Amazon GuardDuty is a fully managed threat detection service to monitors any malicious or unauthorized behavior to ensure the security of your AWS accounts and workloads.
As an AWS Certified Cloud Practitioner, it is crucial to ensure the security of the AWS infrastructure and you can achieve it with the help of Amazon GuardDuty.
In this blog, we are going to explore Amazon GuardDuty and its features, the working of Amazon Guardduty, and how to achieve intelligent Threat Detection using Amazon GuardDuty.
Let’s dive in!
What is AWS GuardDuty?
Amazon GuardDuty is a threat monitoring service that keeps an eye out for illegal activity and harmful activities to safeguard workloads, and data stored in Amazon S3, and AWS accounts.
As soon as an IT or security administrator activates GuardDuty through the AWS Management Console, the controlled cloud-hosted service starts scanning the AWS environment.
Although there is a 30-day free trial when you enable GuardDuty, the service is not free. Pricing is determined by the quantity of VPC Flow Log and DNS Log data evaluated monthly as well as the number of AWS CloudTrail events examined.
AWS GuardDuty Features
Accuracy
Amazon GuardDuty ensures effective threat detection for the accounts that are subjected to theft using continuous monitoring in real-time.
GuardDuty finds the activity of the accounts comprised such as resources accessed from uncommon locations at unexpected times.
Continuous monitoring
Amazon GuardDuty continuously monitors and assesses data from AWS CloudTrail, VPC Flow Logs, and DNS Logs in AWS accounts and workloads. It allows for aggregated threat detection by linking AWS accounts, eliminating the need for a per-account approach. Moreover, there is no requirement to manually collect, analyze, or correlate extensive amounts of AWS data from numerous accounts.
Threat severity levels
Amazon GuardDuty employs three severity categories to help clients prioritize their response to potential attacks.
- A “Low” sensitivity indication signifies the detection and prevention of suspicious or malicious activity to safeguard your resources.
- A “Medium” risk level indicates questionable behavior, such as a notable volume of traffic sent through the Tor network or unusual activity.
- A resource assigned a “High” severity rating indicates that it has been compromised and is actively being exploited for malicious purposes, such as an Amazon EC2 instance or a set of IAM user credentials.
High available threat detection
Amazon GuardDuty is crafted to autonomously oversee the utilization of resources within your AWS accounts, workloads, and Amazon S3 data. It enhances detection capabilities precisely when needed and reduces usage during periods when it is no longer necessary.
One-click deployment
Configuring Amazon GuardDuty is a seamless process, requiring just one click or API request for a single AWS account. With a few extra steps, you can easily enable GuardDuty across multiple accounts using the AWS Management Console. Additionally, GuardDuty provides native support for handling multiple accounts and offers integration with AWS Organizations.
How to turn on intelligent Threat Detection using Amazon GuardDuty
In these guided hands-on labs, you will learn how to enable Amazon Guardduty and explore some threat detection functionalities.
To start with it, you have to access the Whizlabs hands-on labs page. Then type Amazon Guardduty in the search box and the lab page will be displayed.
Follow the instructions given under lab steps.
Task 1: Sign in to the AWS Management Console
Click the “Open Console” button, and you will be directed to the AWS Console in a new browser tab. On the AWS sign-in page, keep the Account ID as the default setting. It is crucial not to modify or remove the 12-digit Account ID displayed in the AWS Console; failure to do so may hinder your progress in the lab.
Proceed by copying your User Name and Password from the Lab Console to the IAM Username and Password fields in the AWS Console. Click the “Sign in” button to complete the sign-in process.
Once successfully signed in to the AWS Management Console, set the default AWS Region to US East (N. Virginia) by choosing us-east-1.
Note: There is no validation function for this lab.
Task 2: Enabling Amazon GuardDuty
Ensure you select the US East (N. Virginia) region (us-east-1) from the AWS Management Console dashboard, located in the top right corner.
