Azure Security Center is a collective infrastructure that promotes the security management aspect within the Azure service space. The main role of the Azure Security Center is to add strength to the entire security posture of the Azure datacenters. Along with that, it ensures proficient threat protection for the hybrid workloads within the cloud. It does not matter whether you are within the Azure cloud or not; Azure Security Center has the potential to offer you threat management for all types of hybrid workloads within different clouds.
Azure Security Center is best at keeping the important resources safe. It is termed to be a collective effort implemented by Azure, cloud provider, and you. Before you can implement the workloads and move them to the cloud, you need to take concern for their secure existence. And, Azure Security Manager offers you the feasibility of securing the workloads. Azure Security Center equips you with the necessary tools that intend to harden the network, secure the services and streamline the security aspects of it for seamless execution.
So, if you are in a conflict about whether to trust Azure Security Center or not, then this article intends to help you out with the core fundamentals and concepts within it. Follow this article till the end to ensure that you master all of the concepts and knowledge associated with Microsoft Azure Security Center.
Brief Overview of Microsoft Azure Security Center
Microsoft is actively integrating several physical, operational, and infrastructure controls to help secure the Azure cloud services. Apart from that, it would be best to take utmost security concerns for a few of the additional actions. Azure Security Center has the potential to safeguard the workloads right from the moment you enable it! It will strengthen the cloud security aspects of the infrastructure. Therefore, Azure Security Center intends to offer you protection against all types of hybrid workloads within Azure or other clouds.
Azure Security Center makes use of Azure Defender to offer such high-level security to the cloud infrastructure. It assesses and visualizes the state of security for all of the Azure resources. Moreover, it has the potential to simplify enterprise security compliance and monitor it against all of the regulatory requirements. The best part is that the Azure Security Center makes use of AI and automation for putting up an exception for turning down all the false alarming situations. Following that, it intends to identify the threats as quickly as possible for streamlining the threat investigation and recovery.
With Azure Security Center, you can assess all the cloud resources, storage, applications, networks, workloads, and SQL. When you get an idea about the security state of all these resources, you can intend to work upon enhancing their potential. Moreover, if you wish to monitor the state of security and secure-posture of the cloud infrastructure, then you can use Azure Secure Score for the same. Microsoft Azure Security Center allows you to commence with easy deployment on large-scale environments by integrating the use of automation and policies. With Azure Security Center, you can streamline the pathway for threat investigation, and the remediation process can be automated as well.
The Architecture of Azure Security Center
The next important aspect of understanding the Microsoft Azure Security Center is the Azure security center architecture. Understanding the architecture could help us in evaluating how it works for ensuring the security of cloud workloads. Security Center is a native component of Azure. So, the security center provides monitoring and protection for PaaS services on Azure such as SQL databases, storage accounts, and Service Fabric without the need for any deployment.
The security center also provides safeguards for non-Azure servers and virtual machines on-premises or in the cloud. Azure Security Center ensures protection for both Windows and Linux server environments through the installation of Log Analytics agent on them. Most important of all, the security center also ensures the auto-provisioning of Azure virtual machines.
The next important highlight in Azure security center architecture is the security analytics engine. Readers should note that the security analytics engine helps in correlating the events collected from Azure and from the agents. Based on the results of correlation, the security analytics engine provides reliable recommendations for strengthening the security systems.
For example, you can get recommendations for ensuring the security status of workloads or create customized security alerts. The alerts by the security analytics engine should be the foremost priority of security administrators. Quick and proactive investigation of security alerts can help in preventing any malicious attacks on your workloads.
The Azure security center architecture also depends on the in-built security policy of the security center. You can find it as an in-built initiative in Azure Policy under the Security Center category upon enabling the security center. The in-built initiative is assigned automatically to all registered Security Center subscriptions.
It is essential to note that this in-built initiative in Azure security center architecture comprises of Audit policies only. However, you don’t have to worry about leveraging the maximum potential of Microsoft Azure Security Center. You can always try the official Azure security documentation to excavate additional information about security center policies.
How Does Azure Security Center Work?
Now that you have reflected on the architecture of Azure security center it is important to know how it works. Upon activating the security center, you will have an automatic deployment of a monitoring agent to Azure virtual machines. In the case of on-premise virtual machines, you have to deploy the monitoring agent manually.
Then the security center starts assessment of security status in all your virtual machines, applications, data and networks. Reflecting upon any Azure security center tutorial in detail, you can find that the analytics engine helps in data analysis. Subsequently, machine learning helps in data synthesis and providing recommendations and threat alerts for safeguarding workloads.
