Cloud technology has opened up a whole new era in IT solutions in terms of storage, flexibility, accessibility, and productivity. As the cloud gives the provision of shared resources, it brings along the new overheads of security concerns. Not only sharing features but also its identity management, access control, and privacy are the points of concern. Thus for organizations using cloud computing as well as for the cloud vendors providing services – cloud security is a high priority.
In this blog, we will cover what is cloud security and the different aspects of cloud security like possible risks, challenges, and solutions. Also, we will have a look over the list of the most in-demand cloud security certification.
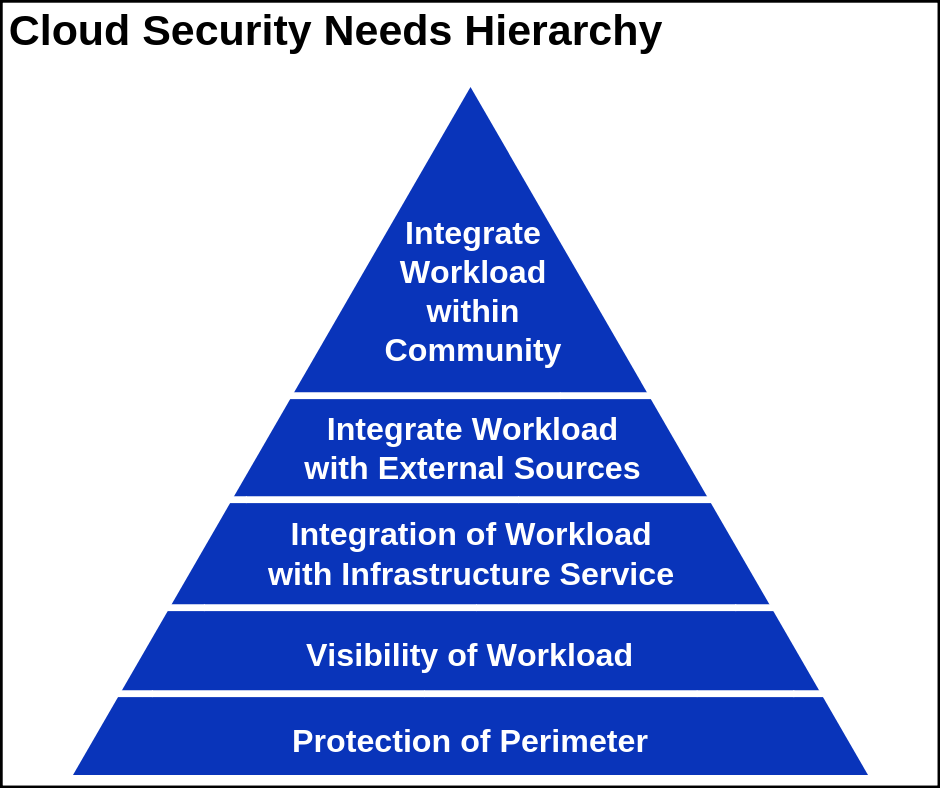
What is Cloud Security?
Cloud security is similar to IT security in on-premises data centers. However, it does not need any hardware or maintenance facility. Cloud security solutions are provided using software tools that protect and monitor the information flow in the cloud resources. Hence, there is no need for physical storage devices or servers. Using various security measures, we can prevent data theft, data leakage, and unwanted data deletion.
In a broad sense, cloud security is a subdomain of information security which comprises the computer and network security. However, it has its own set of policies, controls, and technologies to protect cloud data, applications, and infrastructure.
What are the Various Cloud Security Risks?
Cloud security challenges may come in different ways. The most vulnerable are as below:
1. Account Hijack
Account hijack is a growing threat in the IT industry due to open access to the cloud platform. It has enhanced credential compromise like login details by attackers to make them successful in accessing sensitive user information in the cloud. Moreover, they can manipulate the information using the hijacked credentials. Sometimes hijackers use the cloud for stealing credentials by injecting cross-site scripting bug.
2. Insider Threat
Every company maintains some quality control measures in terms of its process, data security, data sharing, and access. When any violation happens to that by the employees, it is called an insider threat. Though it is very unlikely to happen inside an organization, the insider threat is a viable security issue in the cloud. In such a scenario, an employee can misuse his authorized access to access organization’s cloud-based services such as customer accounts, financial information, and other sensitive information.