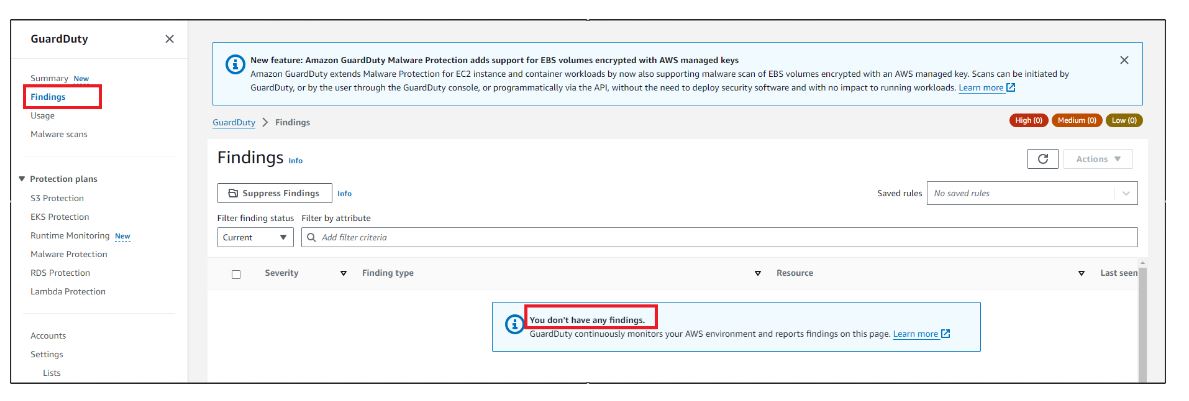
Navigate to the Services menu at the top, then click on GuardDuty under the Security, Identity, and Compliance section. Proceed by clicking on “Get started.”
Click on Enable GuardDuty with one click and this service will be activated.
In the Findings page, you will see the warning You don’t have any findings because there is no malicious activity happening in your AWS Account. Ignore the warnings, wherever you find them.
Task 3: Exploring Amazon GuardDuty
Settings
Navigate to the left panel and click on “Settings.” You will find a Detector ID, which represents the GuardDuty service as a resource.
For service roles, GuardDuty utilizes a service role to oversee your data sources on your behalf.
Concerning findings export options, findings are automatically sent to CloudWatch Events, and there’s the additional option to export them to an S3 bucket. The export process for new findings takes place within 5 minutes, and no adjustments are necessary.
If you choose to suspend GuardDuty, it ceases monitoring your AWS environment, preventing the generation of new findings. Existing findings are preserved and remain unaffected.
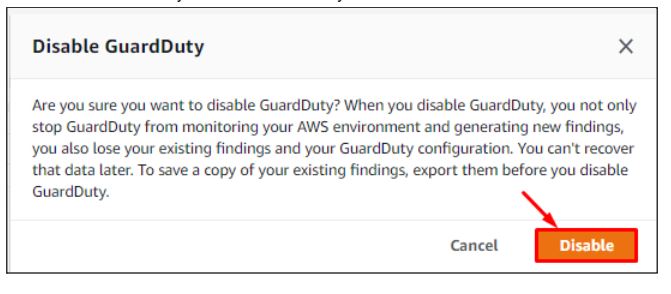
However, disabling GuardDuty not only halts its monitoring and generation of new findings but also results in the loss of existing findings and configurations. Once disabled, the data cannot be recovered later.
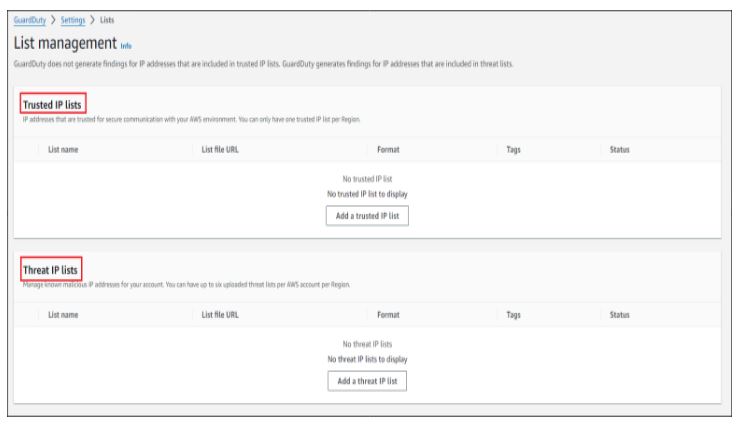
Lists
Select “Lists” beneath the “Settings” section. In the List Manager, you can include Trusted IP Lists and Threat IP Lists.
Trusted IP Lists include IP addresses authorized for secure communication with your AWS environment. GuardDuty refrains from generating findings for IP addresses present in these trusted lists, acknowledging them as secure.
On the other hand, Threat IP Lists comprise known malicious IP addresses. GuardDuty actively generates findings for any IP addresses identified within threat lists, helping to identify and respond to potential security threats.
Accounts
Click on Accounts above the settings.
