Are you preparing for AWS Certified SysOps Administrator – Associate certification exam? Are you ready to pass this AWS associate exam? In this blog, we are writing a series of articles on topics which are covered in the AWS Certified SysOps Associate certification exam. You can subscribe to us for receiving further updates on this topic.
The SysOps Associate certification exam is the hardest exam at the associate certification level. We would recommend you pass both the AWS associate architect certification exam and developer associated certification exam first before of taking this exam.
The AWS Certified SysOps Administrator – Associate exam validates technical expertise in deployment, management, and operations on the AWS platform
The AWS Certified SysOps Administrator – Associate Level exam validates the candidate’s ability to:
- Deliver the stability and scalability needed by a business on AWS
- Provision systems, services, and deployment automation on AWS
- Ensure data integrity and data security on AWS technology
- Provide guidance on AWS best practices
- Understand and monitor metrics on AWS
Figure #0. Domains covered by the AWS Certified SysOps associate exam
You can download the related AWS Certified SysOps Administrator – Associate Level Exam Blueprint for more detail about it.
In this article, we are going to explain about the topic that addresses the “demonstrate the ability to implement networking features of AWS” as highlighted in the AWS Blueprint from the above exam guide.
Context
The Cloud computing provides agility for organizations. It mays increase users’ flexibility with re-provisioning, adding, or expanding technological infrastructure resources fast. Also, it could contribute to cost reductions.
It is a model for enabling ubiquitous, on-demand access to a shared pool of configurable computing resources which can be rapidly provisioned and released with minimal management effort.
You could provision a logically isolated section of the Amazon Web Services cloud where you can launch infrastructure resources and services in a virtual network that you define, like your corporate datacenter network. You have complete control over your virtual networking environment, it is called a Virtual Private Cloud (VPC).
What is Amazon VPC?
Amazon Virtual Private Cloud (Amazon VPC) enables you to launch Amazon Web Services (AWS) resources into a virtual network that you’ve defined, with the benefits of using the scalable infrastructure of AWS.
You can launch your AWS resources, such as Amazon EC2 instances, into your VPC. You can configure your VPC; you can select its IP address range, create subnets, and configure route tables, network gateways, and security settings.
You can create a VPC quickly and easily using the AWS Management Console. You can instantly scale your resources up or down, select Amazon EC2 instances types and sizes that are right for your applications, and pay only for the resources you use.
A variety of connectivity options exist for your Amazon Virtual Private Cloud:
- Connect directly to the Internet (public subnets): You can launch instances into a publicly accessible subnet where they can send and receive traffic from the Internet.
- Connect to the Internet using Network Address Translation (private subnets)– Private subnets can be used for instances that you do not want to be directly addressable from the Internet. Instances in a private subnet can access the Internet without exposing their private IP address by routing their traffic through a Network Address Translation (NAT) gateway in a public subnet.
- Connect securely to your corporate datacenter: All traffic to and from instances in your VPC can be routed to your corporate datacenter over an industry standard, encrypted IPsec hardware VPN connection.
- Connect privately to other VPCs: Peer VPCs together to share resources across multiple virtual networks owned by your or other AWS accounts.
- Connect to Amazon S3 without using an internet gateway or NAT, and control what resources, requests, or users are allowed through a VPC endpoint.
Combine connectivity methods to match the needs of your application– You can connect your VPC to both the Internet and your corporate datacenter and configure Amazon VPC route tables to direct all traffic to its proper destination.
What are the components of Amazon VPC?
