This blog talks about the AZ-800 Administering Windows Server Hybrid Core Infrastructure exam, which requires an understanding of Azure Role-Based Access Control (RBAC). It is a key area tested in the exam. This will enable you to pass the Microsoft AZ-800 Certification exam as well as enhance your performance at work. Read through to know more about RBAC!
What is Azure Role-Based Access?
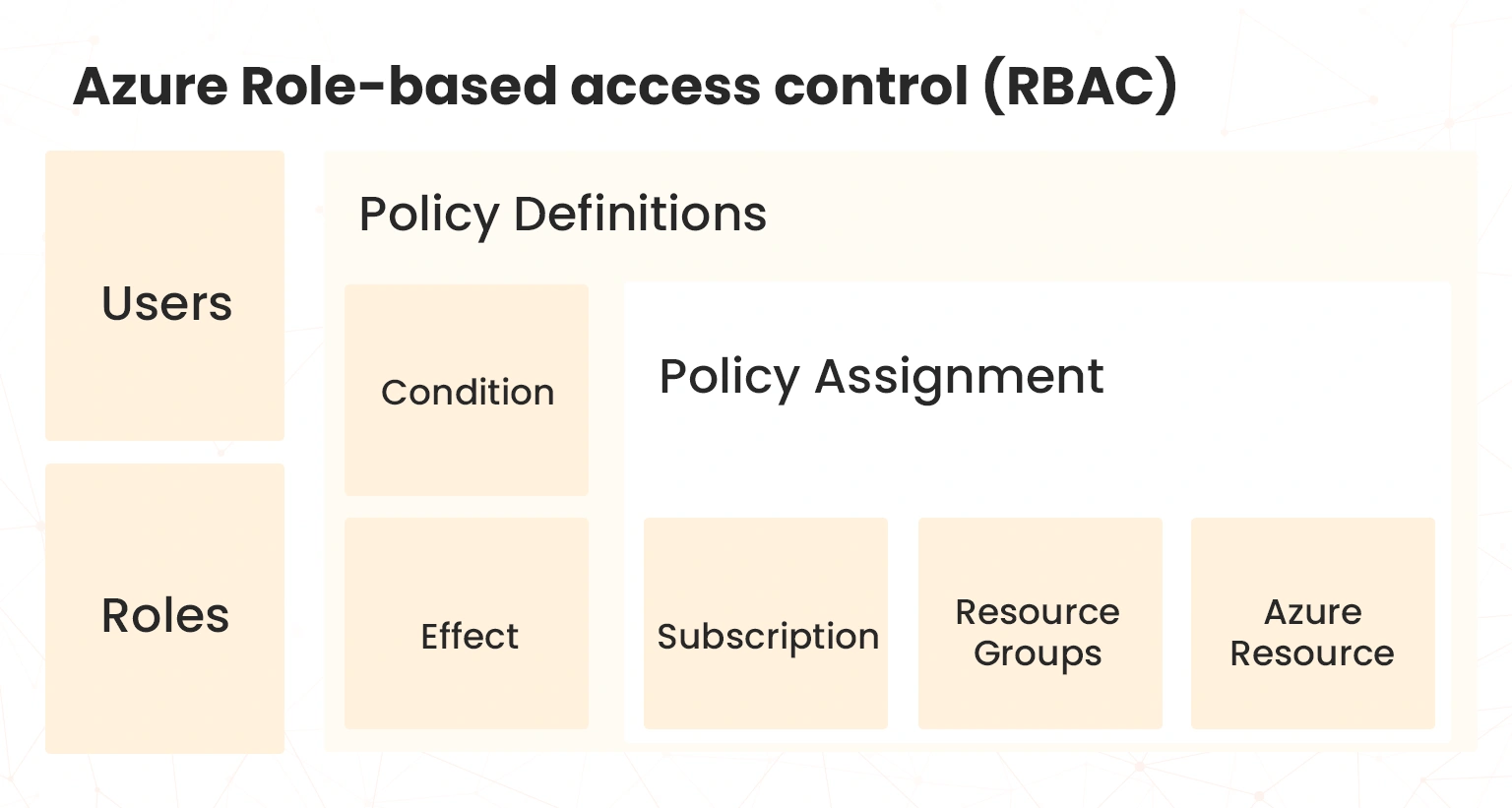
Microsoft Azure provides flexible role-based access control for Azure resources through which administrators can efficiently manage user’s access to Azure resources. This enables you to allow the level of permission and identify user access to a variety of cloud hybrid infrastructure resources. Note also that Azure Role-based access control (RBAC) is a policy-neutral access-control and authorization mechanism defined around roles and privileges, as shown in the diagram below.
