We have launched AWS Certified Solutions Architect Associate certification exam which is the basic level of AWS certifications. As part of training AWS certification topics, we have started writing important topics that are useful for preparing for the aws certification exams. In this articles, we are writing about Ingress vs Egress, these topics are part of the security in Amazon Web Services (AWS). Here is the snapshot of the exam blueprint.
What are AWS Security groups?
In AWS, there is a security layer which can be applied to EC2 instances which are known as security groups. Security groups comprise of rules which allow traffic to and from the EC2 instances. These rules are divided into the below 2 categories
- Inbound Rules – These rules are used to control the inbound traffic or also known as ingress
- Outbound Rules – These rules are used to control the outbound traffic or also known as egress
Why AWS provide Security groups?
These rules are provided by AWS to have an additional security barrier which protects your EC2 instances. It’s like a firewall that can be used to protect a set of EC2 instances.
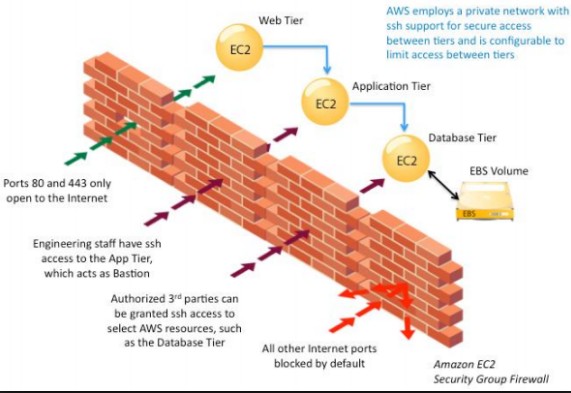
The below diagram from AWS documentation shows a classic example of why you would need Security Groups. Let’s go through each bit of the image below in a little more detail.
- The web tier – Normally companies would host a web layer which are EC2 web servers that can be exposed to the internet. Now when such servers are exposed to the internet, it can be very easy for a hacker to break into these servers. This is where you would need to lock down all the ports on the server except for port 80 for HTTP traffic and port 443 for HTTPS traffic. This can be achieved with the help of security groups. These security groups can be assigned to a set of EC2 instances and the rules will be applied to all of the servers. This ensures that you don’t need to manually do the same settings on all the servers one by one.
- The application tier – Ideally the application tier will not be able be accessed in the internet and can only be controlled by the IT admin staff. In such a case you would have an intermediate host known as the bastion host to have access to the EC2 application servers. So in this case you would create security groups in which only the bastion host would have access to the application servers.
- Database Tier – Again this tier would only be accessible by IT support staff via SSH or by the web and application tier. So in this case you would ensure that the security groups would only allow traffic from the web and application tier in addition to the SSH protocol from the IT support staff. And then finally all other traffic would be blocked by default from the internet.
How do we create/set Security groups?
Now let’s look in detail and the steps required to create security groups.
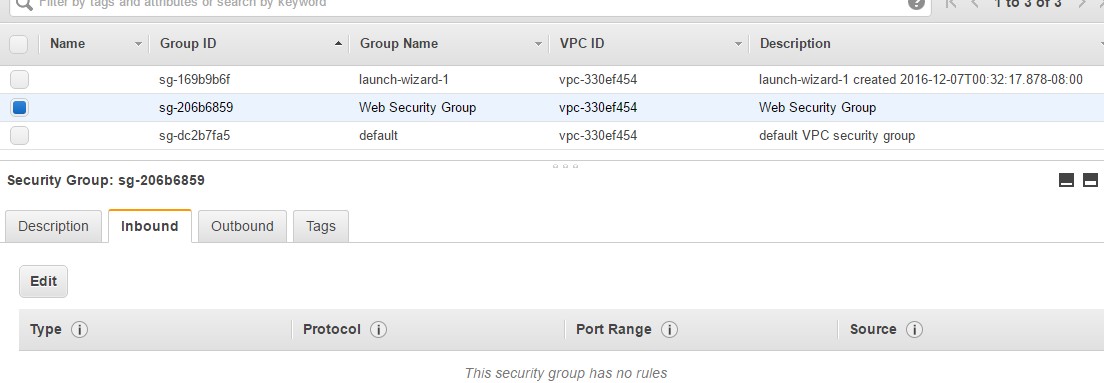
Step 1 : Log into your AWS Console and go to the EC2 dashboard. Go to Network & Security->Security Groups.
