Hope your AWS CSAA exam preparation is going well. To help you with your preparation, here we bring another topic – AWS Key Management Service. This topic comes under “Specify Secure Applications and Architectures” domain of the exam. While preparing for the AWS Certified Solutions Architect Associate exam you need to know an overview of AWS KMS.
So, here in this article, we’ll cover an introduction to the AWS Key Management Service.
Try Now: AWS Certified Solutions Architect Associate Free Test
What is the AWS Key Management Service?
AWS KMS is a managed service that is integrated with various other AWS Services. You can use it in your applications to create, store and control encryption keys to encrypt your data. KMS allows you to gain more control for access to the data that you encrypt. KMS assures 99.99999999999% durability of the keys.
It also provides high availability as keys are stored in multiple AZ’s within a region. KMS is integrated with the CloudTrail. You can audit, for what purpose, by whom and when the key was used which helps to meet compliance and regulatory needs.
Some Noteworthy points you should know about AWS Key Management Service:
- Even though KMS is a global service but keys are regional that means you can’t send keys outside the region in which they are created.
- How does AWS KMS protect the confidentiality and integrity of your keys? KMS uses FIPS 140-2 validated HSMs (Hardware Security Modules).
- Whether you are writing your own application or using other AWS services, you can control who can access your master keys and gain access to your data.
- When you are importing keys in KMS make sure to maintain a copy of those keys so that you can re-import them anytime.
How does AWS KMS Encrypt Your Data?
Well, actually it doesn’t. The primary resource of KMS is customer master key (CMK) which can encrypt or decrypt data up to 4096 bytes. We generally have a lot of data be it S3, EBS, RDS etc. So, we can’t use CMK’s for that. Therefore, we use KMS CMK keys to generate, encrypt and decrypt data keys which are used outside of KMS to encrypt large amounts of data. It is these data keys created by CMK’s that do the encryption/decryption.
You can create, use or manage the CMK’s through AWS KMS. They never leave AWS KMS FIPS validated hardware security modules. This is different for data keys as AWS KMS does not store or manage or perform any kind of cryptographic operation with your data keys. You must use them outside of AWS KMS. You can use OpenSSL or other cryptographic libraries like AWS Encryption SDK for that.
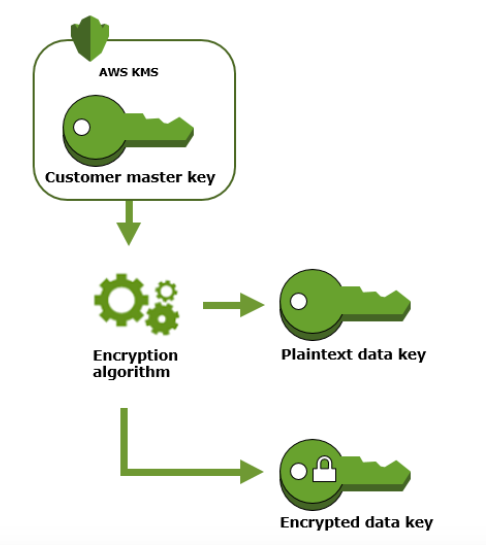
To create a data key call GenerateData key operation. AWS KMS then uses the specified CMK to generate data keys. As you can see from the below figure it generates one plaintext data key and an encrypted data key.
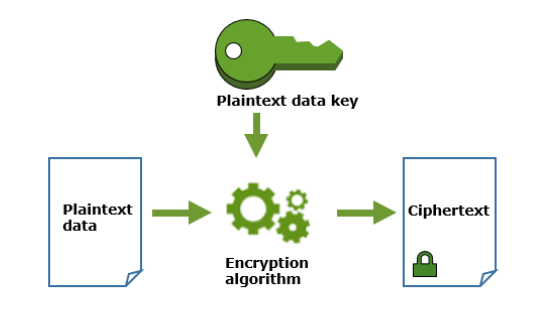
This plaintext data key is used to encrypt the data, then the plaintext key is removed ASAP from the memory so that data doesn’t get compromised. The encrypted key is stored along with the encrypted data to use it during decryption.
