Microsoft Endpoint Administrator (MD-102) certification is designed mainly for IT professionals who are responsible for managing and deploying Windows 10 and other Microsoft 365 technologies within an organization.
Microsoft MD-102 Exam assesses your expertise in deploying, configuring, protecting, managing, and monitoring devices and applications of the client in a Microsoft 365 environment.
In this blog, we’ll provide you with valuable resources such as free MD-102 practice exam questions, allowing you to sharpen your skills and boost your confidence. Moreover, you can take advantage of our online Microsoft MD-102 practice test to assess your readiness before undertaking the actual MD-102 exam questions.
Top MD-102 Practice Test Exam Questions & Answers
Passing the MD-102 Certification exam can help you attain the Microsoft 365 Certified: Endpoint Administrator Associate distinction.
You can prepare for the Endpoint Administrator (beta) certification with MD-102 exam questions and answers crafted by our experts. Relying on the Microsoft MD-102 exam practice test online before appearing for the actual MD-102 exam can help to determine your preparation level.
Here, we have compiled the top 25 Microsoft’s MD-102 actual exam questions for you:
Domain: Manage identity and compliance
Question 1: Which of the following commands can be used for restricting to a specific resource group on a specific subscription?
A. “/subscriptions/{sub-id}/resourceGroups/{rg-name}”
B. “/subscriptions/{sub-id}”
C. “/subscriptions/{sub-id}/resourceGroups/{rg-name}/{resource-name}”
D. “/subscriptions/{sub-id}”, “/subscriptions/{sub-id}”
Correct Answer: A
Explanation
Option A is correct – Restrict to a specific resource group on a specific subscription.
Option B is incorrect – Command for Restrict to a subscription.
Option C is incorrect – Command for Restrict to a specific resource.
Option D is incorrect – Command for Make a role available for assignment in two subscriptions.
Reference: https://docs.microsoft.com/en-us/learn/modules/manage-users-and-groups-in-aad/5-manage-aad-roles
Domain: Manage identity and compliance
Question 2: The forest root domain contains objects that don’t exist in other domains in the forest.
A. True
B. False
Correct Answer: A
Explanation
Option A is correct because you always create these objects on the first domain controller, a forest can consist of as few as one domain with a single domain controller, or it can consist of several domains across multiple domain trees.
Reference: https://docs.microsoft.com/en-us/learn/modules/introduction-to-ad-ds/4-define-forests-domains
Domain: Manage identity and compliance
Question 3: Global Infotech has appointed you as a Desktop Administrator who needs your help on setting up conditional access policies to provide granular access for accessing company data irrespective of the device and location due to work from home policy. Please select the most secure way of accessing the data from the following.
A. Activate MFA for the employees to use the corporate application on their personal devices
B. Automatically update the device to the latest version for accessing the company’s data
C. Ask the employees to visit any nearby office with a secured network
D. User Exchange ActiveSync to enable access for the employees using their home network
Correct Answer: A
Explanation
Option A is correct – We should need better protection and Conditional access allows you to add a layer of protection for them by requiring MFA when users access them.
Option B is incorrect – Conditional access will not have any functions on initiating any steps instead, it will set criteria for access.
Option C is incorrect – Employees will not prefer going to the office due to work from home setup.
Option D is incorrect – Exchange ActiveSync (EAS) is an Exchange synchronization protocol that’s optimized to work together with high-latency and low-bandwidth networks which can’t be used to create policies.
Domain: Manage identity and compliance
Question 4: What are some of the more commonly used device compliance settings? Choose 2 Options
A. Restrict internet service providers
B. Perform factory reset including deleting personal data
C. Maximum OS version allowed
D. Record the private conversation on any 3rd party messenger
E. Whether the device is jail-broken or rooted
Correct Answers: C and E
Explanation
Options C and E are correct – Maximum OS version allowed, Whether the device is jail-broken or rooted, Local data encryption, and requires the device to be at, or under the Mobile Threat Defense level are some of the more commonly used device compliance settings. Some of the more commonly used device compliance settings include, require a password to access devices, local data encryption, whether the device is jail-broken or rooted, minimum OS version required, maximum OS version allowed, require the device to be at, or under the Mobile Threat Defense level.
Option A is incorrect – Internet Service Provider (ISP) can’t be restricted using compliance policies.
Option B is incorrect – Deleting personal data will be against the data protection policy but we can encrypt data.
Option D is incorrect – We can restrict the usage of applications that can be installed on a device but we don’t have access to record conversations on 3rd party messenger applications.