As shown in the diagram above, Azure RBAC is built on the Azure Resource Manager feature. It comprises a variety of components, such as role-permissions, user-role, and role-role relationships make it simple to perform user assignments. Its primary function is to help you manage who has access to Azure resources, what they can do with those resources, and what areas they have access to.
Key Concepts of Azure RBAC
The key concepts involved in RBAC include security principal, role definition and scope as discussed in more detail below;
Security Principal
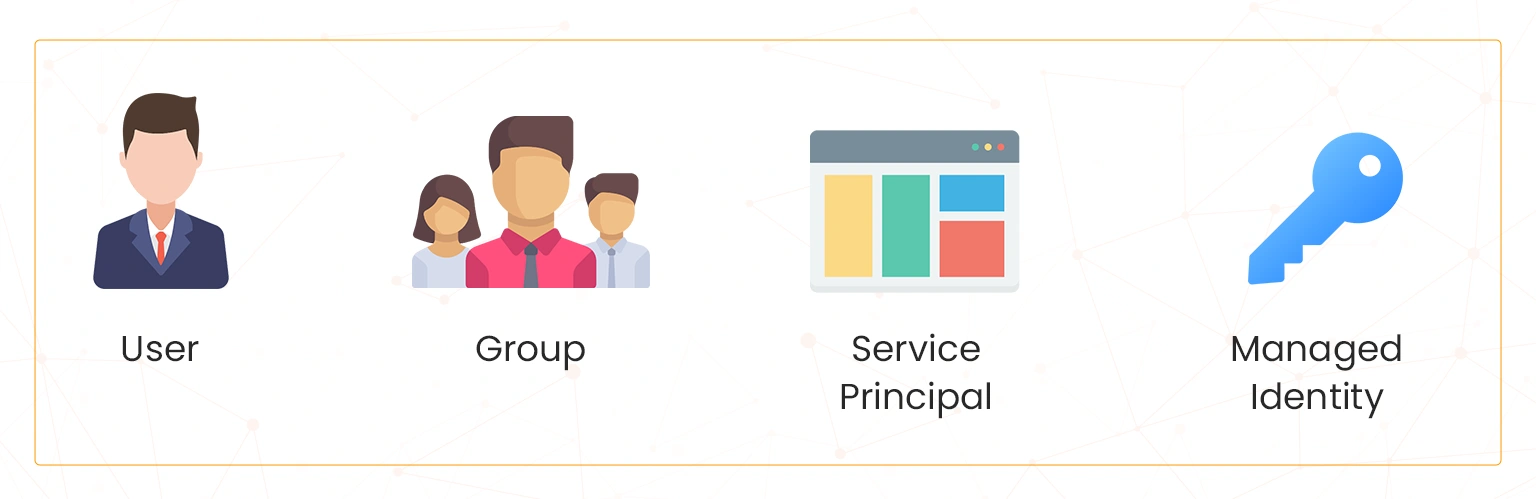
The security principal refers to any object that represents a user, group, service principal, or managed identity requesting access to Azure resources. It is important to note that most organizations using Windows Server Administration often integrate Active Directory and Microsoft Entra ID to enhance their Identity and Access Management (IAM) processes. The components making up the security principles are shown and discussed below;
- User: This refers to an individual who needs access to Azure resources. For example, a developer who requires access to virtual machines for the deployment of applications is a user..
- Group: A group is a collection of users that can be managed as a single entity. For example, a software development team can be grouped together with permissions assigned collectively.
- Service Principal: A service principal is an identity representing an individual or group of individuals that is created for use with applications, hosted services, and automated tools. Its purpose is to enable you to securely access Azure resources such as WebApp or Blob Storage.
- Managed Identity: This refers to an identity managed by Azure that can authenticate to any service that supports Azure AD authentication, requiring no management of credentials. For example, a VM can use a managed identity to access Azure Key Vault.