You have the option to extend invitations to other accounts, inviting them to enable GuardDuty and establish an association with your AWS account. Upon acceptance, your account assumes the role of the master GuardDuty account.
The account accepting the invitation transforms into a member account linked to your master account. This arrangement allows you to oversee and administer GuardDuty findings on behalf of the associated member account.
Notably, a master account in GuardDuty, for each region, can manage up to 1000 member accounts.
Task 4: Generating Sample Findings
To simulate and explore sample security findings in our AWS Account, follow these steps:
Navigate to the “Settings” section from the left panel.
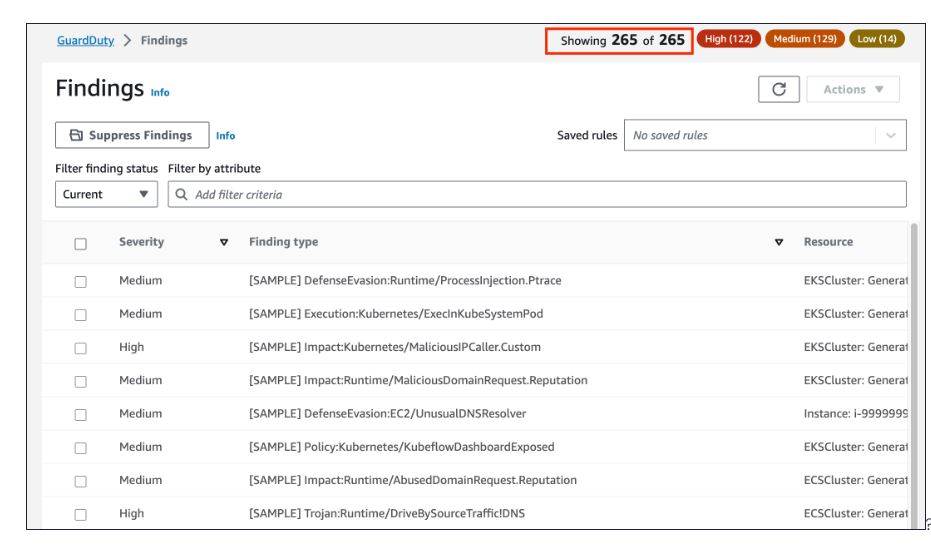
Scroll down and click on “Generate sample findings.”
Go to “Findings” from the left panel and wait for the loading process to complete. In the top-right corner, you should observe several findings.
This process allows you to generate and examine example security findings in your AWS environment.
You can use filter criteria to filter your findings.
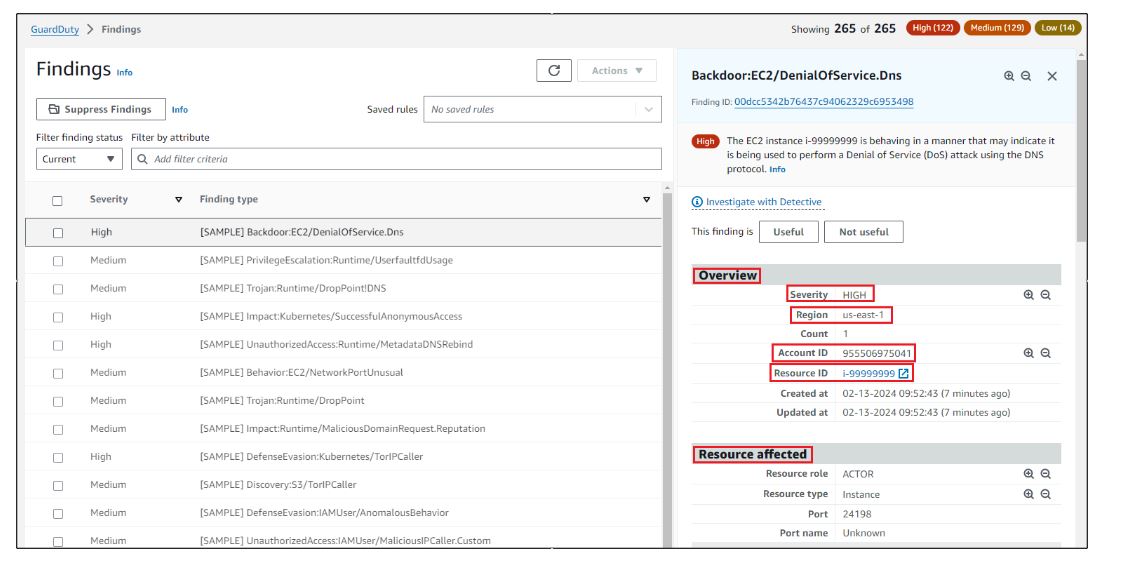
Click on one of the sample findings.