Amazon VPC comprises a variety of components like the existing networks at your datacenter:
| Element | Brief description |
| Virtual Private Cloud (VPC) | A logically isolated virtual network in the AWS cloud. You define a VPC’s IP address space from a range you select. |
| Subnet | A segment of a VPC’s IP address range where you can place groups of isolated resources. |
| Internet Gateway | The Amazon VPC side of a connection to the public Internet. |
| NAT Gateway | A highly available, managed Network Address Translation (NAT) service for your resources in a private subnet to access the Internet. |
| Hardware VPN Connection | A hardware-based VPN connection between your Amazon VPC and your datacenter, home network, or co-location facility. |
| Virtual Private Gateway | The Amazon VPC side of a VPN connection. The Customer gateway is the customer side of a VPN connection. |
| Peering Connection | A peering connection enables you to route traffic via private IP addresses between two peered VPCs |
| VPC Endpoint | Enables Amazon S3 access from within your VPC without using an Internet gateway or NAT, and allows you to control the access using VPC endpoint policies. |
Table #1. VPC relevant concepts
Your AWS resources are automatically provisioned in a ready-to-use default VPC. You can choose to create additional VPCs by going to the Amazon VPC page in the AWS Management Console and selecting “Start VPC Wizard“, as follow:
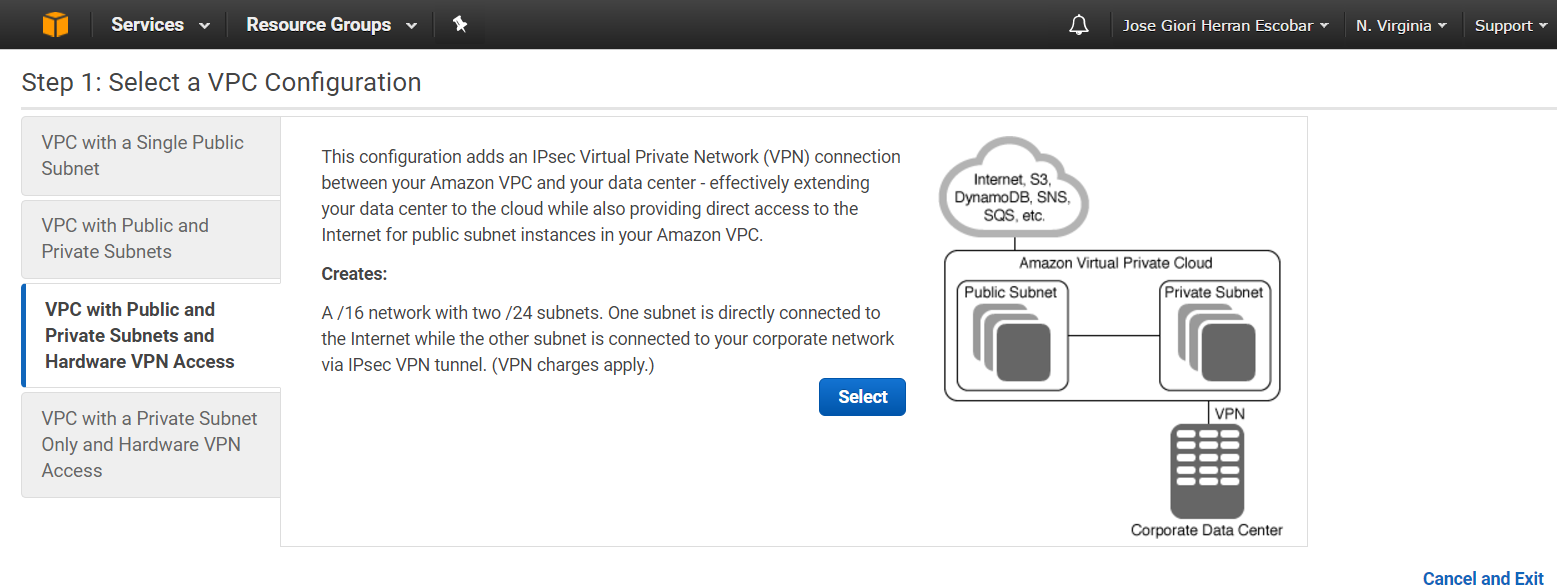
Figure #1. Getting started with the VPC Wizard
You can modify the VPC to add more subnets or add or remove gateways at any time after the VPC has been created. You’ll be presented with the following four basic options for network architectures:
- VPC with a Single Public Subnet Only
- VPC with Public and Private Subnets
- VPC with Public and Private Subnets and Hardware VPN Access
- VPC with a Private Subnet Only and Hardware VPN Access
Accessing the Internet
Amazon VPC supports the creation of an Internet gateway. This gateway enables Amazon EC2 instances in the VPC to directly access the Internet.
You can use public IP addresses, including Elastic IP addresses (EIPs), to give instances in the VPC the ability to both directly communicate outbound to the Internet and to receive unsolicited inbound traffic from the Internet. EC2 instances without public IP addresses can route their traffic through a NAT gateway or a NAT instance to access the Internet. Also, you may use a third-party software VPN to create a site to site or remote access VPN connection with your VPC via the Internet gateway.
Securing the access to your VPC resources
Amazon VPC provides advanced security features such as security groups and network access control lists to enable inbound and outbound filtering at the instance level and subnet level.