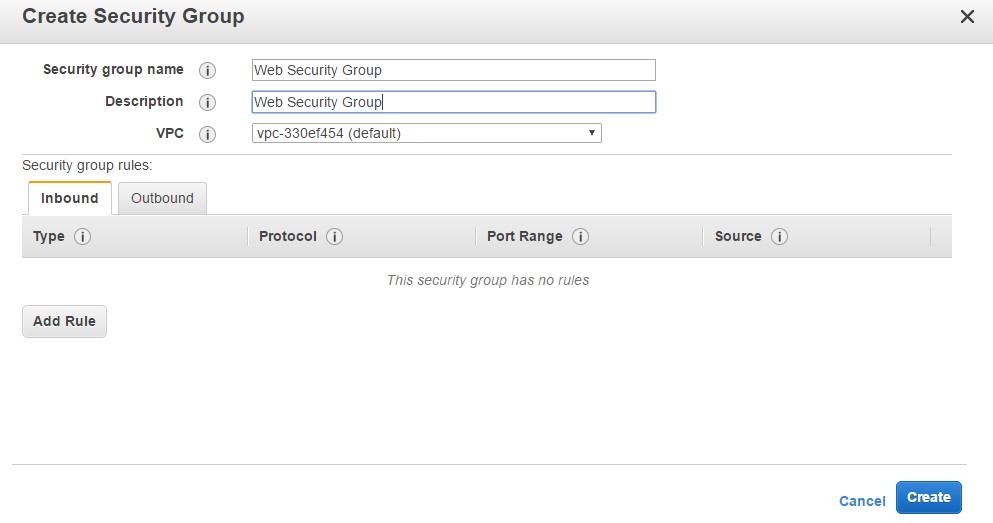
Step 2: Click on Create Security Group. Let’s create a Web Security Group. This Security group will be for all Web servers in our AWS account.
Click on Create to create the Security Group.
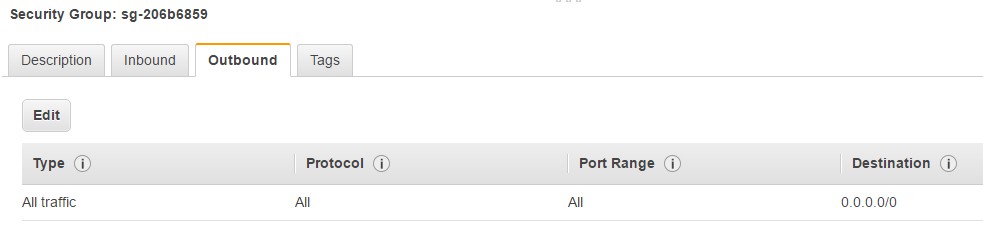
Now by default, because you have not mentioned any Rules, this Security Group will be based on the following principles
- No Inbound Rules – This means that if this Security Group is attached to any instance, no traffic would be allowed into that instance. This is because by default for Inbound Rules is DENY and hence all access to the server will be denied.
- Outbound Rules – But in retrospect, if you look at the Outbound Rules, you can see that all traffic by default is allowed and this is ok.