Role Definition
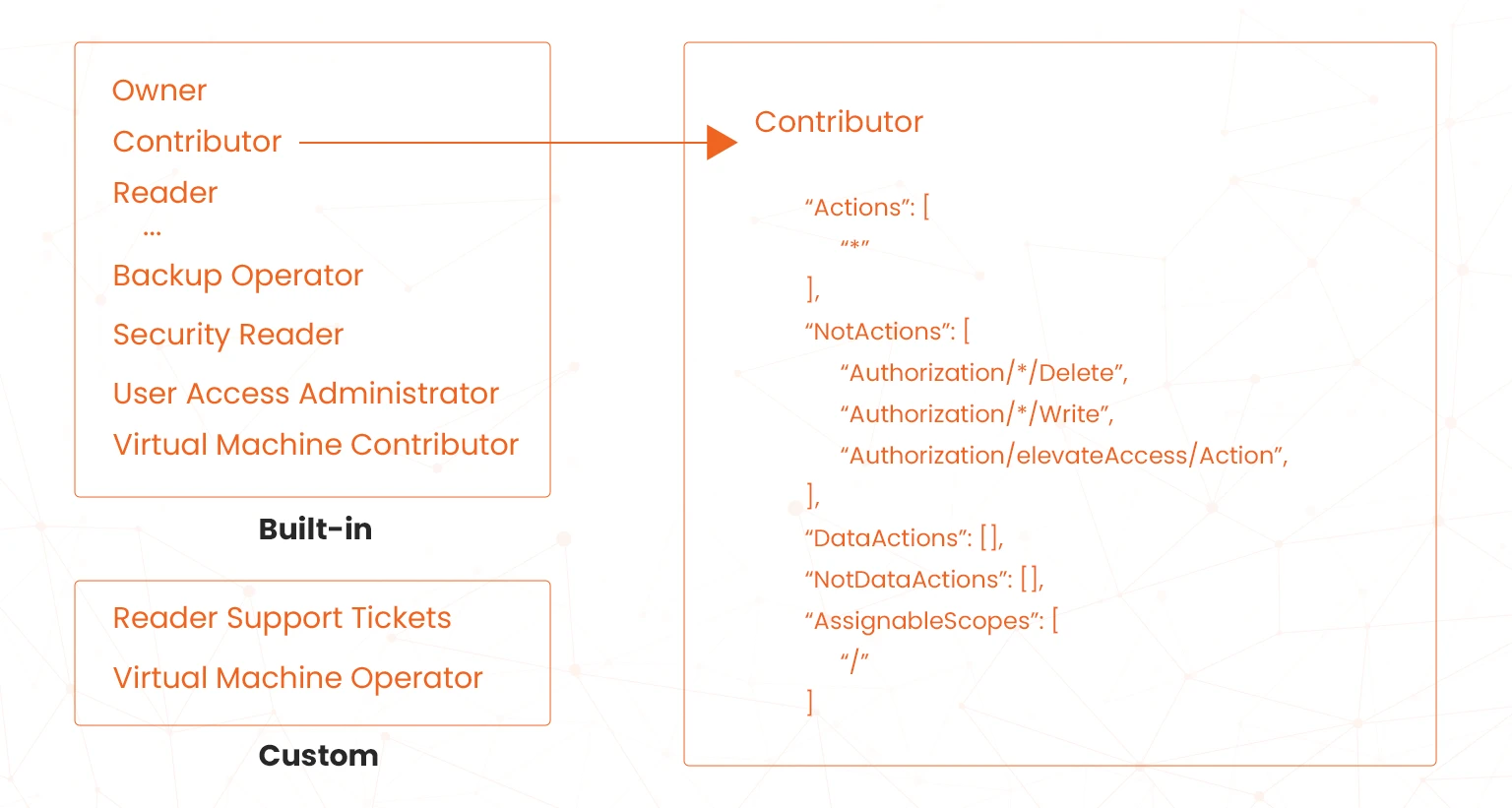
Role definition represents a collection of permissions that can be assigned to security principals. It specifies what actions can be performed on what resources and lists all the operations that can be performed, such as read, write, edit and delete which is crucial for organisations deploying hybrid cloud infrastructure. Also note that roles can be high-level, such as owner, or specific, such as VM reader. You should also be able to make a distinction to be made between built-in roles and custom roles as shown and explained below;
Built-in roles: These are predefined roles in Azure readily available for use, They include the following;
- Owner: The owner has full access to all resources including the right to delegate access to others. For example, the IT administrator managing all resources within a subscription can be assigned the Owner role.
- Contributor: The contributor can create and manage all types of Azure resources but cannot grant access to others. For instance, a developer who needs to deploy applications and manage resources without need to manage access can be assigned the Contributor role.
- Reader: This role can only view existing Azure resources. For example, a project manager who needs to monitor the status of resources without making any changes can be assigned the Reader role.
- User Access Administrator: The user access administrator role has the permissions to manage user access to all types of Azure resources. For example, a project manager who needs to monitor the status of resources without making any changes can be assigned the Reader role.
- Custom roles: Microsoft Azure allows you to create custom roles where the built-in roles do meet your needs in configuring Windows server security. The ideal approach is to create customer roles based on existing roles. This allows you to determine elements you would like to change about the existing role and then make those modifications. Also note that you require the Owner role or the User Access Administrator role within the subscription to create custom roles.
