Firewall, please visit the below-given link: https://docs.microsoft.com/en-us/azure/firewall/tutorial-firewall-deploy-portal
Domain: Secure Windows Server On-premises and Hybrid Infrastructures
Question 5 : When Azure Disk Encryption is enabled on a Linux VM, which of the following technologies is used by Azure Disk encryption to encrypt the file system volumes residing on VM disks?
A. BitLocker Drive Encryption
B. DM-Crypt
C. Key Vault
D. None of these
Correct Answer: B
Explanation:
Azure Disk Encryption helps in protecting and safeguarding your data to accomplish your organizational security and compliance needs. It utilizes DM-Crypt feature of Linux to offer volume encryption to the operating system and Azure VM data disks and is connected to Azure Key Vault for controlling and managing the encryption secrets and keys of disks easy.
Option A is incorrect. BitLocker Drive Encryption is used by Azure Disk Encryption for Windows.
Option B is correct. For Linux VMs, Azure Disk Encryption uses DM-Crypt.
Option C is incorrect. Key Vault is integrated with Azure Disk Encryption to manage the disk-encryption keys and secrets.
Option D is incorrect. Azure Disk Encryption uses the DM-Crypt feature of Linux to offer volume encryption for the OS and Azure VM data disks.
Reference:
To know more about Azure Disk Encryption for Linux VMs, please visit the below-given link: https://docs.microsoft.com/en-us/azure/virtual-machines/linux/disk-encryption-overview
Domain: Implement and Manage Windows Server High Availability
Question 6 : The quorum configuration in a failover cluster determines the number of failures that the cluster can sustain. Which of the following cmdlet is used to configure the quorum options for a failover cluster?
A. Set-ClusterQuorum
B. Set-ClusterFaultDomain
C. Set-QuorumForFailoverCluster
D. Set-ADClusterQuorum
Correct Answer: A
Explanation:
The Set-ClusterQuorum command configures quorum options for a failover cluster. This quorum configuration determines the number of failures that can be sustained by the cluster. In case of an additional failure, the cluster must stop running. The possible failures are failures of nodes or, in some conditions, of a disk witness (which consists of a copy of the cluster configuration) or even a file share witness.
Option A is correct. Set-ClusterQuorum is the right cmdlet used to configure the quorum options for a failover cluster.
Option B is incorrect. Set-ClusterFaultDomain cmdlet is used to update an existing cluster fault domain.
Option C is incorrect. Set-QuorumForFailoverCluster is not the right cmdlet.
Option D is incorrect. Set-ADClusterQuorum isn’t the right cmdlet.
Reference:
To know more about Set-ClusterQuorum command, please visit the below-given link: https://docs.microsoft.com/en-us/powershell/module/failoverclusters/set-clusterquorum
Domain: Implement and Manage Windows Server High Availability
Question 7 : Which of the following tasks do you need to perform as an administrator to use CAU (Cluster-Aware Updating) in remote-updating mode?
A. Install a clustered role
B. Install the Failover Clustering Tools on a remote computer
C. Pause cluster nodes
D. Configure Quorum
Correct Answer: B
Explanation:
To use CAU in remote-updating mode, you need to install the Failover Clustering Tools on a remote computer with direct connectivity to the cluster nodes.
Option A is incorrect. A clustered role is needed while using self-updating mode.
Option B is correct. To use CAU in remote-updating mode, you need to install the Failover Clustering Tools on a remote computer with direct connectivity to the cluster nodes.
Option C is incorrect. You don’t need to pause cluster nodes to use CAU.
Option D is incorrect. Configuring quorum is not the right task.
Reference:
To know more about Cluster-Aware Updating, please visit the below-given link: https://docs.microsoft.com/en-us/windows-server/failover-clustering/cluster-aware-updating
Domain: Implement and Manage Windows Server High Availability
Question 8 : You are having a failover cluster known as Cluster2 with the following configuration:
Number of Nodes: 8
Quorum: Dynamic quorum
Witness: File share, Dynamic witness
How many nodes can fail simultaneously (at maximum) while maintaining quorum?
A. 1
B. 2
C. 3
D. 4
E. 5
Correct Answer: D
Explanation:
The most important thing to note is that the question is asking about the number of nodes failing simultaneously not one after the other.