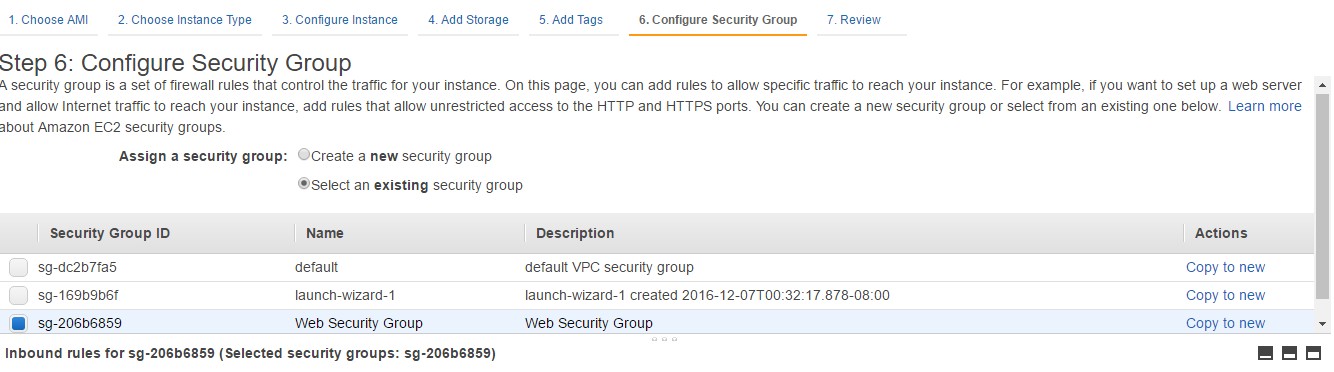
Step 3: Now let’s assign this Security group to an EC2 instance. So when you create an EC2 instance, when you reach the “Configure Security Group” screen, you need to select the option of “Select an existing Security Group” and choose the Web Security Group which was created earlier.
An Example configuration for our Security Group
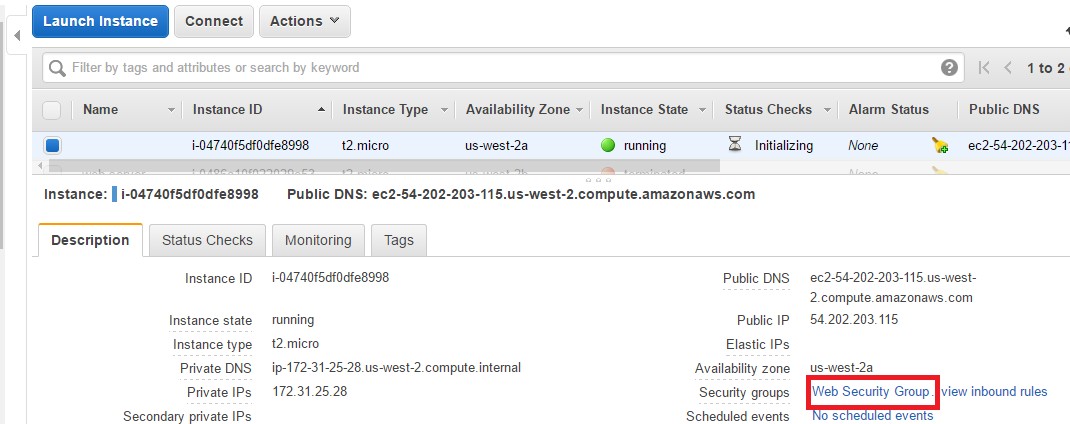
Now that we have an instance setup and a Security group assigned to the instance, let’s see an example of an Inbound Security Group.
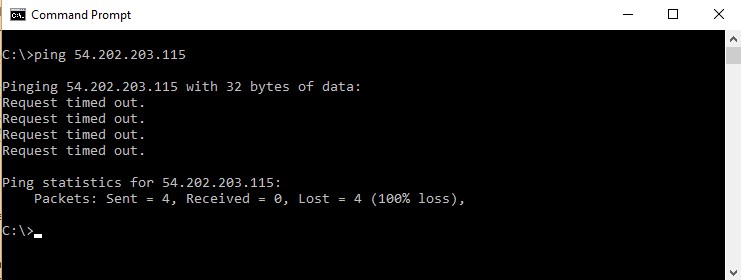
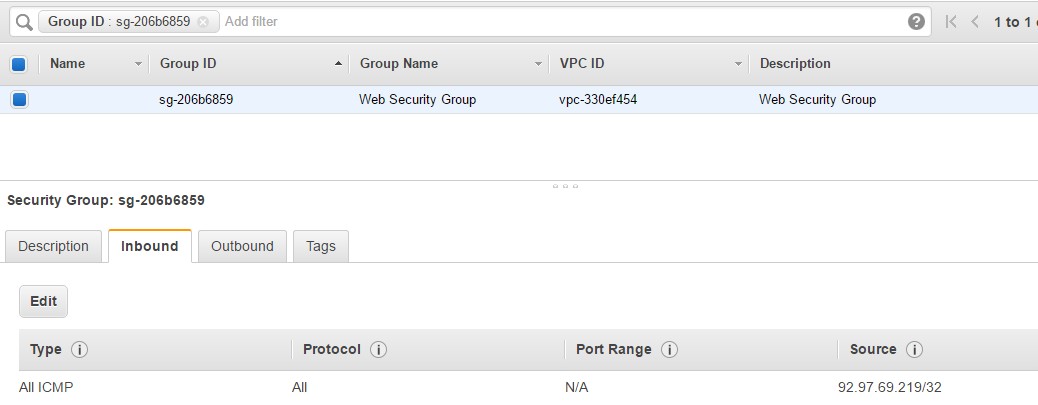
Step 1: Go to your EC2 dashboard, go to the instance which was created and click on Web Security Groups. Also please note that this instance has a public IP of 54.202.203.115
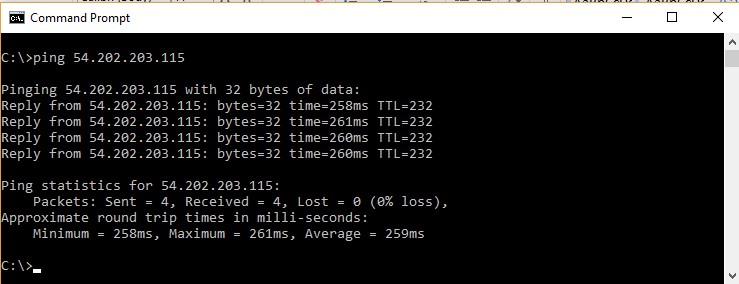
Now let’s try to ping our server on the Public IP. As shown below, we can see that the request is getting timed out. This is because all incoming traffic is blocked for the PING command.