Scope
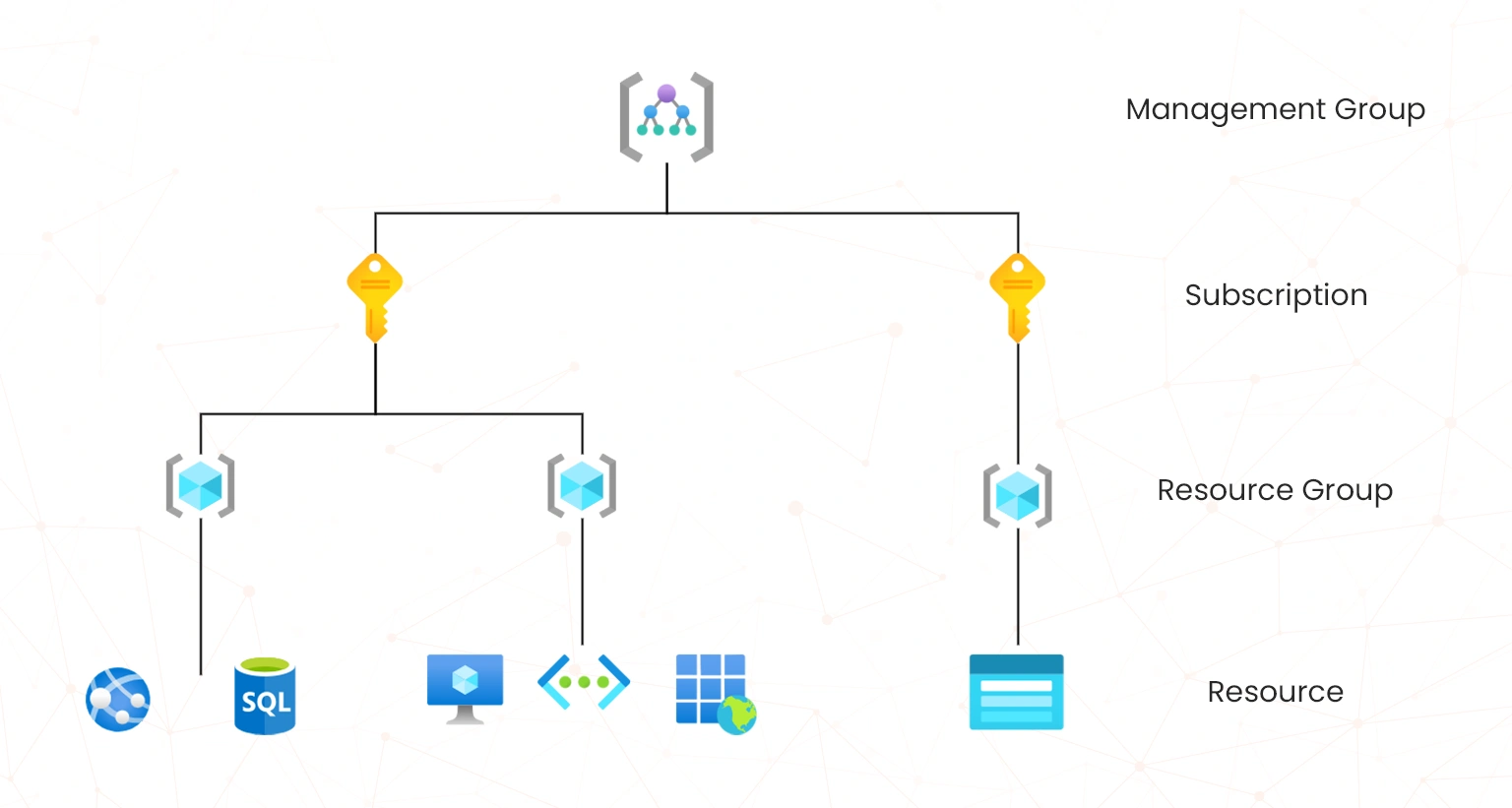
A scope in Azure RBAC represents a set of resources that the access applies to. It defines the boundaries within which permissions are granted and can be at multiple levels which is crucial in managing identity and access in Active Directory Management. This means that if you grant access at a parent scope, those permissions are inherited to the child scopes. For example, if you assign the Reader role to a group at the subscription scope, the members of that group can view every resource group and resource in the subscription. The diagram below shows the Azure RBAC scope;
- Management group: This is a collection of users, groups, and applications that are managed together to make it easier for the administrator to manage access for multiple entities at once. For instance, you can create a managed group for the IT department. You then assign specific roles and permissions to group members.