With 8 nodes and 1 witness, there are a total of 9 votes. For maintaining the quorum, it requires 5 votes to be available (5 votes is the majority of 9). It indicates that a minimum of 4 nodes plus the witness are required to remain online for the cluster to remain functional. So, the maximum number of nodes that can fail simultaneously is 4.
Option A is incorrect. 1 is not the right answer.
Option B is incorrect. The question asks about the maximum simultaneous failure that is 4.
Option C is incorrect. 3 is not the right answer.
Option D is correct. The question asks about the maximum simultaneous failure which is 4.
Option E is incorrect. The maximum number of nodes that can fail simultaneously is 4.
Reference:
To know more about cluster and pool quorum, please visit the below-given link: https://docs.microsoft.com/en-us/windows-server/storage/storage-spaces/understand-quorum
Domain: Implement and Manage Windows Server High Availability
Question 9 : To use CAU (Cluster-Aware Updating), you need to install the Failover Clustering feature in Windows Server and create a failover cluster. Which of the following tools can you use to install the Failover Clustering feature?
A. Add Roles and Features Wizard in Server Manager
B. Install-Windows Feature Windows PowerShell cmdlet
C. DISM (Deployment Image Servicing and Management) command-line tool
D. All the above
Correct Answer: D
Explanation:
To use Cluster-Aware Updating, install the Failover Clustering feature in Windows Server and create a failover cluster. Components supporting CAU functionality are installed automatically on each cluster node.
The following tools can be used to install the Failover Clustering feature:
- Add Roles and Features Wizard in Server Manager
- Install-WindowsFeature Windows PowerShell cmdlet
- DISM command-line tool
Option A is incorrect. All of the given tools can be used to install failover clustering features.
Option B is incorrect. You can use any of the given tools to install the failover clustering feature.
Option C is incorrect. DISM is not the only mandatory tool to be used.
Option D is correct. All of the given tools can be used to install failover clustering features.
Reference:
To know more about Cluster-Aware Updating, please visit the below-given link: https://docs.microsoft.com/en-us/windows-server/failover-clustering/cluster-aware-updating
Domain: Implement and Manage Windows Server High Availability
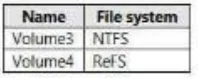
Question 10 : You are having a Storage Spaces Direct configuration that has persistent memory and consists of the data volumes as demonstrated in the below table.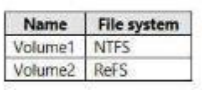
A. Both Volume 1 and 3
B. Both Volume 2 and 4 only
C. Either Volume 1 or Volume 3
D. Either volume 2 or volume 4
Correct Answer: C
Explanation:
Direct access can be used only on a single volume and that volume must be NTFS. Here, in the given scenario, volume 1 and volume 3 are NTFS and DAX can be configured on any one of them. If you decide to go with volume 1 there would be a need to reformat the volume.
Option A is incorrect. Direct access can be used only on a single volume, not both Volume 1 and Volume 3.
Option B is incorrect. To use DAX, the volume must be NTFS. DAX can’t be applied to ReFS.
Option C is correct. You can use DAX on any one volume out of volume 1 and volume 3.
Option D is incorrect. DAX can’t be applied on a ReFS volume.
Reference:
To know more about Direct Access, please visit the below-given link: https://docs.microsoft.com/en-us/windows-server/storage/storage-spaces/persistent-memory-direct-access
Domain: Implement Disaster Recovery
Question 11 : From the below-given list, choose the type of computers on which you can’t install Azure Backup Server. (Select all that are applicable)
A. A computer that runs as a domain controller
B. A computer that has an Application Server role installed on it
C. A computer that runs Exchange Server on it
D. A computer that is a node of a cluster
E. All of these
Correct Answer: E
Explanation:
Azure Backup Server has been designed to run on a single-purpose, dedicated server. Azure Backup Server can’t be installed on:
Option A is incorrect. Azure Backup Server can’t be installed on all of the given computer types.
Option B is incorrect. It’s true that you can’t install Azure Backup Server on a computer having an Application server role installed on it but all other options are also correct.
Option C is incorrect. Azure Backup Server can’t be installed on any of the given computer types.
Option D is incorrect. You can’t install Azure Backup Server not only on the computer that is a node of a cluster, but also all of the given computer types.
Option E is correct. Azure Backup Server can’t be installed on all of the given computer types.