Step 2: So now let’s edit our Web security groups to allow traffic to our Web server. Go to the Security Group and click on the Edit button.
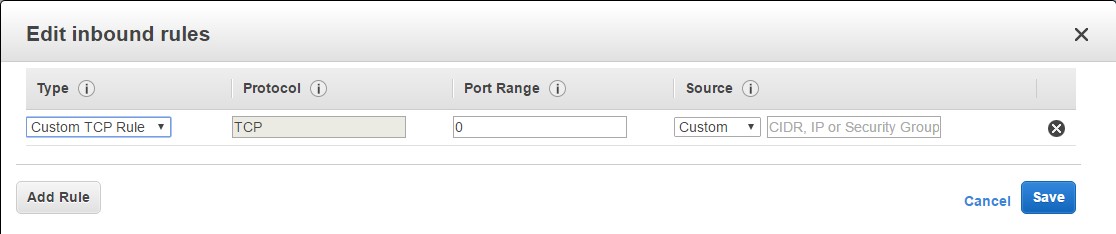
Step 3: Now when you create an Inbound Rule, You need to mention the below parameters
- Type – This is the type of rule you want to configure. Here you have custom rules, such as rules for HTTP, SSH, HTTPS etc.
- Next is the protocol which gets set when you choose the Type.
- Next is the port range for which you want to allow the protocol. So for example if you want to allow http web traffic, you need to allow the Port Range of 80.
- Next is the Source Address. Here you have the further Options to allowing the traffic from any IP, or a range of IP or from your IP Address.
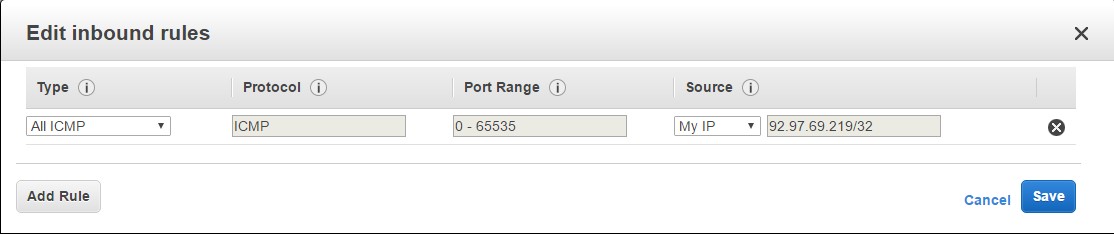
So let’s choose the following parameters for allowing us to ping the server. So there is an option to choose the Type of “All ICMP”. ICMP is the protocol used by the ping command.