Reference: https://docs.microsoft.com/en-us/learn/modules/manage-device-compliance/2-plan-for
Domain: Manage identity and compliance
Question 5: You are assigned a task to restrict access for Android Smartphones from accessing Organizational data. You should find and restrict the access for smartphones that don’t have the latest version of the security patch and can give a maximum 90 days of grace period for the users to update their smartphones. Which of the following can be used to achieve this task?
A. Notify end users through email
B. Google Play Protect
C. Encryption of data
D. Mark device non-compliant
Correct Answer: D
Explanation
Option D is correct – Organizations can grant a grace period for users to update the device to make it compliant. Devices that aren’t updated in that grace period are marked as noncompliant.
Option A is incorrect – Notifying end-users via email can just alert them with a customized email notification before sending it to the end-user.
Option B is incorrect – Google Play Protect is an android specific app that checks your apps and devices for harmful behavior.
Option C is incorrect – Only encryption of data will not restrict the user access using device compliance.
Reference: https://docs.microsoft.com/en-us/learn/modules/manage-device-compliance/2-plan-for
Domain: Manage, maintain, and protect devices
Question 6: A restaurant named Pizzamania wants to digitize their orders so they decide to give new iPhones to their waiters. Which Apple option can deploy an enrollment profile “over the air” to bring devices into management?
A. Company Portal
B. Device Enrollment Program (DEP)
C. Enterprise work profile
D. Configurator for iPhone
Correct Answer: B
Explanation
Option B is correct – Organizations can purchase iOS devices through Apple’s Device Enrollment Program (DEP). DEP lets you deploy an enrollment profile “over the air” to bring devices into management.
Option A is incorrect – Company Portal is the app that lets you, as an employee of your company, securely access those resources.
Option C is incorrect – Enterprise work profile devices to ensure work and personal information are separate.
Option D is incorrect – Configurator for iPhone enables you to add any Mac that has the T2 Security Chip or Apple silicon to your organization in Apple Business Manager or Apple School Manager so that you can use Automated Device Enrollment.
Domain: Manage, maintain, and protect devices
Question 7: In Azure AD, If you’re in a federated domain, you’re redirected to your on-premises Secure Token Service (STS) server.
A. True
B. False
Correct Answer: A
Explanation
Option A is correct – Federated domain in Azure AD will redirect to the on-premises STS server by locating a matching tenant.
For example, Active Directory Federation Services (AD FS), authenticates users with their usernames and password. Users can access certain applications without being prompted to provide login credentials repeatedly.
Domain: Manage, maintain, and protect devices
Question 8: Which of the following statements NOT true about policy sets?
A. Used for group objects that need to be assigned together
B. It can be assigned as cross-platform
C. The default restrictions and ESP cannot be added to a policy set
D. Policy sets will replace existing concepts or objects
Correct Answer: D
Explanation
Option D is correct – Policy sets do not replace existing concepts or objects. You can continue to assign individual objects and you can also reference individual objects as part of a policy set. Therefore, any changes to those individual objects will be reflected in the policy set.
Option A is incorrect – One of the usages of policy sets is to Group objects that need to be assigned together.
Option B is incorrect – Policy sets support Windows, Android, macOS, and iOS/iPadOS settings, and can be assigned cross-platform.
Option C is incorrect – In Policy sets, the default restrictions and ESP cannot be added to a policy set and which is one of the enrollment restrictions and Enrollment Status Page (ESP) issues.
Reference: https://docs.microsoft.com/en-us/mem/intune/fundamentals/policy-sets
Domain: Manage applications
Question 9: You are required to deploy a Win32 application using Microsoft Endpoint Manager (MEM). While deploying, your employer asks you to add the name of the person who will be the point of contact for this app. Which of the following will be the most suitable field to add this information?
A. Publisher
B. Developer
C. Name
D. Owner
Correct Answer: D
Explanation
Option D is correct – Under the App information page, the Owner field is used to indicate the name of the person in your organization who manages to license or the point of contact for this app.
Option A is incorrect – The name of the developer or company that distributes the app.
Option B is incorrect – The name of the developer or company that distributes the app.
Option C is incorrect – This name will be visible in the Intune apps list and to users in the Company Portal.
Domain: Manage applications
Question 10: Which of the following values used to define the location of the Office installation files in the Office Deployment Tool?
A. UpdatePath=”\\Server\Share”
B. OfficeClientEdition=”32″
C. SourcePath=”\\server\share”
D. DownloadPath=”\\server\share”
Correct Answer: C
Explanation
Option C is correct – SourcePath=”\\server\share” – The SourcePath value should not include the /Office part or the name of the folder on which Office Data has been downloaded.
Option A is incorrect – Office checks for updates at “\server\share” on your network.
Option B is incorrect – Downloads and installs the 32-bit edition of Office.
Option D is incorrect – Office downloads the package at “\server\share” on your network.