- Subscription: This is a logical container that is used to provision resources in Azure. It is characterized by specific limits and quotas and its role is to organize and manage resource usage, billing, and access control. For example, you can subscriptions for development and production environments.
- Resource: A resource is a service in Azure that supplies resources. Note that each resource type in Azure is provided by its own resource, for instance, the Storage resource will provide the storage accounts.
- Resource group: This is basically a container that holds related resources for an Azure solution. It allows you to manage and deploy resources together. For instance, you can place all resources for a web application, including VM databases, and storage accounts in a single resource group for better management.
Role Assignments
Role assignments in Azure RBAC consist of binding a security principal to a specific role at a particular scope. This grants specific permissions and determines the actions the security principal can perform on Azure resources within the given scope. The following process should be followed in assigning roles in Windows server environments;
- Determine who needs access: The first step is to determine who needs access. This is represented by the security principal.
- Select the appropriate role: As permissions are grouped into role definitions, you need to select the appropriate role from a list of several built-in roles. If there is no corresponding built-in role, then you will need to create your own custom roles.
- Identify the scope: You can assign roles at any level of scope with each scope determining how widely the role is applied. Also keep in mind that lower levels will inherit role permissions from higher levels.
- Check prerequisites: You need to check the necessary in assigning roles. For example, you must be signed in as a user that is assigned a role that has write permission, such as Role Based Access Control Administrator at the scope level.
- Assign role: Once you have the security principal, role, and scope all in order, you can then proceed to assign a role. You can use a variety of methods to assign roles including using the Azure portal, Azure CLI or REST APIs
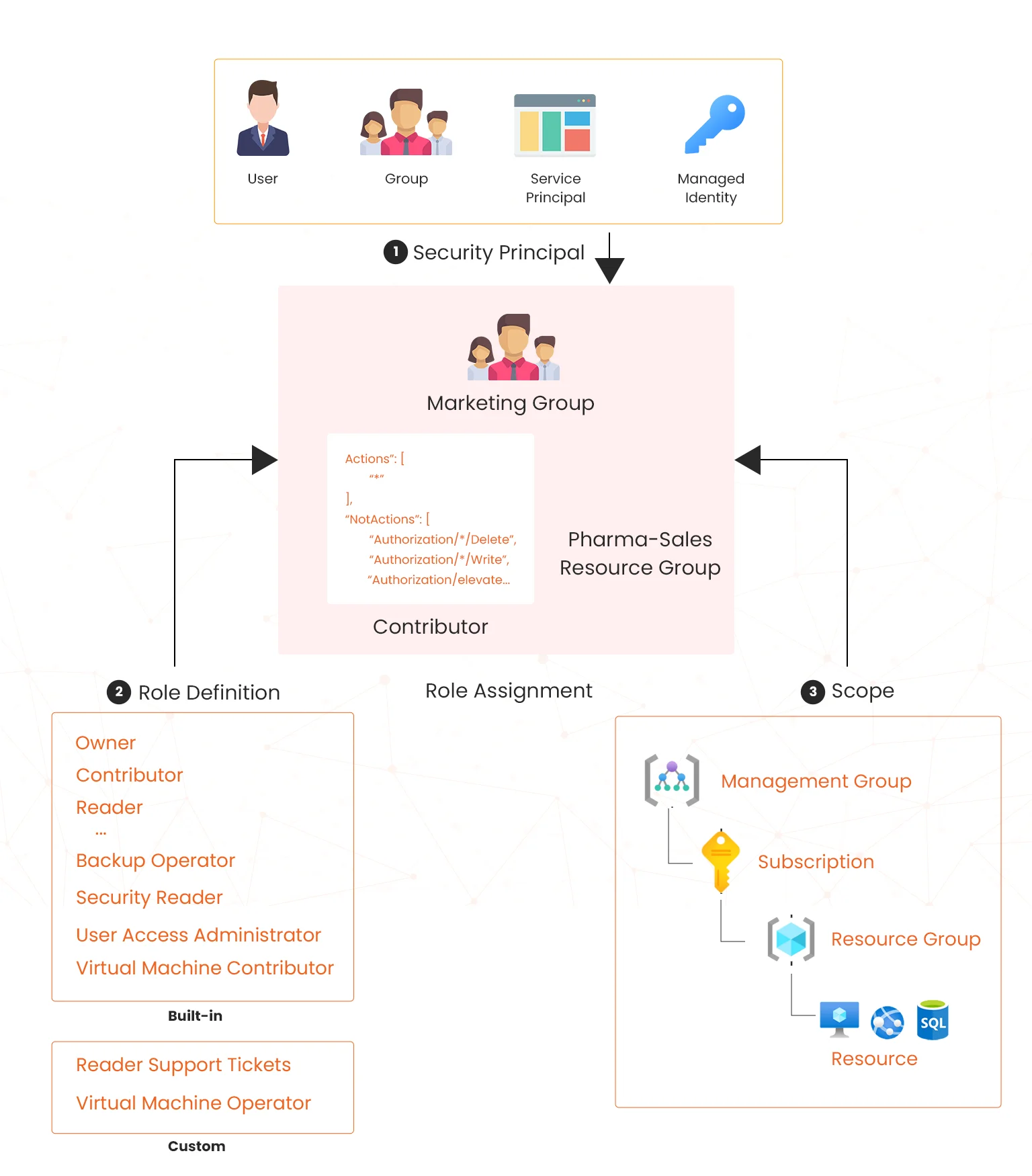
The following diagram shows the process involved in role assignment;
In the diagram above, the Marketing group has been assigned the Contributor role for the pharma-sales resource group. This allows the Marketing group to create or manage any Azure resource in the pharma-sales resource group. Also note that Marketing users will not access resources outside the pharma-sales resource group, unless they are part of another role assignment.