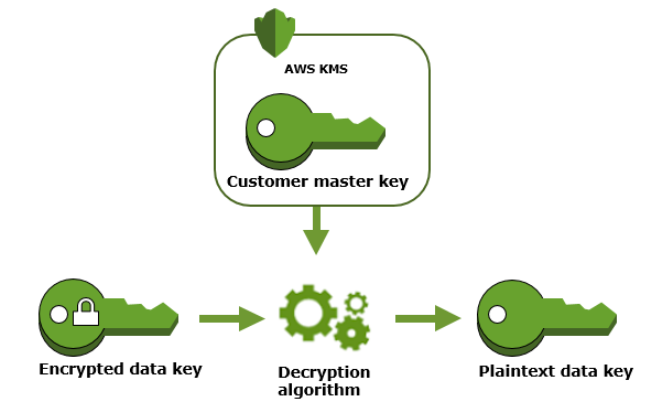
Now the encryption part is done, for decryption you need to use decrypt operation. AWS KMS uses the customer master key to decrypt the encrypted data key stored along with the data. It returns the plaintext key which is then used to decrypt the data again this plaintext key is removed from the memory.
The following diagram depicts this:
Image Courtesy: https://docs.aws.amazon.com/kms/latest/developerguide/concepts.html
AWS Managed CMK’s vs Customer Managed CMK’s
When you want an AWS service to encrypt data on your behalf you can specify CMK that you would like to use to generate, encrypt or decrypt data keys. These are customer managed CMK’s. Basically, you have full control over them like you can enable/disable/rotate master keys, create IAM policies to restrict who can access the keys, grant permissions for other accounts and services to use these keys.
If you don’t specify a CMK and you are trying to create an encrypted resource for the first time within that service then that AWS Service will create an AWS managed CMK. In that case, the access control and key policies are managed by AWS itself. Even though you don’t have any direct control over the keys you can still track AWS managed keys and usage of keys in CloudTrail.
Note: AWS Machine Learning certification is one of the best among AWS certifications for machine learning professionals. Learn about AWS ML and get ahead towards the certification preparation with the AWS Certified Machine Learning Speciality free test.
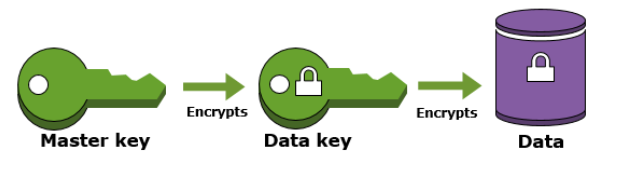
Envelope Encryption
As discussed above CMK’s can be used to generate, encrypt or decrypt data keys. Envelope encryption includes encrypting the data with plaintext data key then encrypting the plaintext data with another key which is a customer master key (CMK).
Final Words
Key Management Service (KMS) along with Server-side Encryption in S3 is one of the most important topics for CSAA certification exam. In case you want to understand how KMS integrates with S3 please refer to our previous blog on S3 Server-Side Encryption. Hope this article has helped you in your AWS CSAA exam preparation and also it is beneficial for pursuing AWS Certified Developer Associate Certification
You can also take the Whizlabs AWS CSAA Online Course to prepare for the AWS Certified Solutions Architect Associate exam. Also, you can take AWS CSAA Practice tests to check your current level of preparation. After that, we also avails AWS Professional courses under AWS Solution Architect in order to expand your career. So, join us today and prepare yourself to pass the AWS Certified Solutions Architect Associate (AWS CSAA) exam. For more help we also provide complete guide of AWS Solution Architect Associate certification.
Have any query regarding AWS KMS? Just write in the comment section below and we’ll be happy to respond. You can also raise your query in Whizlabs Forum to get it resolved by the industry experts.
- Cloud DNS – A Complete Guide - December 15, 2021
- Google Compute Engine: Features and Advantages - December 14, 2021
- What is Cloud Run? - December 13, 2021
- What is Cloud Load Balancing? A Complete Guide - December 9, 2021
- What is a BigTable? - December 8, 2021
- Docker Image creation – Everything You Should Know! - November 25, 2021
- What is BigQuery? - November 19, 2021
- Docker Architecture in Detail - October 6, 2021



Great Article Akshay ??
Durability of Keys are 99.999999999%
Excellent!! Best description of KMS, CMK, DK on the WWW!