Reference: https://docs.microsoft.com/en-us/deployoffice/office-deployment-tool-configuration-options
Domain: Manage applications
Question 11: __________ monitors reliability and performance metrics and provides custom guidance to help optimize and troubleshoot Microsoft 365 Apps on your client devices.
A. Inventory
B. Microsoft 365 Apps health
C. Security update status
D. Servicing profile
Correct Answer: B
Explanation
Option B is correct – Microsoft 365 Apps health monitors reliability and performance metrics and provides custom guidance to help optimize and troubleshoot Microsoft 365 Apps on your client devices.
Option A is incorrect – You can use the inventory page to see information about the devices in your organization, including hardware, operating system, and the Office software running on that device.
Option C is incorrect – You can use the security update status page in the Microsoft 365 Apps admin center to see which devices have installed the latest security updates for Office.
Option D is incorrect – With servicing profiles, you can automatically deliver monthly Office updates for specific users or groups.
Reference: https://docs.microsoft.com/en-us/deployoffice/admincenter/overview
Domain: Deploy Windows client
Question 12: An organization manually deploys Enterprise or Education edition images for thousands of FAT machines, enters the Key Management services or Multiple Activation Key, and restarts the device. This causes a huge hit on SLA as they are unable to meet clients’ requirements due to this tedious process. How can they implement a change to improve this situation?
A. Use Inherited Activation
B. Use MAK
C. Use Subscription Activation
D. Use CSP program
Correct Answer: C
Explanation
Option C is correct: The Subscription Activation feature eliminates the need to manually deploy Enterprise or Education edition images on each target device, then later relying upon on-premises key management services such as KMS or MAK based activation, entering Generic Volume License Keys (GVLKs), and subsequently rebooting client devices.
Option A is incorrect: Inherited Activation is a new feature available in Windows 10, version 1803 or later (Windows 11) that allows Windows 10/11 virtual machines to inherit activation state from their Windows 10/11 host. This will be applicable only when Virtual Machines activations are involved.
Option B is incorrect: Multiple Activation Key (MAK) activation is used for one-time activation through Microsoft-hosted activation services, either via the internet or by telephone. However, without Subscription activation, the IT Department needs to rely on the traditional method of rebooting the device.
Option D is incorrect: CSP (Cloud Solution Provider) is similar to the Subscription Activation feature but on a smaller scale.
Reference: https://docs.microsoft.com/en-us/windows/deployment/windows-10-subscription-activation
Domain: Manage identity and compliance
Question 13: An user was unable to log in to Azure Active Directory(AD) even though they have valid credentials, but they were able to log in when they are connected to the corporate network. What could be the issue?
A. AD user account was created before federated authentication
B. Password hash was not synchronized to the cloud
C. Legacy password hashes for NTLM + Kerberos authentication are required
D. The hashing algorithm has failed
Correct Answer: A
Explanation
Option A is correct: Azure AD user accounts created before federation authentication services might have an old password hash, so this doesn’t match a hash of their on-premises password. Hence, Azure Active Directory Domain Services (Azure AD DS) won’t be able to validate a user’s credentials.
Option B is incorrect: The password hash synchronization process runs every 2 minutes and it is streamlined to the cloud which cannot cause the issue.
Option C is incorrect: The user already accessed the AD while on-premises so the Legacy password hashes for NTLM (New Technology LAN Manager) + Kerberos authentication are already enabled and accessed.
Option D is incorrect: the hashing algorithm is automated and cannot be modified or reverted. Once the password is entered while on-premises, the existing password in the cloud is overwritten.
Reference: https://docs.microsoft.com/en-us/azure/active-directory-domain-services/compare-identity-solutions
Domain: Manage identity and compliance
Question 14: Markle is a Law Firm located in New Jersey and you recently joined the firm as Desktop Administrator. One of the top executives forgot the password and used the self-service password reset functionality of Azure AD. What are the alternative methods of authentication for users that have forgotten their passwords?
A. Security questions, Office phone, Mobile Phone, Alternative email address
B. Mobile phone, Alternative email address, Security questions, Biometric thumbprint
C. Office phone, Mobile phone, Text message to any phone number, Security questions
D. Challenge Handshake Authentication Protocol, or CHAP, Office phone, Mobile Phone, Alternative email address
Correct Answer: A
Explanation
Option A is correct – This functionality can be enabled for all users or a group of users.
Option B is incorrect – A biometric thumbprint is not yet available for Azure AD.
Option C is incorrect – Text Message or One Time Password is sent only to a registered number.
Option D is incorrect – Challenge Handshake Authentication Protocol or CHAP is not a part of Azure AD.