Data Actions
Role-based access controls for control plane actions in Windows server environments are specified in the Actions and NotActions properties as stipulated in role definitions. This allows you to secure sensitive data in Windows server security environments. The following are some data plane actions you can specify in DataActions and NotDataActions:
- Read a list of blobs
- Write a storage blob
- Delete a message in a queue
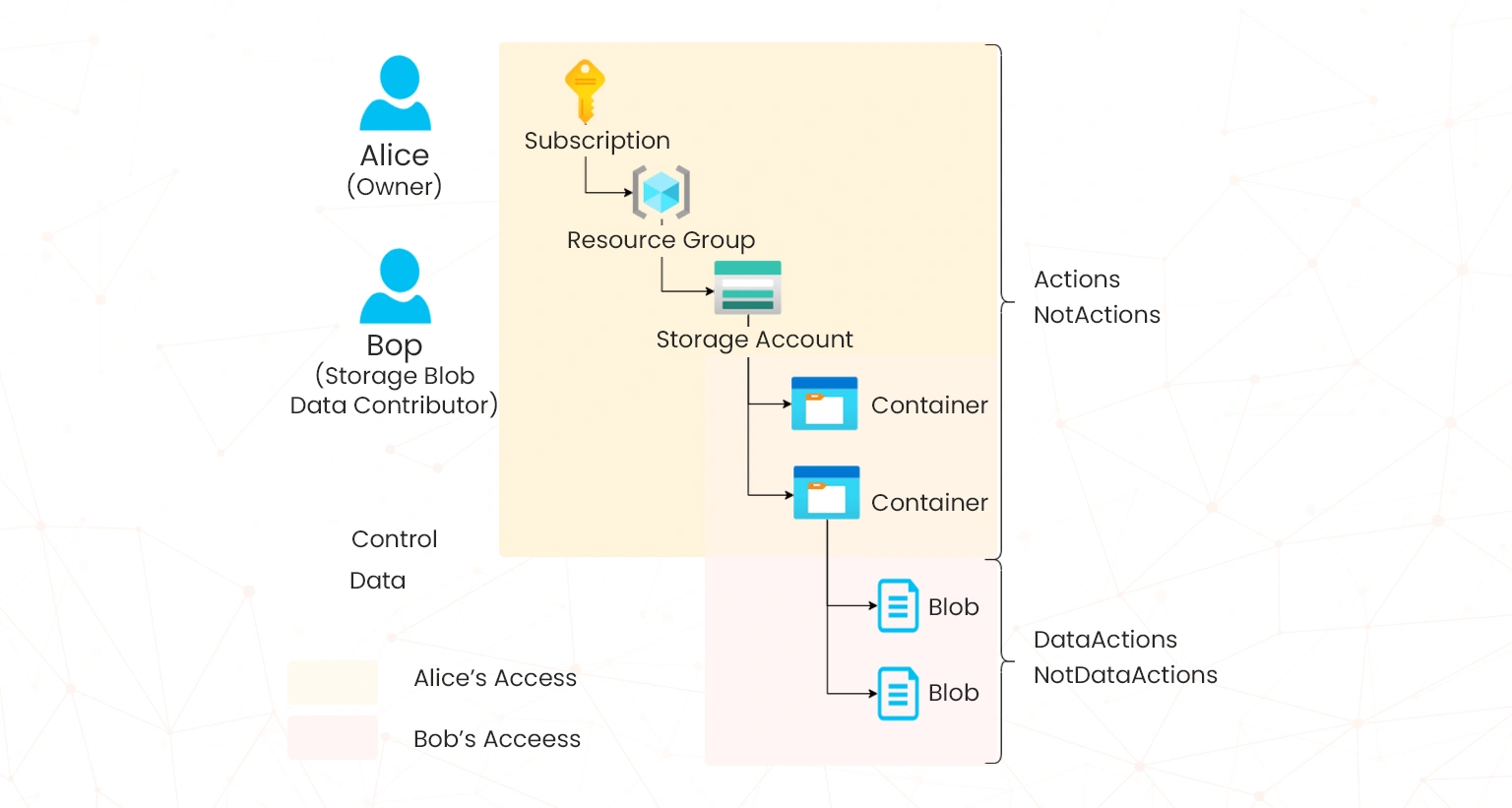
To better understand how data actions work in Azure RBAC, consider the following diagram;
In the diagram above, because Alice is signed the owner role at the subscription scope, she can perform a variety of actions such as creating and deleting resources. However, because Bob is assigned the Storage Blob Data Contributor role at a storage account, he can only perform actions and DataActions related to that storage account.