Therefore, Azure security center helps in faster identification of any threat or anomalous activity. Users can aggregate their security information in Azure Monitor workspace to ensure big data querying capabilities. In addition, users can also choose for querying through PowerShell cmdlets, integration with an existing SIEM (Security Information and Event Management) tool such as Azure Sentinel or REST APIs.
Security Challenges Attended By Azure Security Center
Azure Security Center can be well understood by getting insight into the right potential of how it attends to the major security challenges. There are three security challenges that are of utmost concern, and Azure Security Center has the potential to attend and sort them out. The challenges include:
-
Workloads Tend to Change Rapidly
Rapid changing workloads are considerably a strength to cloud operations but are also a progressive challenge that the security concerns need to attend to on priority. The end-users also intend to implement more of their measures to tweak the workloads. Apart from that, you need to be sure of the fact that all of the ever-changing cloud services used by people meet the security standards. Azure Security Center intends to offer you ideal protection to ensure the security of those practices, even though the workloads change frequently.
-
Lack of Security Skills
The administrators within the organizational space are responsible for protecting the cloud environment that is carrying out your services. The biggest challenges for the organizations operating within the cloud are to stay updated with the new possible attacks. It is quite impossible to stick to just one security front when the demands are ever-changing within the organizational space. Therefore, along with the security administrators, it is important for you to take the assistance of Azure Security Center.
-
Rapid Increase in Impactful Attacks
It doesn’t matter where you run the workloads; the attacks are worsening over time and are accountable to be more sophisticated. And to take a step towards staying prepared for such attacks, it is important that you intend to secure the public cloud workloads. Make sure that those public workloads are in effect. Most of the internet workloads that are not embedded with the security practices are possibly more vulnerable to such attacks. Therefore, implementing the Azure Security Center is ideal for this purpose.
Azure Security Center has the potential to help you protect against all of these challenges with the right availability of tools and solutions. The tools within Azure Security Center intend to help you come up with efficacies such as:
- It allows you to strengthen the security posture of your entire cloud infrastructure. It assesses the environment upon which your business operates and will enable you to get insight into the resource status, to know whether they are secure or not.
- It will help you get complete protection against some of the major threats by assessing the workloads. Following that, it will trigger the threat prevention alerts and recommendations.
- Faster security is yet another potential of Azure Security Center, as everything within this initiative is done with respect to cloud speed. Azure Security Center is a native integration, and the deployment of it is quite easy. Therefore, it offers you protection and auto-provisioning with the respective Azure services.
The Use of Azure Defender within the Security Center
Azure Defender is the dashboard or tool that is embedded within the Security Center in order to offer control and visibility of all the CWP features within the environment. The features of Azure Security Center intend to cover the two massive pillars of cloud security, which include Cloud Security Posture Management (CSPM) and Cloud Workload Protection (CWP).
Azure Defender within the security Center offers threat protection and security alerts for VMs, containers, web apps, networks, SQL databases, and more. You need to enable Azure Defender from the ‘Pricing and Settings’ tab over the Azure Security Center. There are specific Defender plans that are embedded within the Azure Security Center. Different plans have the different potential of offering comprehensive defenses for computing, service, and data layers within the environment.
With Azure Defender, you can secure the servers, app service, SQL, Kubernetes, storage, Key Vault, Container Registries, Resource Manager, DNS, and Open-source Relational Databases. Refer to this documentation to understand how Azure Security Center and Defender offer security to these resources. There is a separate product as Azure Defender for IoT that has a different significance. Follow this documentation to know more about how this product is implemented.
How to Enable Security Center to your Azure Subscriptions?