You can see various parameters like severity, region, Account ID, Resource ID, Resource Affected, etc.
Go through the sample to learn more about the different severities.
Task 5: Validation of the Lab
Once the lab steps are completed, please click on the Validation button on the right-side panel.
This will validate the resources in the AWS account and display whether you have completed this lab successfully or not.
Task 6: Disabling GuardDuty
Go to the settings and click on DisableGuardDuty under suspend GuardDuty to stop it.
Click on Disable to confirm and you have successfully disabled GuardDuty.
AWS GuardDuty Use Cases
- Protect your compute workloads: detect whether your EC2 instance is mining cryptocurrency or communicating with IP addresses and domains connected with known dangerous actors.
- Protect your AWS credentials: detect whether your AWS credentials are used unusually or suspiciously, such as from IP addresses connected with known malicious actors, or in a manner that differs from their expected behavior.
- Protect your data stored in Amazon S3 buckets: identify when data stored in your Amazon S3 buckets are accessed in an unusually suspicious manner, such as when an unusual volume of items is obtained from an odd location, or when the S3 bucket is visited from IP addresses connected with known malicious actors.
Also Read: Free AWS Cloud Practitioner Exam Questions
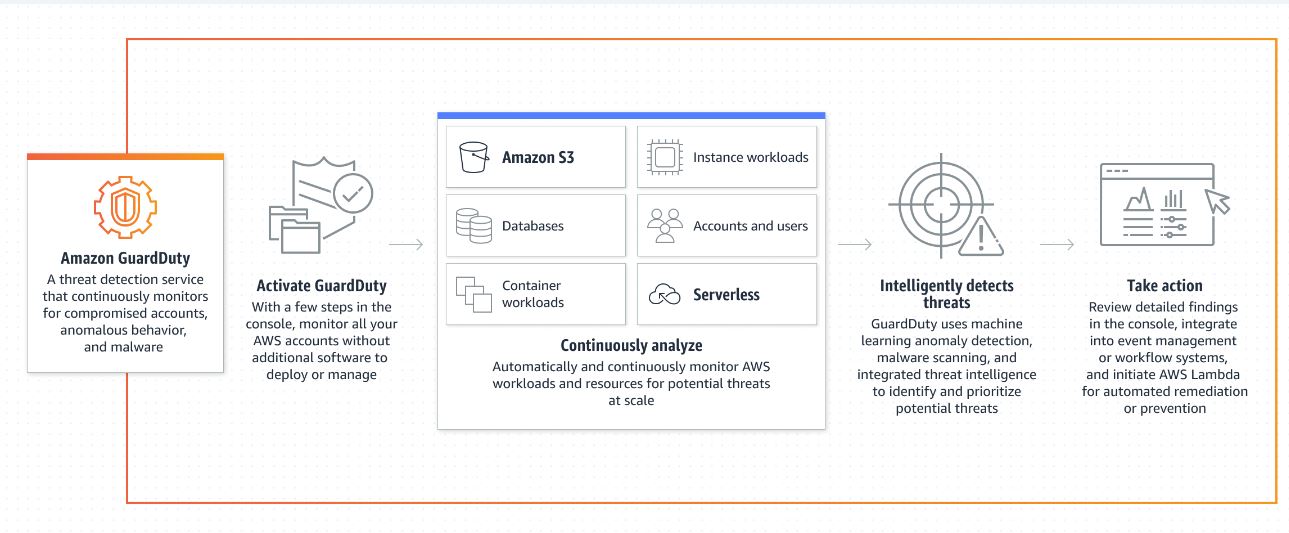
How does AWS GuardDuty work?
Amazon GuardDuty provides continuous monitoring of AWS CloudTrail, Amazon VPC Flow Logs, and DNS logs to detect potential security threats. Utilizing built-in threat intelligence, anomaly detection, and machine learning capabilities developed by the AWS security team, the service conducts near-real-time analysis.
Source: AWS
GuardDuty classifies AWS cloud threats into three categories:
- Attacker reconnaissance: This includes identifying failed login patterns, unusual API activity, and instances of port scanning.
- Compromised resources: GuardDuty detects threats such as cryptojacking, abnormal increases in network traffic, and unauthorized access to EC2 instances through an external IP address.
