This blog divides the Azure content into main themes, namely key management, secrets management, certificate management, data security, backup and recovery, and integrations to enhance understanding. Read more to understand the perspective of a Microsoft Certified Professional holding the AZ-900 certification.
Key Management
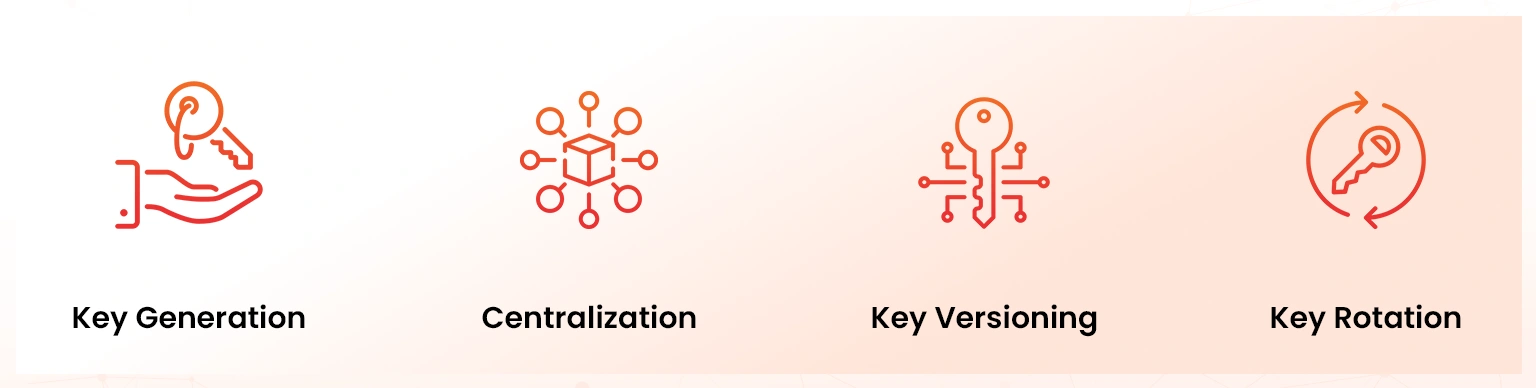
Key management is crucial in ensuring key security from generation up to destruction. The following are the key benefits that Azure Key Vault provides in key management:
- Key generation. You can generate cryptographic keys using Azure Key Vault for your organization. The term ‘key’ within the context of the Azure terminology refers to any cryptographic keys that are used to perform encryption, decryption of information, as well as the creation of digital signatures.
- Centralization: Azure Key Vault provides you with a centralized repository that allows you to securely and conveniently generate, store, and control cryptographic keys. This allows organizations to securely implement key rotation, monitor key usage, and audit key activities to ensure compliance with industry standards and regulations.
- Key versioning: Azure Key Vault provides key versioning capabilities, offering a comprehensive view of key usage and access history. Organizations can track key activities, monitor changes, and gain insight into key usage patterns, improving their ability to detect and respond to potential security incidents effectively.
- Key rotation: You can also perform automated cryptographic key rotation using Azure Key Vault, allowing users to configure Key Vault to automatically generate a new key version at a specified frequency. To securely implement the configuration settings, you can use the key rotation policy, which can be defined on each key.
Secrets management
It is critical to understand the differences between keys and secrets in Azure terminology. We have already discussed keys in the above sections. Secrets in Azure refer to any confidential information such as passwords, database connection strings, and Application Programming Interface (API) keys that should be kept private and secure in an organization. Azure Key Vault protects secrets in the following ways:
- Centralized repository: Azure Key Vault provides a centralized repository that enables organizations to securely store secrets. There is no need for organizations to hard-code secrets directly into the application code or configuration files. Users can also retrieve secrets from Azure Key Vault at runtime, thus reducing the risk of accidental exposure.
- Fine-grained access policies: With Azure Key Vault, you can define fine-grained access policies, thereby ensuring that only authorized users and applications can access specific secrets in your organization.
- Secrets segregation: Through the segregation, Azure Key Vault can allow applications to access only the authorized vaults. They can also be limited to performing only specific operations. Organizations can create a separate segment of Azure Key Vault per application and restrict the secrets stored to a specific application or team of developers.
Certificate Management
Certificate Management: Azure Key Vault also allows for the secure handling of certificates in an organization. These certificates include the Transport Layer Security (TLS) certificates that you use alongside Azure and your internal connected resources.
- Certificate storage: You can use Azure Key Vault to securely store and manage your certificates, including X.509 certificates. The functionality supports both internally generated and self-signed certificates as well as those signed by trusted CAs. This process can also happen without the need for certificate owners to interact with the private key material.
- Certificate lifecycle: Azure Key Vault simplifies managing the certificate lifecycle. Organizations can easily create, renew, and revoke certificates as required, ensuring that they remain current and valid. They can also access and manage certificates through APIs or client libraries, thus integrating certificates into applications and services.
- Seamless use of certificates: The integration of Azure Key Vault with other Azure services, including Azure App Service and Azure Functions, allows for the seamless use of certificates in various Azure-based applications. For instance, developers can bind TLS certificates stored to their web applications hosted on Azure App Service. This provides secure and encrypted communications between clients and servers.
Data Protection
Data protection is a crucial area in any cloud environment and Azure Key Vault ensures the security of data through its life cycle. The following are some of the functionalities provided by Azure Key Vault in the protection of organizational data:
- Encryption: Azure Key Vault encrypts keys and small secrets, such as passwords, and protects data in transit. It uses the latest version of the Transport Layer Security (TLS) protocol to protect data traveling between Azure Key Vault and clients.