Reference:
To know more about installing and upgrading Azure Backup Server, please visit the below-given link: https://docs.microsoft.com/en-us/azure/backup/backup-azure-microsoft-azure-backup
Domain: Implement Disaster Recovery
Question 12 : There are 3 Azure virtual machines (VMs) named VM1, VM2, and VM3 which host a multi tier app. You plan the implementation of Azure Site Recovery. You are required to make sure that all virtual machines fail over as a group. Which of the following would you configure?
A. Availability Zone
B. Availability set
C. A recovery plan
D. None of these
Correct Answer: C
Explanation:
Recovery plans can be used and configured for customizing and sequencing the failover and recovery of multi-tier apps running on several VMs. Machines are grouped together in a recovery plan, and scripts and manual actions can be optionally added. You can integrate recovery plans with Azure automation runbooks.
Option A is incorrect. Azure availability zones are physically separate locations within every Azure region that are tolerant to local failures. These are not configured for the given purpose.
Option B is incorrect. You don’t need to configure the availability set for the given purpose.
Option C is correct. Recovery plans can be used and configured for customizing and sequencing the failover and recovery of multi-tier apps running on several VMs.
Option D is incorrect. You need to configure a recovery plan to make sure that all virtual machines failover as a group.
Reference:
To know more about Azure Site Recovery, please visit the below-given link: https://docs.microsoft.com/en-us/azure/site-recovery/site-recovery-overview
Domain: Implement Disaster Recovery
Question 13 : There are 2 servers known as Server1 and Server2 both running Windows Server. Both of the servers have installed Hyper-V server role. Server1 hosts 3 VMS named VM1, VM2, and VM3. The VMs replicate to Server2 and Server1 faces a hardware failure. Now, You need to bring all 3 VMs – VM1, VM2, and VM3 back online at the earliest possible. From the Hyper-V Manager console on Server2, which of the following would you run for each VM?
A. Start
B. Planned failover
C. Unplanned failover
D. Multifeed failover
Correct Answer: C
Explanation:
With unplanned failover, you can recover from the latest recovery point or from previous recovery points. It can be run by right-clicking on the replica virtual machine and selecting Replication > Unplanned Failover from Hyper-V Manager or Failover Clustering Manager.
Option A is incorrect. Running starts won’t help in meeting the goal.
Option B is incorrect. Planned failover makes prerequisite checks to make sure that there is no data loss. It checks that the primary VM is shut down before initiating the failover.
Option C is correct. In the given scenario, you need to run an unplanned failover to bring all 3 VMs back online at the earliest possible.
Option D is incorrect. There is nothing like a multifeed failover.
Reference:
To know more about Hyper-V Replica, please visit the below-given link: https://docs.microsoft.com/en-us/windows-server/virtualization/hyper-v/manage/set-up-hyper-v-replica
Domain: Migrate Servers and Workloads
Question 14 : There are two file servers known as Server1 and Server2 and both run Windows Server. There is a shared folder named Data in Server1. Data has 10 TB of data. You are looking towards decommissioning Server1. Therefore, you want to migrate the files from the shared folder Data on Server1 to a new shared folder on Server2.
The solution is required to meet the below-given requirements:
- You need to ensure that file, share, and folder permissions are copied.
- After the initial copy happens, ensure that modifications in \\Server1\Data can be synced to the destination without initiating a full copy.
- Administrative effort should be minimized.
What would you use to achieve the given requirement?
A. Azcopy
B. Storage Migration service
C. Storage Replica
D. Xcopy
Correct Answer: B
Explanation:
With Storage Migration Service, it becomes easy to migrate the storage to Azure or Windows Server. It offers a graphical tool that stores data on Linux, Windows, and NetApp CIFS servers. After that it moves data to Azure VMs and other new servers. It also gives the option to pass on the server identity to the destination server to allow users and apps access their data without modifying paths or links.
Option A is incorrect. AzCopy is a command-line utility that is used to copy files or blobs to or from a storage account.
Option B is correct. Using Storage Migration Service will ensure that all the given requirements are met.
Option C is incorrect. Storage Replica is not the best solution to meet the given requirements.
Option D is incorrect. In the given scenario, Xcopy doesn’t suit best.