Domain: Manage identity and compliance
Question 15: As an Enterprise Admin in Gagle’s IT Department, you are assigned a task to configure a mobile device setting or policy that specifies whether Gagle allows or blocks access to Exchange mail for devices that aren’t supported by Basic Mobility and Security. Which of the following mobile device settings or policies should you use to make this requirement possible?
A. Device Compliance Policies
B. Organization-Wide Device Access Settings
C. Device Security Policies
D. Conditional Access
Correct Answer: A
Explanation
Option B is correct – Organization-wide device access settings enable an organization to specify whether it wants to allow or block access to Exchange mail for devices that aren’t supported by Basic Mobility and Security and which security groups should be excluded from access control.
Option A is incorrect – Device compliance policies are an Intune feature that defines the rules and settings that users and managed devices must meet to be compliant.
Option C is incorrect – Organizations can use device security policies to protect their devices from unauthorized access.
Option D is incorrect – Conditional Access policies are enforced after first-factor authentication is completed. Conditional Access isn’t intended to be an organization’s first line of defense
Domain: Manage, maintain, and protect devices
Question 16: Whizlabs want to restrict specific content for the users due to security reasons. However, they are worried about line-of-business applications since many line-of-business applications are written with limited security concerns. How can an organization deploy attack surface reduction rules without affecting the productivity of its users?
A. Enable Notification and alerts
B. Enable Block mode
C. Enable Warn mode
D. Enable Audit mode
Correct Answer: D
Explanation
Option D is correct – Organizations should use audit mode to evaluate how attack surface reduction rules would affect them if enabled. They should also run all rules in audit mode first so they can understand how the rules affect their line-of-business applications. Many line-of-business applications are written with limited security concerns. As such, they may perform tasks in ways that seem similar to malware. By monitoring audit data and adding exclusions for necessary applications, organizations can deploy attack surface reduction rules without reducing productivity.
Option A is incorrect – Whenever an attack surface reduction rule is triggered, a notification and an optional alert are displayed on the device but it doesn’t prevent users from accessing the restricted contents.
Option B is incorrect – Enabling the block mode directly will result in affecting the line-of-business apps and can affect their day to day tasks of the users.
Option C is incorrect – With the introduction of warn mode, whenever the content is blocked by an attack surface reduction rule, users see a dialog box that indicates the content is blocked. The dialog box also offers the user an option to unblock the content, which may lead to exposing the restricted content to the users.
Domain: Manage, maintain, and protect devices
Question 17: Which of the following is a cloud protection service and enhances standard real-time protection, providing arguably the best antivirus defense on the cloud?
A. Microsoft Sentinel
B. Microsoft Defender for Cloud
C. Microsoft Advanced Protection Service (MAPS)
D. Microsoft Defender for Identity
Correct Answer: C
Explanation
Option C is correct – Microsoft Defender Antivirus works seamlessly with Microsoft cloud services. These cloud protection services, also referred to as Microsoft Advanced Protection Service (MAPS), enhance standard real-time protection, providing arguably the best antivirus defense. Cloud protection is critical to preventing breaches from malware and a critical component of attack surface reduction rules.
Option A is incorrect – Microsoft Sentinel delivers intelligent security analytics and threat intelligence across the enterprise. With Microsoft Sentinel, you get a single solution for attack detection, threat visibility, proactive hunting, and threat response.
Option B is incorrect – Defender for Cloud helps you limit exposure to brute force attacks. By reducing access to virtual machine ports, using the just-in-time VM access, you can harden your network by preventing unnecessary access. You can set secure access policies on selected ports, for only authorized users, allowed source IP address ranges or IP addresses, and for a limited amount of time.
Option D is incorrect – Microsoft Defender for Identity (formerly Azure Advanced Threat Protection, also known as Azure ATP) is a cloud-based security solution that leverages your on-premises Active Directory signals to identify, detect, and investigate advanced threats, compromised identities, and malicious insider actions directed at your organization.
References: https://docs.microsoft.com/en-us/learn/modules/implement-endpoint-security-microsoft-intune/7-implement-attack-surface-reduction-rules, https://docs.microsoft.com/en-us/azure/sentinel/overview, https://docs.microsoft.com/en-us/azure/defender-for-cloud/defender-for-cloud-introduction, https://docs.microsoft.com/en-us/defender-for-identity/what-is
Domain: Manage, maintain, and protect devices
Question 18: What are the factors that Threat and Vulnerability Management prioritize vulnerabilities in Microsoft Defender for Endpoint?
A. The Threat landscape
B. Non-Sensitive information
C. Detections in your organization
D. Business context
Correct Answers: A, C and D
Explanation
Options A, C and D are correct – The Threat and Vulnerability Management module serves as an infrastructure for reducing organizational exposure, hardening endpoint surface area, and increasing organizational resilience. It uses sensors to discover vulnerabilities and misconfigurations in real-time. This discovery is completed without the need for agents or periodic scans. Threat and Vulnerability Management prioritizes vulnerabilities based on:
- the threat landscape
- detections in your organization
- sensitive information on vulnerable devices
- business context
Option B is incorrect – Non-sensitive information is often considered as public data and won’t be a security threat to an organization.