Amazon VPC provides features that you can use to increase and monitor the security for your VPC:
- Security groups: Act as a firewall for associated Amazon EC2 instances, controlling both inbound and outbound traffic at the instance level
- Network access control lists (ACLs): Act as a firewall for associated subnets, controlling both inbound and outbound traffic at the subnet level
- Flow logs: Capture information about the IP traffic going to and from network interfaces in your VPC
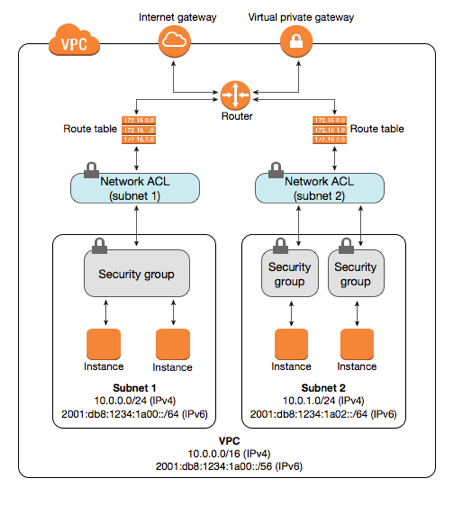
Figure #2. Layers of security provided by security groups and network ACLs
Differences between Security Groups and NACLs
A security group acts as a virtual firewall for your instance to control inbound and outbound traffic. When you launch an instance in a VPC, you can assign the instance to up to five security groups. If you don’t specify a group at launch time, the instance is automatically assigned to the default security group for the VPC. For each security group, you add rules that control the inbound traffic to instances, and a separate set of rules that control the outbound traffic.
A network access control list (ACL) is an optional layer of security for your VPC that acts as a firewall for controlling traffic in and out of one or more subnets. The following table illustrates the differences between both security topics:
| Security Groups | Network ACLs |
| Stateful: Return traffic is automatically allowed, regardless of any rules | Stateless: Return traffic must be explicitly allowed by rules |
| Operates at the instance level | Operates at the subnet level, automatically applies to all instances in the subnets |
| Supports allow rules only | Supports allow rules and deny rules |
| All rules are evaluated before deciding whether to allow traffic | Rules are evaluated in number order when deciding whether to allow traffic |
Table #2. Differences between Security Groups and NACLs
As the AWS Shared Responsibility Model is established, the AWS subscriber is the responsible and required to EC2 security using security groups and network ACLs.
How to modify Network Access Controls (NACLs)?
A network ACL contains a numbered list of rules that we evaluate in order, starting with the lowest numbered rule, to determine whether traffic is allowed in or out of any subnet associated with the network ACL.
A network ACL has separate inbound and outbound rules, and each rule can either allow or deny traffic. You can specify any protocol that has a standard protocol number.
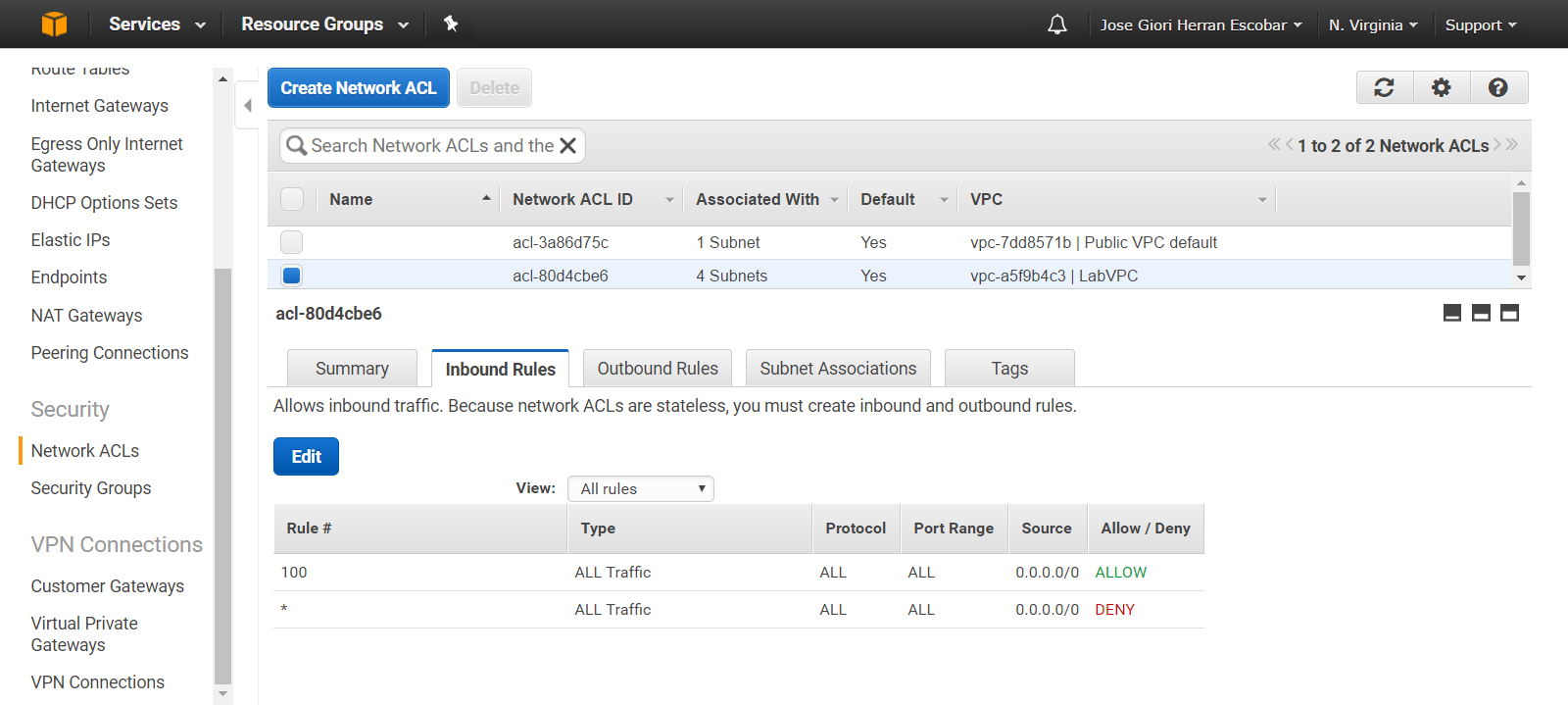
Figure #3. Modifying rules into a Network ACL
Important Points to Remember for the AWS Certified SysOps Administrator – Associate Certification exam
- Amazon VPC lets you provision a logically isolated section of the Amazon Web Services (AWS) cloud where you can launch AWS resources in a virtual network defined.