Reference:
To know more about Storage Migration Service, please visit the below-given link: https://docs.microsoft.com/en-us/windows-server/storage/storage-migration-service/overview
Domain: Migrate Servers and Workloads
Question 15 : Complete the statement below:
You have been asked to assign the Virtual Machine Contributor role to an Azure account. Assigning the VM contributor role to an Azure account will provide the permission to …………..
A. Create a VM in the selected resource group
B. Create a VM in the selected virtual network.
C. Write to an Azure managed disk
D. All of the above
Correct Answer: D
Explanation:
Assigning the VM Contributor role to the Azure account will provide the permission of:
- creating a VM in the selected resource group
- creating a VM in the selected virtual network.
- Writing to an Azure managed disk.
Option A is incorrect. Assigning the VM Contributor role to the Azure account will provide all the given permissions, not just one.
Option B is incorrect. Assigning the VM Contributor role to the Azure account will provide all the given permissions.
Option C is incorrect. Assigning the VM Contributor role to the Azure account will provide all the given permissions.
Option D is correct. All the given permissions will be provided.
Reference:
To know more about migrating machines as physical servers to Azure, please visit the below-given link: https://docs.microsoft.com/en-us/azure/migrate/tutorial-migrate-physical-virtual-machines
Domain: Migrate Servers and Workloads
Question 16 : There are 2 servers having the Web Server (IIS) server role installed. The configuration for the servers is as in the below table: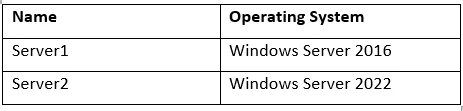
Complete the following command.
msdeploy -verb:sync -source: …………………………….. – dest: …………………………….
A. apphostconfig=”Site1″,computername=Server2 and apphostconfig=”Site1”
B. apphostconfig=”Site1″ and apphostconfig=”Site1”,computername=Server2
C. apphostconfig=”Site1″ and apphostconfig=”Site1”,computername=Server1
D. apphostconfig=”Site1″,computername=Server1 and apphostconfig=”Site1”
Correct Answer: D
Explanation:
The command to be used to pull synchronization of Site 1 in the given scenario is:
msdeploy -verb:sync -source: apphostconfig=”Site1″,computername=Server1 – dest: apphostconfig=”Site1”
Option A is incorrect. In the command, the computername would be Server1, not Server2.
Option B is incorrect. The given command is not correct.
Option C is incorrect. Using the given option won’t result in the right command.
Option D is correct. The right command is msdeploy -verb:sync -source: apphostconfig=”Site1″,computername=Server1 – dest: apphostconfig=”Site1”.
Reference:
To know more about synchronizing IIS, please visit the below given link: https://docs.microsoft.com/en-us/iis/publish/using-web-deploy/synchronize-iis
Domain: Migrate Servers and Workloads
Question 17 : After you raise the domain functional level to a higher level, you realize that there is a domain controller of an earlier version and therefore the domain functional level should be changed back to an older level.
Is it possible to change back the domain functional level to an older level?
A. Yes
B. No
Correct Answer: A
Explanation:
After the domain functional level is increased to a higher level, it is possible to change it back to an older level with the help of forest recovery. This restriction occurs because the features often modify the communication among the domain controllers, or the features modify the storage of the Active Directory (AD) data in the database.
Reference:
To know more about raising AD domain and forest functional levels, please visit the below-given link: https://docs.microsoft.com/en-us/windows-server/identity/ad-ds/active-directory-functional-levels
Domain: Monitor and Troubleshoot Windows Server Environments
Question 18 : There are 4 Azure VMs. You need to gather the performance data and Windows Event logs from these VMs and send the collected data to an Azure Storage account. Which of the following would you install on VMs?
A. Azure Monitor agent
B. Azure Diagnostics extension
C. Dependency agent
D. Telegraf agent
Correct Answer: B
Explanation:
Azure Diagnostics extension is one of the agents in Azure Monitor that collects the performance and monitoring data from the guest OS of Azure compute resources including VMs.
The main scenarios that diagnostics extension addresses are:
- Collecting guest metrics into AZ Monitor Metrics.
- Sending guest metrics and logs to AZ storage for archiving.
- Sending guest metrics and logs to Azure event hubs to deliver outside of Azure.
Option A is incorrect. Azure Monitor agent is not the right agent to install.