Domain: Manage, maintain, and protect devices
Question 19: As a system administrator, you are running the Threat and vulnerability management exposure score, followed by Microsoft Secure Store for Devices for investigation purposes. You found out that one of the devices which is not active for nearly 90 days has not been factored in the exposure score run by you. Can you please provide an explanation on why the specific device was not factored?
A. The device was considered an exposed device
B. Analysis has found software vulnerability in that device
C. Device must be active in the last 30 days to be factored
D. Device has been marked for remediation activities which refrain itself from the evaluation
Correct Answer: C
Explanation
Option C is correct – Devices must be active in the last 30 days to be factored in on the data that reflects an organization’s threat and vulnerability management exposure score and Microsoft Secure Score for Devices.
Option A is incorrect – Even though marked as an exposed device, the device should be factored in during the evaluation.
Option B is incorrect – Only after the evaluation is performed by the threat and Vulnerability Management capability in the Microsoft 365 Defender, we can find out whether the device has software vulnerability.
Option D is incorrect – Device marked for remediation activities will not be refraining itself from the threat and vulnerability management exposure score and Microsoft Secure Score for Devices.
Domain: Manage, maintain, and protect devices
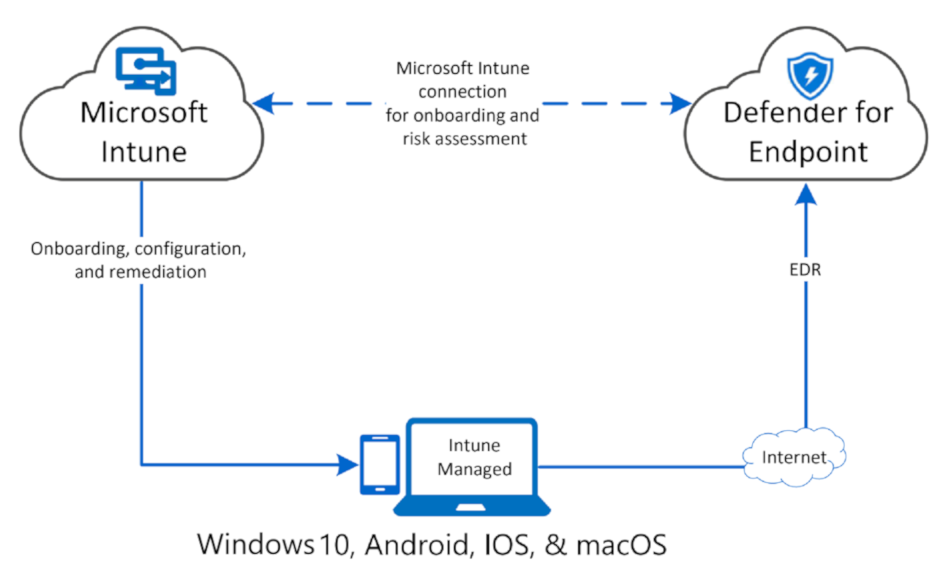