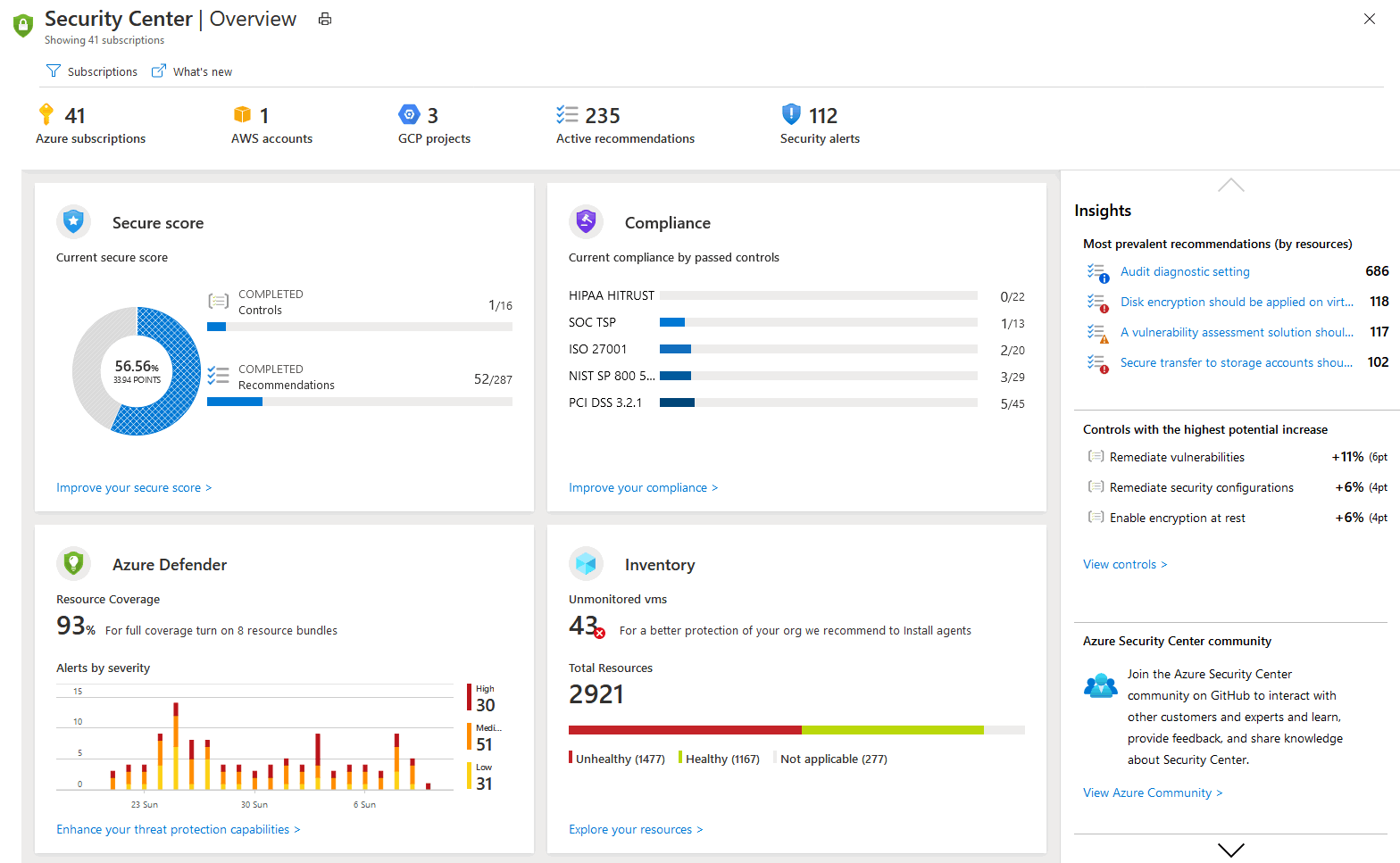
Azure Security Center offers collective security management & threat protection across multi-cloud and hybrid workloads. There are free features within Azure Security Center, but they intend to offer limited security that is eligible only for the Azure resources. But, when you subscribe to Azure Defender, you will eventually enhance the efficacy to higher capabilities for integrating security to not just Azure cloud but others as well.
With Azure Defender, you can intend to find and rectify the vulnerabilities and security concerns within diverse cloud infrastructures. Apart from that, you can apply accessibility and application control to block all malicious activities. Hence, you can detect the threats with the help of analytics and intelligence to respond quickly when the cloud encounters any attack. Trying out Azure Defender comes at no cost. However, to use its full potential, you need to choose one of the plans that vary in price. For more information on the pricing, check out this pricing chart or documentation.
Before getting started with the steps for enabling Microsoft Azure Security Center onto your subscriptions, it is important that you have a subscription to Microsoft Azure. In case you do not have a subscription, you can always sign-up and create a free account for the same. Once you have done that, here are the next steps that you need to follow for enabling security center to your subscription:
- To begin with, sign in to your Azure Portal by entering your credentials over this link.
- Now, head to the menu over the Azure Portal, and choose the option ‘Security Center’.
- You will be redirected to the overview page of the Security Center that will give you an insight into the hybrid cloud security posture. Hence, it will enable you to assess and discover the workload security.
- It automatically enables Security Center to the available Azure Subscriptions.
- After launching the security center, you will then get to see the recommendations, based upon which you can improve the resource security that is connected within the portal.