Option B is correct. The azure diagnostic extension should be installed on VMs to gather the performance data and Windows Event logs from these VMs and send the collected data to an Azure Storage account.
Option C is incorrect. The Dependency agent collects exposed data about processes that run on the machine and external process dependencies.
Option D is incorrect. Telegraf agent is a Linux agent.
Reference:
To know more about Azure Monitor agents, please visit the below-given link: https://docs.microsoft.com/en-us/azure/azure-monitor/agents/agents-overview
Domain: Monitor and Troubleshoot Windows Server Environments
Question 19 : There is an Azure VM named VM2 running Windows Server. VM2 has boot diagnostics configured to utilize a managed storage account. You have been asked to troubleshoot the connectivity issue on VM2. You are required to run a PowerShell command on VM2 with the use of the Azure Serial Console.
From the below-given list of actions, choose the action that is not required for the given purpose.
A. From the Azure portal, open the Run command blade
B. From the Azure portal, configure the Boot diagnostics settings for VM2 to use a custom storage account
C. From the serial console, run cmd
D. From the serial console, run ch-si 1and sign in by using a local account
E. From the Azure portal, open the serial console blade of VM2
Correct Answer: A
Explanation:
To achieve the given task, you need to follow the following 4 tasks in the below sequence:
- From the Azure portal, configure the Boot diagnostics settings for VM2 to use a custom storage account
- From the Azure portal, open the serial console blade of VM2.
- From the serial console, run cmd.
- From the serial console, run ch-si 1and sign in by using a local account
Option A is correct. You don’t need to open the Run command blade from the Azure portal.
Option B is incorrect. The given one is the required task to perform.
Option C is incorrect. You need to perform this action.
Option D is incorrect. This is a required action.
Option E is incorrect. The given task is required.
Reference:
To know more about Azure serial console for Windows, please visit the below-given link: https://docs.microsoft.com/en-us/troubleshoot/azure/virtual-machines/serial-console-windows
Domain: Monitor and Troubleshoot Windows Server Environments
Question 20 : repadmin /showrepl is the command that is run to identify Active Directory replication problems. When you run this command, you receive the “LDAP Error 49” as output.
What might be the possible root cause of this error?
A. The administration tool couldn’t contact AD DS
B. The domain controller (DC) computer account may not be synchronized with the KDC (Key Distribution Center)
C. A replication link occurs between two domain controllers, but replication can’t be performed appropriately due to an authentication failure
D. None if these
Correct Answer: B
Explanation:
Replication issues are reported in event messages and in several error messages that happen when a service or application tries an operation. Most replication issues are recognized in the event messages which are logged in the Directory Service event log. Replication issues might also be recognized in terms of error messages as the output of the repadmin /showrepl command.
Option A is incorrect. The given one is the root cause of the Repadmin error “Cannot open LDAP connection to localhost”.
Option B is correct. The given one is the possible root cause of the LDAP Error 49.
Option C is incorrect. It would have resulted in the error “Access is denied”.
Option D is incorrect. The possible root cause is “The DC computer account may not be synchronized with the KDC.
Reference:
To know more about troubleshooting Active Directory Replication Problems, please visit the below-given link: https://docs.microsoft.com/en-us/windows-server/identity/ad-ds/manage/troubleshoot/troubleshooting-active-directory-replication-problems
Domain: Implement Disaster Recovery
Question 21 : You have just deleted some backup data from Azure Backup. Now, one of the administrative staff informs you that the deleted data was required to restore some damaged files. What are the possible options available to you?
A. Once the backup data is deleted, it is unrecoverable. You can do nothing
B. You can recover the deleted backup data with no loss for up to 7 days after deletion
C. You can recover the deleted backup data with no loss for up to 14 days after deletion
D. You can recover the deleted backup data, whenever required
Correct Answer: C
Explanation:
Some security features are provided by Azure backup intended towards protecting the backup data even after deletion. With soft delete, if you delete the backup of a virtual machine, the backup data is retained for an additional 14 days, making it possible to recover that backup item with no data loss.
Option A is incorrect. The backup data can be recovered up to 14 days after deletion.
Option B is incorrect. You can recover the deleted backup data with no loss for up to 14 days, not only 7 days after deletion.
Option C is correct. With soft delete, if you delete the backup of a virtual machine, the backup data is retained for an additional 14 days, making it possible to recover that backup item with no data loss.