Benefits of Azure RBAC
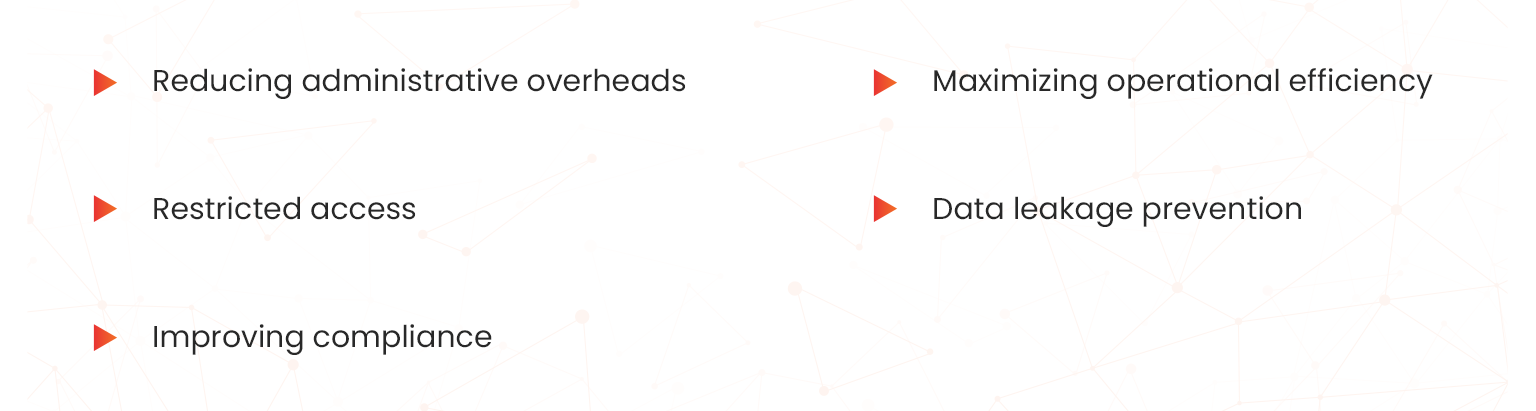
Azure RBAC provides you with many benefits for Windows Server Administration including the following;
- Reducing administrative overheads: Azure RBAC allows a single user to manage virtual machines in a subscription and another user to manage VNs, thus reducing administrative overheads.
- Maximizing operational efficiency: The Azure RBAC functionality allows users to efficiently manage all resources in a resource group, such as virtual machines, websites, and subnets
- Restricted access: Azure RBAC allows you to limit user access to only the authorized level necessary to complete a specific job. This minimizes the impact felt by the organization in case of an attack.
- Data leakage prevention: Another benefit of Azure RBAC is that it helps cloud-first businesses enforce security controls around data leakages. This preserves organizational data in an event of a breach.
- Improving compliance: Using Azure RBAC, you can do the following to strengthen your governance and security control. It provides a consolidated monitoring solution that allows you to have enhanced control over your governance processes.