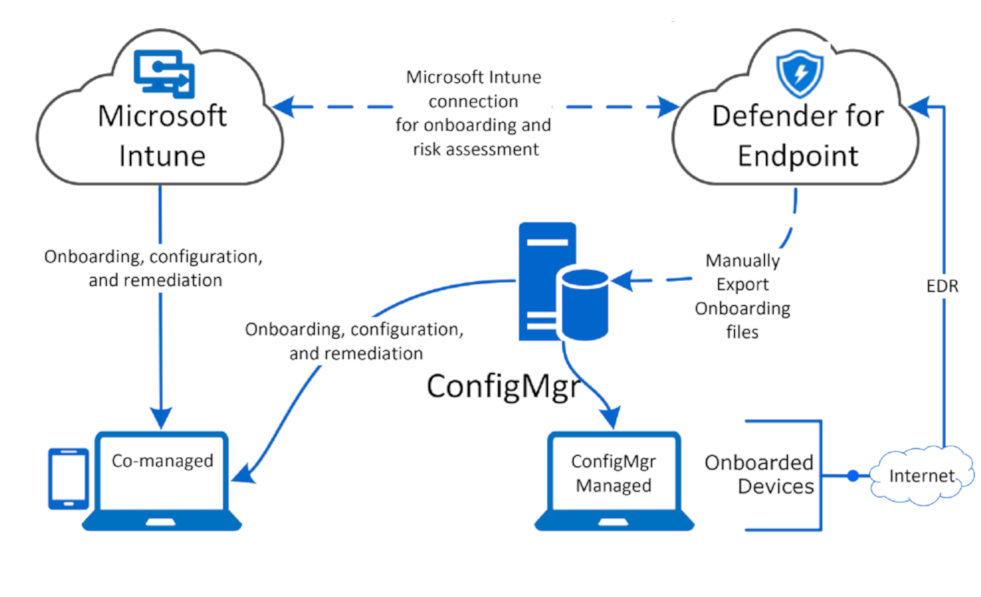
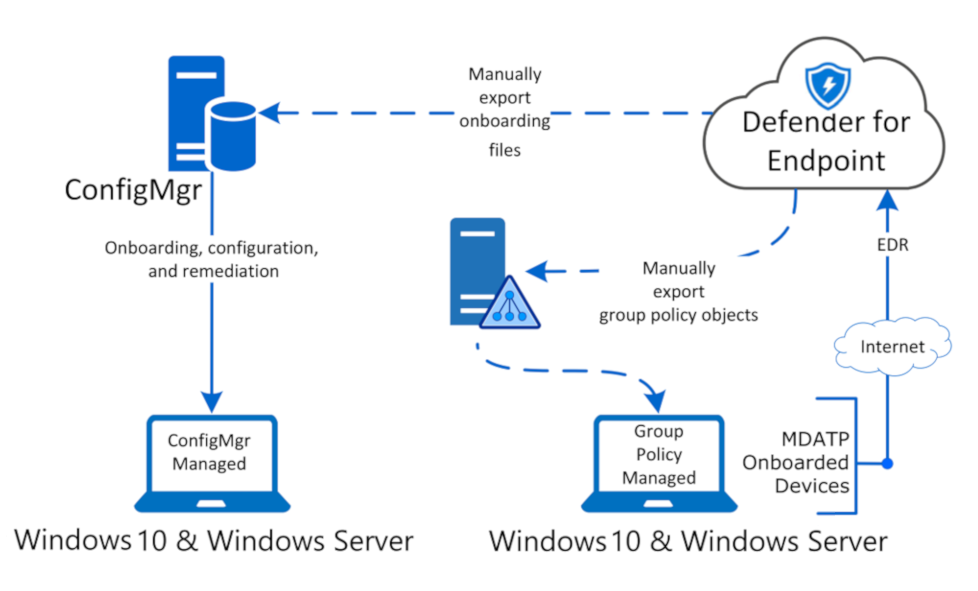
Question 20: Each architecture type has a selection of tools to use for onboarding devices to Microsoft Defender for Endpoint. Please drag and drop to match tools based on the architecture.
| Cloud-native | Microsoft Endpoint Manager, Configuration Manager |
| Co-management | Configuration Manager, Group Policy |
| On-premises | Microsoft Endpoint Manager |
Correct Answer: 1-C, 2-A and 3-B
Explanation
- Cloud-native
Microsoft Endpoint Manager
- Co-management
Microsoft Endpoint Manager, Configuration Manager
- On-premises
Configuration Manager, Group Policy
You can use Microsoft Defender for Endpoint in your environment in different ways to meet your needs. The first step is to classify how your company is structured. Choose the architecture that best maps to your needs.
Cloud-native – You should choose a cloud-native architecture if your organization’s devices are based in the cloud. For example, if all devices are managed by Microsoft Endpoint Manager, or if your organization would like to move to them in the future to be managed by Microsoft Endpoint Manager.
Co-management – Choose co-management if you have a blended architecture, with devices managed by Microsoft Endpoint Manager and an on-premises configuration management solution.
On-premises – Choose an on-premises architecture if all your devices are using either Configuration Manager or Active Directory Domain Services. Your organization can still benefit from using the power of the cloud-based Microsoft Defender for Endpoint.