Option D is incorrect. The deleted backup data can be recovered only for up to 14 days. After that, it can’t be recovered.
Reference:
To know more about various security features available in Azure Backup, please visit the below-given link: https://docs.microsoft.com/en-us/azure/backup/security-overview
Domain: Implement Disaster Recovery
Question 22 : One of your friends needs an Azure subscription containing an Azure Recovery Services vault. He has an on-premises physical server running Windows Server. He needs to back up the server daily to Azure.
He is confused about the procedure he should follow and therefore he consults you. You need to suggest to him the steps that he should follow to meet the goal. From the below-given list of steps, choose the steps that would be part of the procedure. [ Choose all that are applicable]
A. On Server, install and register the Azure connected Machine Agent
B. Download the vault credentials file
C. Install and register the Microsoft Azure Recovery Services (MARS) agent
D. Create a recovery plan
E. On Server, install and register the Azure Site Recovery Mobility Service Agent
F. Schedule a backup
Correct Answers: B, C and F
Explanation:
The three steps that are needed to be followed in the right sequence are:
- Download the vault credentials file
- Install and register the Microsoft Azure Recovery Services (MARS) agent
- Schedule a backup
Option A is incorrect. There is no need to install and register the Azure-connected Machine Agent.
Option B is correct. Downloading the vault credentials file is the foremost step in the process.
Option C is correct. After downloading the vault credentials file, there is a need to install and register a MARS agent.
Option D is incorrect. There is no need to create a recovery plan.
Option E is incorrect. There is no need to install and register the Azure Site Recovery Mobility Service Agent.
Option F is correct. Scheduling the backup is the necessary step in the procedure.
Reference:
To know more about how to back up Windows Server to Azure, please visit the below-given link: https://docs.microsoft.com/en-us/azure/backup/tutorial-backup-windows-server-to-azure
Domain: Implement Disaster Recovery
Question 23 : You are the network administrator. You need to create a recovery plan in Azure Site Recovery to fail over all the virtual machines (around 250) to an Azure region.
The plan has four manual actions. You want to replace one of these four manual actions with an automated process. Which of the following would you use?
A. An Azure PowerShell function
B. An Azure Desired State Configuration (DSC) virtual machine extension
C. An Azure Automation Runbook
D. Custom Script Extension on VMs
Correct Answer: C
Explanation:
It might be a complex task to recover large applications. The processes with manual steps are prone to error. A recovery plan can be used to impose order, and automate the steps or actions required at each step, utilizing Azure Automation runbooks for failover to Azure or scripts.
Option A is incorrect. You need to use an Azure Automation Runbook to replace the manual action with an automated process.
Option B is incorrect. Azure Desired State Configuration (DSC) extension is primarily used to bootstrap a VM to the Azure Automation State Configuration (DSC) service.
Option C is correct. Azure Automation Runbook is used to replace the manual action with an automated process.
Option D is incorrect. Custom Script Extension won’t work in the given scenario.
Reference:
To know more about the recovery plan, please visit the below-given link: https://docs.microsoft.com/en-us/azure/site-recovery/recovery-plan-overview
Domain: Implement Disaster Recovery
Question 24 : Complete the statement below:
In the Live migration, when a VM failover is started by an administrator, the source Hyper-V server creates a ……………….. connection to the target Hyper-V server.
A. SMTP
B. HTTP
C. P2P
D. TCP
Correct Answer: D
Explanation:
When an administrator begins a VM failover, the source Hyper-V server makes a TCP connection with the target Hyper-V server. This TCP connection is used for transferring the VM configuration data between the two hosts.
Option A is incorrect. Rather than SMTP, a TCP connection is created.
Option B is incorrect. The connection type is TCP, not HTTP.
Option C is incorrect. P2P is not the right option.