Best Practices for Azure RBAC Implementation
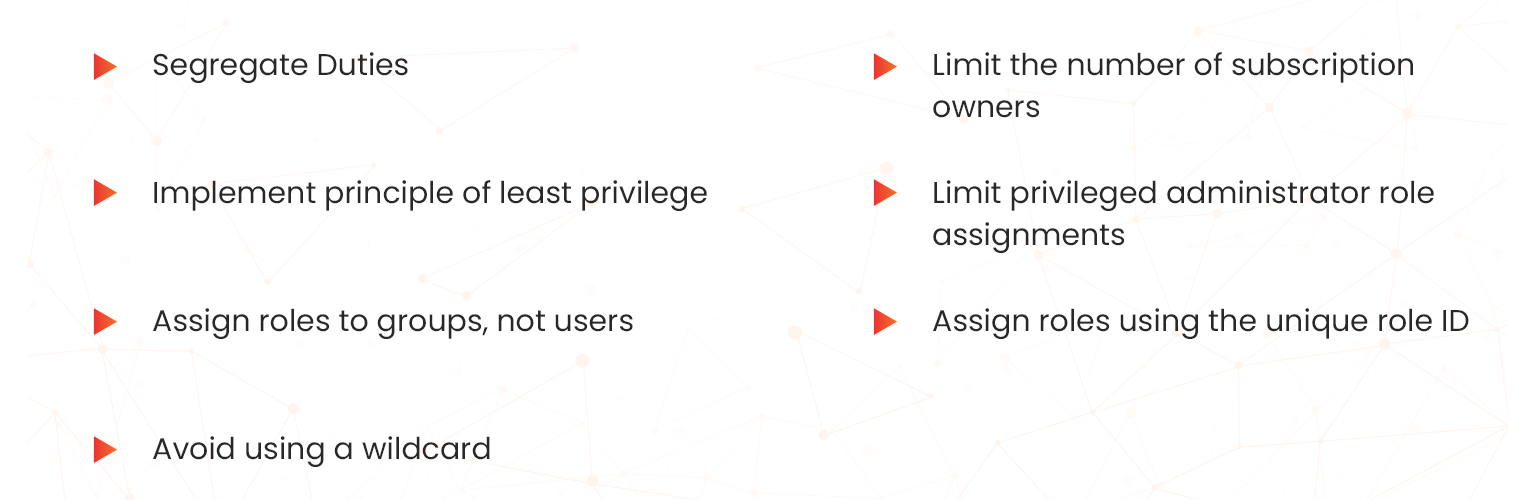
The following best practices implementing Azure RBAC are crucial for organizations that use Windows server administration and operate in hybrid cloud infrastructure environments;
- Segregate duties: Ensure that you use Azure RBAC to segregate duties within your team. This prevents incidences of collusion and other fraudulent activities.
- Limit the number of subscription owners: Best practice is that the maximum should be 3 subscription owners. This is implemented to reduce the potential for breach by a compromised owner.
- Implement principle of least privilege: It is best practice in Azure security to grant users the least privilege to get their work done. This entails avoiding assigning broader roles as they can lead to broader scopes and hence greater attack surface.
- Limit privileged administrator role assignments: Consider removing unnecessary privileged role assignments to reduce the attack surface. Also use a narrow scope, such as resource group or resource, instead of a broader scope, such as a subscription when assigning privileged administrator roles.
- Assign roles to groups, not users: To effectively and securely manage role assignments, avoid assigning roles directly to users. Instead, assign roles to groups as this minimizes the number of role assignments.
- Assign roles using the unique role ID: Ensure that you assign roles using unique IDs not role names. This maintains the security of the cloud environment in cases where you need to rename your roles.
- Avoid using a wildcard: Wildcards should not be used when creating custom roles as they can lead to the granting of excessive access. You should instead specify Actions and DataActions explicitly instead of using the wildcard (*) character.
Conclusion
This blog gives you the perspective of a candidate for the AZ 800 Administering the Windows Server Hybrid Core Infrastructure exam, you deploy, package, secure, and configure Windows Server workloads using on-premises, hybrid, and cloud technologies. You, therefore, need a solid understanding of the operations of Azure RBAC, such as in Active Directory Management and Azure hybrid services, as explained in this blog. This allows you to ensure that the creation of roles is as secure as possible while adhering to IAM requirements, you can experiment the above through our hands-on labs! Talk to our experts in case of queries!
- How to Use GitHub Copilot Like a Pro 2025 Guide - July 28, 2025
- AZ-104 Networking Concepts Explained for Beginners - July 4, 2025
- How do you configure Azure Site Recovery for AZ-800? - May 16, 2025
- How Does AZ-140 Help in Managing Azure Virtual Desktops? - March 7, 2025
- What Are AZ-800 Key Concepts for Role-Based Access? - February 18, 2025
- Simplifying Azure Dev Workflows with the Azure Developer CLI - February 7, 2025
- MD-102:Endpoint Administrator – Syllabus Update Sept 17, 2024 - September 24, 2024
- How I Successfully Passed the AI-900 Certification Exam - September 4, 2024