Reference: https://docs.microsoft.com/en-us/learn/modules/m365-get-started-defender-endpoint/plan
Domain: Manage, maintain, and protect devices
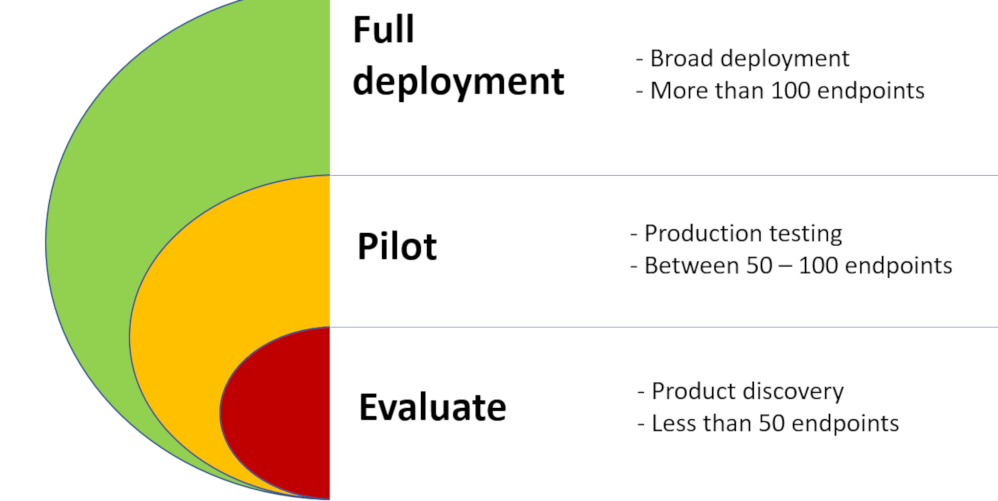
Question 21: What are the Microsoft recommended deployment ring structure to use with Microsoft Defender for Endpoint?
A. Pilot
B. Evaluate
C. Full Deployment
D. Exit Criteria
Correct Answers: A, B and C
Explanation
Option A, B and C are correct – You need to define deployment rings. Using deployment rings, you onboard a set number of devices first, look for potential issues and then address those issues before you go to the next set of devices. This is useful for your scenario because you don’t want to onboard all your devices in one go.
- Evaluate – You choose a relatively small number of test devices (up to 50) to onboard. You test the devices in this ring to ensure that they meet your exit criteria before you move to the next ring. Exit criteria can include confirming whether the devices show up in the devices list and whether alerts are showing up in the dashboard.
- Pilot – If the devices have passed the evaluation ring, you can then move up to this deployment ring. You choose more devices to onboard (between 50 to 100 devices). Then if the devices pass your exit criteria, you proceed to the next deployment ring.
- Full deployment – If the devices have passed the pilot ring, you can move to this final ring, where you onboard the rest of your devices in increments. Use the deployment link in the Learn more section to access best practice material on how to do this.
Option D is incorrect – Exit criteria is already a part of the evaluation process so you don’t need to define it separately to consider it as one of the deployment ring structures.
Reference: https://docs.microsoft.com/en-us/learn/modules/m365-get-started-defender-endpoint/plan
Domain: Manage, maintain, and protect devices
Question 22: Since you are a new recruit as an Enterprise Administrator, you are being questioned by your seniors to test your knowledge on Microsoft Defender for Endpoint. They asked you to evaluate the devices and block sophisticated threats and malwares which can be a security concern for an organization. Also, they have requested you to configure the device to stop any malicious activity from installed applications. How will you fulfill their requirement by using one of the below components of Microsoft Defender for Endpoint?
A. Threat and vulnerability management
B. Next generation protection
C. Attack surface reduction
D. Microsoft Threat Experts
Correct Answer: B
Explanation
Option B is correct – You can use Microsoft Defender for Endpoint’s next generation protection to block sophisticated threats and malware. With it, you can leverage a combination of both client-based and cloud-based protection engines and machine learning. You’re able to use behavior-based real-time protection, block file-based, and fileless malware, and stop malicious activity from applications.
Option A is incorrect – Threat and vulnerability management uses a risk-based based approach that can help you discover, prioritize, and remediate endpoint vulnerabilities and misconfigurations.
Option C is incorrect – Attack surface reduction eliminates risks by ensuring device settings are correctly configured with capabilities such as hardware-based isolation, application control, network and web protection, and more. You can use granular controls through rules that target certain software behaviors to keep your organization safe.
Option D is incorrect – Microsoft Threat Experts is a managed service to get access to security experts. You can use it to get access to insights that you can use to better understand threats and take appropriate action. This is a separate service, so it’s not a direct capability of Microsoft Defender for Endpoint.
Reference: https://docs.microsoft.com/en-us/learn/modules/m365-get-started-defender-endpoint/prepare
Domain: Manage, maintain, and protect devices
Question 23: What are the right steps that are involved in the deployment process for device onboarding to Microsoft Defender using Microsoft Endpoint Manager?
A. Configure Microsoft Defender for Endpoint capabilities, create a group, then verify config policies have been applied
B. Configure capabilities, verify config policies have been applied, then create a group
C. Create a group, configure Microsoft Defender for Endpoint capabilities, then verify config policies have been applied
D. Verify config policies, create a group, then configure Microsoft Defender for Endpoint capabilities
Correct Answer: C
Explanation
Option C is correct – The deployment process using Microsoft Endpoint Manager consists of the following steps:
-
- Create a group in Microsoft Endpoint Manager to assign configurations to target devices or users
- Configure Microsoft Defender for Endpoint capabilities that you’ll need using Microsoft Endpoint Manager.