Also Read: Top 5 Cloud Certifications in 2018
3. Malware Injection
Malware injections are the code or scripts which are used for malicious activities in the cloud. They are embedded into valid instances of cloud services and run as Software as a Service (SaaS) to cloud servers. Once such code or scripts are injected, it starts executing and utilizing it. Attackers can compromise the sensitive information along with stealing data.
4. Abuse of Cloud Services
As the cloud leverages the extended facility of storage and services, enterprises whether small or large host a vast amount of data in the cloud. However, this storage solution also allows hosting illegal software, and other digital contents. Consequently it sometimes adversely affect the cloud service providers and their clients. In most of the cases, such contents include pirated software, music, videos or books.
5. Insecure APIs
Application Programming Interfaces (API) is the means to customize the features of cloud services to enhance user cloud experience. Programmers build their own programs and integrate those applications with cloud services for better performance. However, sometimes these APIs are used for authentication, accessibility and encryption purposes, and that’s where the vulnerability lies with it. This increases the security risks.
6. Denial of Service Attacks (DoS)
Denials of Service (DoS) attacks are the kind of cyber attack that does not target to breach the sensitive information. However, they carry long-term effects like making a website and servers unavailable. In addition to that, sometimes it turns down firewalls to perform malicious activities.
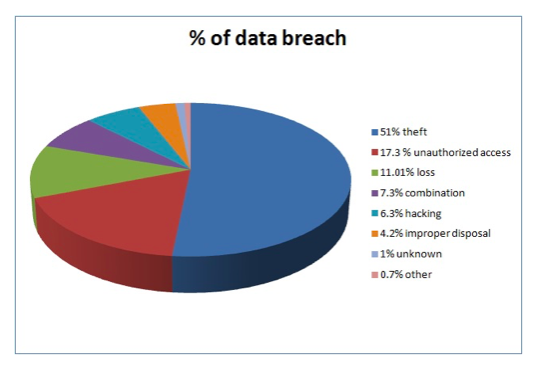
7. Data Breaches
Data breaches are the common problem in IT for years. With the cloud, this problem is more highlighted as the cloud offer open access to data stored online. There are different types of data breaches that happen in cloud platform which is displayed in the below chart.
As per the market survey report, data breach occurrence happens 3 times more in the organizations that use cloud than those of the others. This is because of the cloud’s unique set of characteristics which makes it more vulnerable.
Are you an AWS Security professional? AWS Security Specialty certification recognizes and demonstrates your expertise in AWS Security. Plan now to validate your skills with the AWS Certified Security Speciality exam!
8. Insufficient Due Diligence
Apart from the technical security concern, security issue can arise due to incorrect cloud strategy. This means when an organization is not clear about its policies, organizational goals, and resources, that causes insufficient due diligence which creates the security risk for the company.
9. Shared Vulnerabilities
The security of cloud is a shared goal for the provider and the client. Here the partnership is between the client and the provider where the client needs to take preventive measures to protect data. In case this shared responsibility is omitted, there is a high possibility of comprising security.
10. Data Loss
Cloud service provider must have a proper data recovery plan. The reason behind is that there is a high chance of data loss on cloud services due to:
- Malicious attack
- Natural disaster
- Data removal by the provider
An organization can lose vital information along with these lost data, and it could badly impact an organization. Hence, verifying the provider’s data backup policy is an utmost importance as it is related to physical storage, access, and geographical location of the data centers.
Aspired to become an AWS Certified Cloud Security certification? Follow this preparation guide for the AWS Certified Security Specialty exam and get ahead in your career.
What are the Different Cloud Security Solutions Available?
There are various ways of applying cloud solutions. Some of them are as below:
- Firewalls
- Penetration testing
- Tokenization
- Virtual private networks (VPN)
What are the Benefits of Cloud Security?
In a nutshell, cloud security helps to remove all the security concerns we have mentioned in the previous section. However, cloud security, more importantly, helps to recover the below areas of concerns:
- Cloud DDoS Protection
- High Availability
- Data Security
- Regulatory Compliance
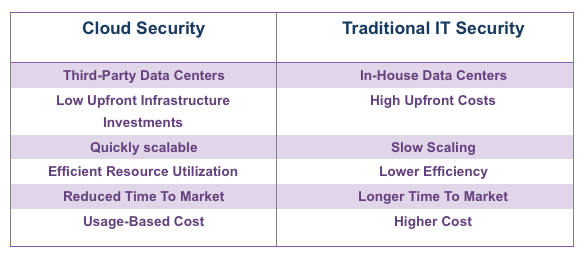
Difference between Cloud Security Solutions and Traditional IT Solutions
Some people may consider cloud security and traditional IT security the same but it’s not. Cloud security is different from traditional IT security in many aspects. Let’s understand the difference between cloud security solutions and traditional IT solutions –
What are the Different Cloud Security Certifications in the IT Industry?