- You will also get to see the resource inventory that is currently being checked by the Azure Security Center. And you will also get an insight into the security posture of each of the resources within the cloud.
For a quick start, you need to enable Azure Defender within Security Center, for storage accounts and SQL, for either resource or subscription levels. But for enabling Azure Defender for Open-Source Relational Databases, you can integrate it only at the resource level. For enabling the Azure Defender attributes within the workspaces and subscriptions, you need to follow specified steps again, that includes:
For Enabling Azure Defender on a Single Subscription
- Head to the main menu of the Security Center, select the tab “Pricing and Settings.”
- Select the subscription that you wish to protect within your cloud infrastructure.
- Now, select ‘Azure Defender on’ to upgrade the security aspects.
- Now, select ‘Save.’
For Enabling Azure Defender on Multiple Workspaces or Subscriptions
- Explore the sidebar of Security Center, and click on the ‘Getting Started’ tab.
- Now, head to the ‘Upgrade’ tab that consists of the list full of workspaces and subscriptions that are eligible for onboarding.
- Now, visit the ‘Select Subscriptions & Workspaces to Enable Azure Defender on” list. Select the workspaces and subscriptions that you intend to upgrade.
- Now, select ‘Upgrade’ for enabling Azure Defender.
If you are choosing the subscriptions that are not ready for the trial over Azure Defender, then the security center will upgrade them in the following step. And the charges will begin from that moment! But if you are picking up workspaces or subscriptions that are ready for the free trial, then you can check the working of Azure Defender for free before the charges are imposed!
Disabling Azure Defender
When you know how to enable Azure Defender within the Azure Security Center for your resource protection, you must also have the knowledge to disable it at the time of need. The steps for the same are:
- Head to the menu of Azure Security Center, and select the tab ‘Pricings and Settings.’
- Now choose the relevant subscription enabled with Azure Defender that you wish to disable.
- Now, head to the Azure Defender plans and then select the tab “Azure Defender off.”
- Now, you need to select ‘Save.’
Best Practices for Azure Security Center
Apart from the functionalities of Azure security center, it is highly important for users to follow the best practices. The best practices enable users to apply the security center functionalities optimally according to their security requirements. Here are some of the notable Azure security best practices that can ensure the best cloud security management.
-
Know the Shared Responsibility Model of Microsoft Azure
The foremost prerequisite for operating Microsoft Azure is the knowledge of the Shared Responsibility Model of Azure. The model implies the distribution of responsibilities of cloud security between the user and Microsoft. However, the allocation of responsibility varies according to the type of Azure service in use. The user can achieve many promising outcomes from Microsoft Azure Security Center by understanding the Shared Responsibility Model of Azure.
First of all, enterprises can help in the proper migration of businesses to the cloud. In addition, you can ensure comprehensive protection for applications, users, corporate secrets, services, certificates, keys, data and other critical information. Most important of all, you can make the optimal use of all security benefits that Microsoft provides.
-
Address Identity-Related Security Concerns
Another prominent mention among azure security best practices is the resolution of identity-related security issues through Azure Active Directory. Identity has become one of the critical security issues with the rising adoption of cloud services. Therefore, it is important for users to follow the recommended best practices for securing identity through Azure Active Directory.
First of all, users can go for the centralization of identity into a single authoritative source. For example, you can use Azure Active Directory Connect for integrating cloud directories and on-premises. The Single Sign-On (SSO) option by Azure Active Directory is also a reliable best practice to boost your security posture. The next critical best practice for Azure security center would be the use of two-step multi-factor authentication.
Summary
This article will help you understand and implement the rightful use of Azure Defender and Azure Security Center upon your subscriptions. It is important that you get an idea of how this entire service functions in order to leverage its potential.
Check out the pricing and plans of Azure Security Center to ensure that you enable security configuration for your selected resources within Azure or other clouds. Get hands-on experience to ensure protection for your cloud infrastructure against malicious attacks and threats.
- Top 20 Questions To Prepare For Certified Kubernetes Administrator Exam - August 16, 2024
- 10 AWS Services to Master for the AWS Developer Associate Exam - August 14, 2024
- Exam Tips for AWS Machine Learning Specialty Certification - August 7, 2024
- Best 15+ AWS Developer Associate hands-on labs in 2024 - July 24, 2024
- Containers vs Virtual Machines: Differences You Should Know - June 24, 2024
- Databricks Launched World’s Most Capable Large Language Model (LLM) - April 26, 2024
- What are the storage options available in Microsoft Azure? - March 14, 2024
- User’s Guide to Getting Started with Google Kubernetes Engine - March 1, 2024