Option D is correct. When an administrator begins a VM failover, the source Hyper-V server makes a TCP connection with the target Hyper-V server
Reference:
To know more about Hyper-V VM live migration, please visit the below-given link: https://docs.microsoft.com/en-us/learn/modules/implement-high-availability-of-windows-server-vms/4-implement-hyper-v-vm-live-migration
Domain: Migrate Servers and Workloads
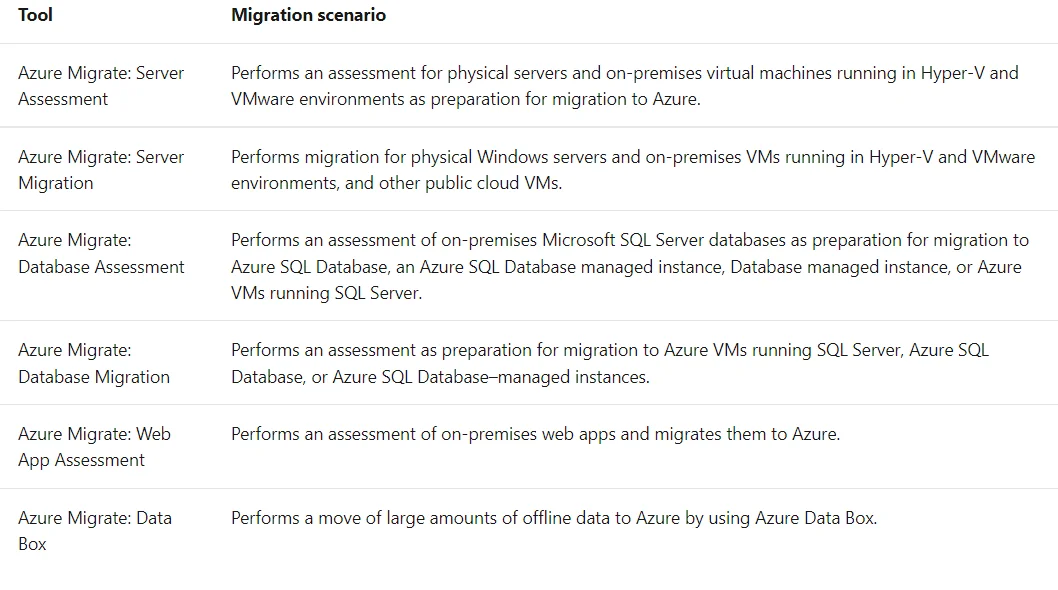
Question 25 : After a long discussion, your Whizlabs team decides to use Azure Migrate: Server Migration tool. From the below-given list, choose the source server configurations that are supported by Azure Migrate: Server Migration.
A. Azure VMs
B. VMware VMs
C. Physical Unix Server
D. Physical Windows Server.
E. Physical Sun Solaris
Correct Answers: A, B and D
Explanation:
The following table lists some of the different migration tools that can be used depending upon the migration scenario:
Option A is correct. Azure Migrate: Server Migration supports Azure VMs.
Option B is correct. Azure Migrate: Server Migration supports VMware VMs.
Option C is incorrect. Azure Migrate: Server Migration doesn’t support the migration of physical Unix hosts or Sun Solaris hosts.
Option D is correct. Azure Migrate: Server Migration supports Physical Windows Server.
Option E is incorrect. Azure Migrate: Server Migration doesn’t support the migration of physical Unix hosts or Sun Solaris hosts.
Reference:
To know more about migration tools and strategy, please visit the below-given link: https://docs.microsoft.com/en-us/azure/migrate/migrate-services-overview
Summary
I hope the above free questions cover all the domains of the AZ-801 exam. By using AZ-801 practice questions, you can test your knowledge and identify areas that require more attention. These questions remain a valuable resource for anyone seeking to achieve the Microsoft Azure AZ-801 certification and advance their career in cloud computing and digital transformation.
To enhance your practical skills further, you can take up hands-on labs and Azure sandboxes and gain confidence in clearing the exam.
If you have any doubts about this blog, please feel free to comment us!
- A Tour of Google Cloud Hands-on Labs - December 12, 2023
- Mastering Azure Basics: A Deep Dive into AZ-900 Exam Domains - December 4, 2023
- Exploring the Benefits of Validation Feature in Hands-on Labs - October 10, 2023
- 20+ Free MD-102 Exam Questions on Microsoft Endpoint Administrator - September 27, 2023
- 20+ Free MS-102 Exam Questions on Microsoft 365 Administrator Certification - September 25, 2023
- AWS Certified Developer Salary in 2024 - September 19, 2023
- Guide to SharePoint, OneDrive, and Teams External Sharing in Teams - September 10, 2023
- What is Cross-Tenant Synchronization | MS-700 Certification - August 31, 2023