We are then choosing the Source as “My IP”. So AWS will automatically detect your IP address and populate it accordingly. You can then click on the Save button to save the rule.
So now you have the Rule defined.
Step 4: Now let’s try to ping our server again. And now you can see that you can successfully ping the server as shown below. This means that the security group has taken effect and is working properly.
Common Rules for the Web Security group
So let’s see some common Security Rules that we can use for our Web server.
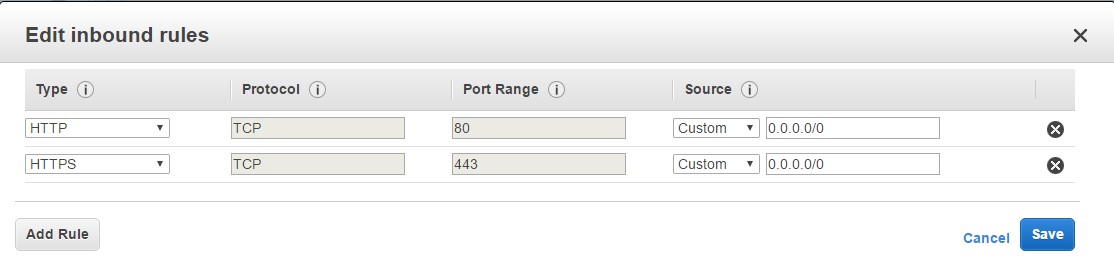
Rule 1: Allowing http and https traffic – You can actually create multiple Rules in the Security group. One common and most required one is to allow traffic for the HTTP and HTTPS ports to allow the web sites hosted on your Web server to be accessed from anywhere.
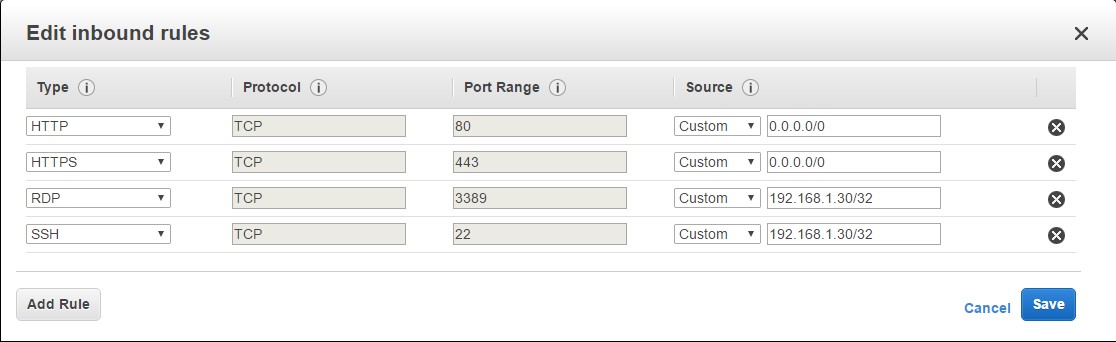
Rule 2: Allow SSH or Remote Desktop, only from a single IP – Sometimes you may want to Remote Desktop or SSH to the web server depending on whether it’s a Windows or Linux Server to do configuration changes to the server. In such a case, you should only allow these protocols from a certain IP. So in the below example, we are assuming that 192.168.1.30 is a bastion host or dedicated machine on your network. It is a security risk to allow this sort of access from any other IP. When you specify a single IPv4 address, use the /32 prefix at the end of the IP Address.