- Compromised accounts: This category involves recognizing API calls from unexpected locations, attempts to disable CloudTrail, and irregular deployments of instances or infrastructure.
While administrators can specify a list of “safe” IP addresses for GuardDuty, the service does not support custom detection criteria. However, administrators can provide feedback on GuardDuty findings by indicating approval or disapproval.
GuardDuty sends security alerts to the Management Console in JSON format, enabling administrators or automated workflows to take appropriate actions. For instance, Amazon CloudWatch Events can leverage GuardDuty findings to trigger AWS Lambda code for adjusting security configurations.
Security findings are retained in the GuardDuty console and APIs for 90 days.
GuardDuty accounts management
You can assign administration to any account inside the organization when using GuardDuty with an AWS Organizations organization.
Only the organization management account has the authority to designate GuardDuty delegation administrators.
GuardDuty is automatically activated in the chosen Region for a delegated administrator account, which also gains the authority to enable & maintain GuardDuty for all accounts in the organization within that Region.
The delegated administrator account may be linked with additional organization accounts for inspection and addition as GuardDuty partner accounts.
Key considerations for GuardDuty delegated administrators
Capable of handling up to 5000 members, GuardDuty sets a maximum limit of 5000 member accounts for each delegated administrator. While this limit may be sufficient for many businesses, those with more than 5000 clients can track the total number of accounts under the “Accounts” section in the GuardDuty interface.
To address potential concerns, GuardDuty employs various notification methods if the member accounts exceed the 5000 limit, including alerts through CloudWatch, the AWS Health Dashboard, and an email sent to the delegated administrator account.
It’s essential to note that GuardDuty operates as a regional service, unlike AWS Organizations.
Consequently, delegated administrators and their associated member accounts must be added to each desired region to activate account management via AWS Organizations across all regions.
Organizations are limited to having a single delegated administrator per organization, and each account can only have one delegated administrator.
While the management account of your organization can serve as the delegated administrator, it is not recommended by AWS Security best practices, adhering to the principle of least privilege.
Notably, changing the delegated administrator does not disable GuardDuty for member accounts. When a delegated administrator is removed, all associated member accounts cease being GuardDuty members, but GuardDuty is not deactivated in those accounts.
Amazon GuardDuty Pricing
Upon initial activation, AWS offers a complimentary 30-day full-access trial for Amazon GuardDuty, allowing users to assess its suitability. Following this trial period, Amazon GuardDuty provides an estimated cost, representing the potential expenses if the free trial were not available.
The pricing for analyzing AWS log data is influenced by the extent of the analysis conducted.
Unlike CloudTrail Event Logs, which incur charges based on a per-million-events-per-month model, VPC Flow Logs and DNS Logs are billed on a per-gigabyte-per-month basis.
Pricing structures may vary by region but typically include the following tiers:
| Service | Usage Tier | Price per Unit |
| VPC Flow Log and DNS Log Analysis | First 500 GB / month | $1.00 per GB |
| Next 2000 GB / month | $0.50 per GB | |
| Over 2500 GB / month | $0.25 per GB | |
| AWS CloudTrail Event Analysis | Per 1,000,000 events/month | $4.00 per 1,000,000 |
GuardDuty offers continuous monitoring of your infrastructure, ensuring cost efficiency by billing only for the actual detection capacity utilized. In essence, charges are incurred solely for the volume of service utilized.
Conclusion
By following the outlined steps, you can enable GuardDuty with just a click or API request. The service is designed to automatically monitor and assess potential threats, allowing you to customize settings based on your security preferences.
With its ability to adapt to varying resource utilization needs, GuardDuty provides a proactive defence against suspicious or malicious activities.
By leveraging its three severity categories, Low, Medium, and High, GuardDuty assists in prioritising responses to potential threats, ensuring a robust and dynamic security posture for your AWS accounts and workloads.
- Top 25 AWS Data Engineer Interview Questions and Answers - May 11, 2024
- What is Azure Synapse Analytics? - April 26, 2024
- AZ-900: Azure Fundamentals Certification Exam Updates - April 26, 2024
- Exam Tips for AWS Data Engineer Associate Certification - April 19, 2024
- Maximizing Cloud Security with AWS Identity and Access Management - April 18, 2024
- A Deep Dive into Google Cloud Database Options - April 16, 2024
- GCP Cloud Engineer vs GCP Cloud Architect: What’s the Difference? - March 22, 2024
- 7 Ways to Double Your Cloud Solutions Architect Role Salary in 12 Months - March 7, 2024