As we have discussed the importance of cloud security from an organizational perspective, it is also engaging more and more cloud professionals to pursue cloud security certifications to make them credible for the role. However, these cloud security certifications are not easy to pass without proper cloud security training. Moreover, there are numerous certifications available in the industry. Here we have highlighted the most prominent ones.
We can categorize cloud security certifications as follows:
- Vendor specific
- Vendor-neutral
Vendor-specific
1. AWS Certified Security –Specialty
- Format: Multiple choices, multiple answers
- Length: 170 minutes, 65 questions
- Languages: English, Japanese, Korean, Simplified Chinese
- Registration Fee: 300 USD
2. Cisco Certified Network Associate Cloud
- Certification level: Foundational
- Certification type: Vendor-specific
Vendor-neutral
1. Certificate of Cloud Security Knowledge (CCSK Certification)
- Provider: Cloud Security Alliance
- Exam pattern:
- No of questions:60
- Allocated time:90 minutes
- Questions types: Multiple choices
- Cost: 345 USD
Preparing for the Certificate of Cloud Security Knowledge (CCSK) exam? Here is the comprehensive preparation guide for Certificate of Cloud Security Knowledge (CCSK) exam.
2. Certified Cloud Security Professional
- Provider: Cloud Security Alliance and (ISC) 2
- Exam pattern:
- No of questions:125
- Allocated time:4 hours
- A passing score is 700 out of 1000 points
- Questions types: Multiple choices
- Cost: 549 USD
3. Certified Cloud Security Specialist (CCSS)
- Provider: Global Science and Technology Forum (GSTF)
- Exam pattern:
Component 1: Written Examination (MCQ)
- No of Questions: 30 Questions
- Allocated time:45 Minutes
- Pattern: Closed Book and multiple choice
- Passing score: 65%
Component 2: Written Examination (MCQ)
- Project Work Component (PWC)
- Individual project
- Allocated time:2 weeks from course completion date
- Passing score: 65%
Cost: Not mentioned by the provider
4. Professional Cloud Security Manager
- Provider: Cloud Credential Council
- Exam pattern:
- No of Questions: 40 Questions
- Allocated time:60 Minutes
- Pattern: Multiple choices
- Cost: 305 USD
5. Certified Integrator Secure Cloud Services
- Provider: EXIN
- Exam pattern:
- No of Questions: 40 Questions
- Allocated time:60 Minutes
- Pattern: Multiple choices
- Cost: Free
Summing Up
To conclude, becoming a cloud practitioner needs your knowledge of the domain as a whole. This includes cloud security as well. Hence, every employer looks for the cloud professional who has the breadth of knowledge on cloud security features and hands-on expertise on implementing them.
Keeping this in mind, Whizlabs as a pioneer of IT certifications training provider has introduced the practice test series for AWS Certified Security Specialty and Certificate of Cloud Security Knowledge (CCSK v.4). These are the two most demanded cloud security examinations in the IT industry, and the combination of the both makes a cloud professional a strong weapon against possible IT threats in a cloud environment.
Hence, join us today and build a valuable future for tomorrow.
Have any query regarding Cloud or its Security? Just write below in the comment section or contact us at Whizlabs Helpdesk and we’ll respond to you in no time.
- Top 20 Questions To Prepare For Certified Kubernetes Administrator Exam - August 16, 2024
- 10 AWS Services to Master for the AWS Developer Associate Exam - August 14, 2024
- Exam Tips for AWS Machine Learning Specialty Certification - August 7, 2024
- Best 15+ AWS Developer Associate hands-on labs in 2024 - July 24, 2024
- Containers vs Virtual Machines: Differences You Should Know - June 24, 2024
- Databricks Launched World’s Most Capable Large Language Model (LLM) - April 26, 2024
- What are the storage options available in Microsoft Azure? - March 14, 2024
- User’s Guide to Getting Started with Google Kubernetes Engine - March 1, 2024



Interesting read!