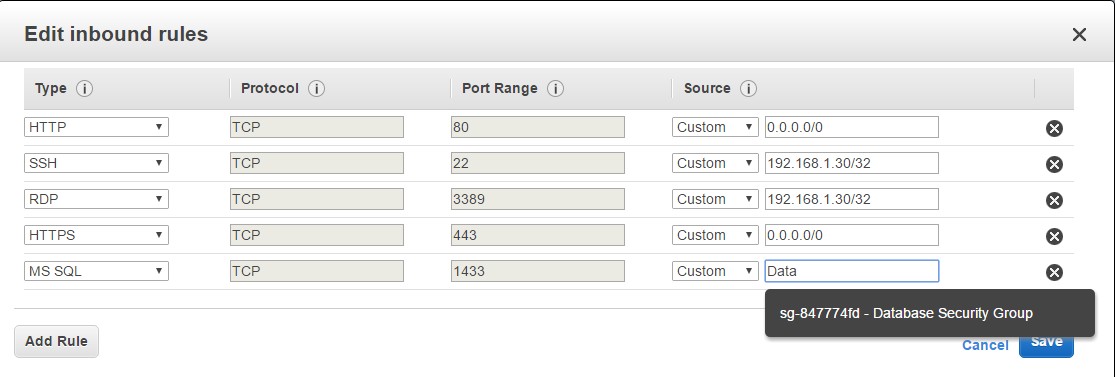
Rule 3: Allowing Access from Database – Normally when you host databases in other EC2 instances you will have separate Security groups for them. Let’s assume you create a Database Security group for these sort of instances. You can then create inbound rules for the Web Security Group to the database security group so that the web servers can talk to the database servers. So in the below screenshot, we are assuming that we have MS SQL server, so we are choosing this rule type. And we are assuming that a Database security group is in place. So when you start typing the ‘Source’ as Database, it will auto populate this section with the Database Security Group.
Final Points to Remember about Security Groups
These are the most important points to remember for the AWS certification exam.
- Security groups are stateful — if you send a request from your instance, the response traffic for that request is allowed to flow in regardless of inbound security group rules. Responses to allowed inbound traffic are allowed to flow out, regardless of outbound rules.
- There are the following service limitations in AWS
- You can create up to 500 security groups per VPC
- You can add up to 50 rules to a security group.
Summary
I hope this article is very useful for you to understand the concepts behind security groups in the Amazon Web Services (AWS). Note that security is one of the important concepts that has to be prepared very well for passing the exam. We are going to write series of articles on the similar topics to teach you on how to use AWS with respect to prepare for the AWS certification exams.
Practice Questions
It is important to practice more number of questions for preparing for the solutions architect certification exam. We have prepared 300+ high quality questions that covers all the exam objectives and provides explanation for all the option given for the question. This would help you to improve our confidence on the exam before you are taking the real exam.
- 300+ Practice Questions for Solutions Architect Associate Exam
- How to prepare for solutions architect associate exam?
Technical Support
If you are looking for any technical support like more explanation on each questions or clarifications, we have a dedicated support for Amazon Web Services (AWS) to answer all your queries. You can drop us a mail at info@whizlabs.com with your queries. We would respond to your questions within 12 hours of time.
Good luck for your exam preparation!!
- Top 20 Questions To Prepare For Certified Kubernetes Administrator Exam - August 16, 2024
- 10 AWS Services to Master for the AWS Developer Associate Exam - August 14, 2024
- Exam Tips for AWS Machine Learning Specialty Certification - August 7, 2024
- Best 15+ AWS Developer Associate hands-on labs in 2024 - July 24, 2024
- Containers vs Virtual Machines: Differences You Should Know - June 24, 2024
- Databricks Launched World’s Most Capable Large Language Model (LLM) - April 26, 2024
- What are the storage options available in Microsoft Azure? - March 14, 2024
- User’s Guide to Getting Started with Google Kubernetes Engine - March 1, 2024


Thanks for this very infomative article.
Hi, I’ve been reading a bit on aws docs and white papers and bumped into a question on ingress and egress rules when I read this article.
You have set the database rule at ingress on your web server, but on your web server ports you be using one high port (1024-65355) as source port and 1433 as destination port to connect on database server.
Maybe you should set this rule on your database security group, so the source port will be 1433 from the web ic2 instances and the outbound port will be accept by default because of the sg state full characteristic.
You are exactly right @Witalo Andrade
You are exactly right @Witalo Andrade
Obviously the individual who wrote this article does not come from a security background. Allowing 0.0.0.0/0 port any as an egress rule is a huge security vulnerability. Controlling egress is at least as important in fighting cyber crime as controlling ingress.