- There are no additional charges for creating and using the VPC, you pay only for the resources you use into a VPC
- EC2 instances in a private subnet can access by routing their traffic through a Network Address Translation (NAT) gateway located into a public subnet
- EC2 instances in a public subnet can browse the internet using an Internet gateway
- A network ACL allows communication between different subnets, supporting allow rules and deny rules
- The network ACL rules are evaluated in number order when deciding whether to allow traffic
- A security group allows communication between EC2 instances into a specific protocol/port
- Stateful filtering tracks the origin of a request and can automatically allow the reply to the request to be returned to the originating computer
- Traffic which is not explicitly allowed to or from an instance is automatically denied
Glossary
| Term | Brief description |
| VPC | Virtual private cloud. An elastic network populated by infrastructure, platform, and application services that share common security and interconnection. |
| Subnet | It is a range of IP addresses in your VPC. You can launch AWS resources into a subnet that you select. Use a public subnet for resources that must be connected to the Internet, and a private subnet for resources that won’t be connected to the Internet. |
| Route table | A set of routing rules that controls the traffic leaving any subnet that is associated with the route table. You can associate multiple subnets with a single route table, but a subnet can be associated with only one route table at a time. |
| Security Group | A named set of allowed inbound network connections for an instance. (Security groups in Amazon VPC also include support for outbound connections.) Each security group consists of a list of protocols, ports, and IP address ranges. A security group can apply to multiple instances, and multiple groups can regulate a single instance. |
| Network ACL | An optional layer of security that acts as a firewall for controlling traffic in and out of a subnet. You can associate multiple subnets with a single network ACL, but a subnet can be associated with only one network ACL at a time. |
| Internet gateway | Connects a network to the Internet. You can route traffic for IP addresses outside your VPC to the Internet gateway. |
| NAT gateway | A NAT device, managed by AWS, that performs network address translation in a private subnet, to secure inbound Internet traffic. A NAT gateway uses both NAT and port address translation. |
Don’t MISS IT : 420 Practice Questions for SysOps Administrator Exam (50% Discount)
Summary
In this article, we have explained about the security and connectivity options provided by the Amazon Virtual Private Cloud at networking level, discussing differences between security groups and network ACLs and describing core elements located into a VPC.
References:
[1] Amazon VPC FAQs. Amazon AWS. https://aws.amazon.com/vpc/faqs
[2] Amazon VPC Documentation. Amazon AWS. https://aws.amazon.com/documentation/vpc
[3] AWS SysOps Administrator – Associate Certification. https://aws.amazon.com/certification/certified-sysops-admin-associate/
[4] AWS Glossary. Amazon AWS. http://docs.aws.amazon.com/general/latest/gr/glos-chap.html
- Top 20 Questions To Prepare For Certified Kubernetes Administrator Exam - August 16, 2024
- 10 AWS Services to Master for the AWS Developer Associate Exam - August 14, 2024
- Exam Tips for AWS Machine Learning Specialty Certification - August 7, 2024
- Best 15+ AWS Developer Associate hands-on labs in 2024 - July 24, 2024
- Containers vs Virtual Machines: Differences You Should Know - June 24, 2024
- Databricks Launched World’s Most Capable Large Language Model (LLM) - April 26, 2024
- What are the storage options available in Microsoft Azure? - March 14, 2024
- User’s Guide to Getting Started with Google Kubernetes Engine - March 1, 2024