- Verify that your configuration policies for capabilities have been applied.
Options A, B and D are incorrect – These are not the correct sequence of steps that are involved in the deployment process.
Domain: Manage, maintain, and protect devices
Question 24: Please select the correct sequence from the below steps for creating a device group in Microsoft Defender for Endpoint.
A. Preview several devices that will be matched by this rule. If you’re satisfied with the rule, select the User access tab
B. In the navigation pane, select Settings, select Endpoints and then under Permissions select Device groups and select + Add device group
C. Assign the user groups that can access the device group you created. You can only grant access to Azure AD user groups that have been assigned to RBAC roles and select Close
D. Enter the group name and automation settings and specify the matching rule that determines which devices belong to the group. See How the automated investigation starts
Correct Answers: B, D, A and C
Explanation
- In the navigation pane, select Settings, select Endpoints, and then under Permissions select Device groups and select + Add device group.
- Enter the group name and automation settings and specify the matching rule that determines which devices belong to the group. See How the automated investigation starts.
- Preview several devices that will be matched by this rule. If you’re satisfied with the rule, select the User access tab.
- Assign the user groups that can access the device group you created. You can only grant access to Azure AD user groups that have been assigned to RBAC roles and select Close.
Statement – In Microsoft Defender for Endpoint, you can create device groups in the context of role-based access (RBAC) to control who can take specific action or see information by assigning the device group(s) to a user group. and use them to:
- Limit access to related alerts and data to specific Azure AD user groups with assigned RBAC roles
- Configure different auto-remediation settings for different sets of devices
- Assign specific remediation levels to apply during automated investigations
Domain: Manage, maintain, and protect devices
Question 25: By enabling me, I can help you in cyber attacks by locking your security settings from being changed through apps and methods and I am exclusively available when you use Microsoft Defender Antivirus and Cloud-based protection is enabled. Can you find my name from the below-advanced features available in Microsoft Defender for Endpoint?
A. Endpoint detection and response (EDR) in block mode
B. Microsoft Threat Experts – Targeted Attack Notifications
C. Office 365 Threat Intelligence connection
D. Tamper protection
Correct Answer: D
Explanation
Option D is correct – During some kinds of cyber attacks, hackers can try to disable security features, such as anti-virus protection, on your machines. Hackers like to disable your security features to get easier access to your data, install malware, or otherwise exploit your data, identity, and devices. Tamper protection essentially locks Microsoft Defender Antivirus and prevents your security settings from being changed through apps and methods.
Option A is incorrect – Endpoint detection and response (EDR) in block mode work behind the scenes to remediate malicious artifacts that are detected post-breach and provides protection from malicious artifacts, even when Microsoft Defender Antivirus is running in passive mode. When turned on, EDR in block mode blocks malicious artifacts or behaviors that are detected on a device.
Option B is incorrect – You can only use the experts-on-demand capability if you’ve applied for preview and your application has been approved. You can receive targeted attack notifications from Microsoft Threat Experts through your portal’s alerts dashboard and via email if you configure it.
Option C is incorrect – This feature is only available if you have an active Office 365 E5 or the Threat Intelligence add-on. When you turn on this feature, you’ll be able to incorporate data from Microsoft Defender for Office 365 into Microsoft 365 Defender to conduct a comprehensive security investigation across Office 365 mailboxes and Windows devices.
Conclusion
Passing the MD-102 exam not only validates their expertise but also opens up new career opportunities in the ever-evolving field of IT administration. Apart from MD-102 Free Exam Questions, we offer MD-102 Study Guides, and MD-102 Practice test. We do not offer MD-102 exam dumps at any cost.
To excel in this certification, continuous learning and hands-on experience are key, ensuring that IT professionals remain well-equipped to address the challenges of managing modern desktops in today’s dynamic technology landscape.
You can get real-time hands-on experience by utilizing our Azure hands-on labs, and Azure sandbox.
- A Tour of Google Cloud Hands-on Labs - December 12, 2023
- Mastering Azure Basics: A Deep Dive into AZ-900 Exam Domains - December 4, 2023
- Exploring the Benefits of Validation Feature in Hands-on Labs - October 10, 2023
- 20+ Free MD-102 Exam Questions on Microsoft Endpoint Administrator - September 27, 2023
- 20+ Free MS-102 Exam Questions on Microsoft 365 Administrator Certification - September 25, 2023
- AWS Certified Developer Salary in 2024 - September 19, 2023
- Guide to SharePoint, OneDrive, and Teams External Sharing in Teams - September 10, 2023
- What is Cross-Tenant Synchronization | MS-700 Certification - August 31, 2023