- Conditional Access: Azure Key Vault supports Microsoft Entra Conditional Access policies, allowing you to deploy the correct access controls to key vaults. This solution ensures that unauthorized access is restricted, thus further enhancing the security of the cloud environment.
- Privileged access: With Azure Key Vault, you can also configure controls to enhance privileged access security in your organization. The feature uses RBAC and Azure Key Value Access policies to provide authorization mechanisms both on the management and data planes. This ensures that your privileged accounts will remain protected from unauthorized access.
- Hardware Security Module (HSM): Azure Key Vault also deploys Azure Dedicated HSMs to provide secure cryptographic key storage in Azure, thus meeting even the most stringent security requirements, such as FIPS 140-2 Level 3. This also provides a higher level of security than software-based solutions.
- Key vault access policy: Azure Key Vault also establishes a key vault access policy that allows an organization to control a variety of access conditions in the organization, such as who can access and when they can access application secrets. It can also go a step further to determine what operations users can perform with the provisioned secrets.
- Secure connections: This is a key benefit for establishing a secure and private connection between Azure resources and client devices. For instance, organizations can connect to other Azure services through a secure and flexible private IP address in their virtual network with the help of Azure Private Link.
- Key Vault firewall: For enhanced security, you deploy the Key Vault firewall to restrict access to specific IP ranges, service endpoints, virtual networks, or private endpoints. This ensures the security of internal cloud assets from external attacks and vulnerabilities.
- Logging and Monitoring Access Azure Key Vault provides logging capabilities, a critical aspect of any cloud security infrastructure. The following features of Azure Key Vault assist an organization to implement effective processes to track and analyze activities related to keys and secrets:
Key Logging: Azure Key Vault also provides keylogging capabilities, including saving information about the activities performed on your vault. These logs are then subjected to detailed analysis, providing information on various key management activities.
Login capabilities: Azure Key Vault supports log-in to a variety of Azure resources, such as Azure Event Hubs and Azure Log Analytics. By enabling logging to these destinations, organizations can have a centralized repository of Key Vault logs, making it easier to analyze and correlate activities across their entire Azure environment.
Backup and recovery
Azure Key Vault provides the following backup and recovery capabilities, thus ensuring the resilience of the Azure cloud infrastructure:
- Key backup: With Azure Key Vault, you should be able to perform regular backups of your vault on update/delete/creation of objects within a Vault. This streamlines the backup process and allows for a quicker recovery in the event of incidents and disasters in the organization.
- Failover: Azure Key Vault maintains availability corresponding to a variety of disaster scenarios. It can then be configured to automatically fail over requests to a paired region without any intervention from a user. This allows the organization to continue operations in the event of an attack or any other disaster.
- Soft Delete: Azure Key Vaults supports the implementation of Soft Delete, storing a ‘soft deleted’ state for a specified period after deletion. This helps prevent accidental data loss due to deleted vaults and allows the recovery of deleted assets if needed. It also allows you to set the Soft Delete Retention Period, allowing you to set the duration of time that soft deleted assets are recoverable before they are permanently purged. This enables you to strike a balance between data protection and efficient data management.
- Purge Protection: This feature prevents the permanent deletion of cryptographic assets in Azure. You can also configure Permitted Purger to set the soft deletion retention period, in which only authorized users or processes with sufficient permissions can execute a ‘purge’ operation, permanently deleting cryptographic assets. This provides controlled access, which minimizes the risk of unintended data loss.
- Key Vault Object Recovery: When a cryptographic asset is accidentally or intentionally deleted during the soft delete retention period, you can perform an extensive recovery mechanism using Key Vault Object Recovery. This feature allows you to recover specific cryptographic assets individually and in a granular, rather than the entire key vault. This streamlines the restoration process and improves operational efficiency.
Integrations
Azure Key Vault can also be integrated with other Azure services, thus allowing these services to have secure access to keys and secrets. This seamless integration enables you to leverage its capabilities within their cloud-based applications and infrastructure.
- Event Grid: Azure Key Vault can be securely integrated with Event Grid. This allows you to get notified of specific security events happening around key management, including when the status of a key, certificate, or secret stored in a key vault changes.
- Microsoft Defender for Cloud: Azure Key Vault integrates well with Microsoft Defender for Cloud. You can therefore obtain a comprehensive view of their security posture and receive actionable recommendations to improve the security of their cryptographic assets stored in the Azure Key Vault.
- Azure Monitor: This integration allows organizations to collect, analyze, and act on the telemetry data generated by Key Vault. You can set up custom alert rules to enable you to detect specific security events or anomalies happening around key management. These include unauthorized access attempts or excessive use of cryptographic assets.
Conclusion
In conclusion, Azure Key Vault serves many functions in the management of cryptographic keys, secrets, and certificates. Its centralized approach allows the organization to streamline key and secret management, allowing authorized personnel to access and control these sensitive assets from a unified platform. Organizations also ensure the consistency and integrity of their cryptographic assets, reducing the risk of exposure and unauthorized access. Azure Key Vault also simplifies auditing and compliance as organizations can easily track access and usage of cryptographic assets, enabling complete log and monitoring, which is crucial to meeting regulatory requirements and maintaining a secure and compliant environment.
- What are the career opportunities with AZ-104? - April 10, 2025
- Why Is Microsoft Entra Important for Cybersecurity? - March 26, 2025
- Why is Microsoft Fabric Essential for Data Analytics? - March 14, 2025
- How does AWS Lambda Support AI Inference and Model Execution - March 4, 2025
- How to Optimize ML Pipelines on AWS for AI Practitioners - February 17, 2025
- How to Improve Model Outcomes with AWS ML Performance Tools? - January 15, 2025
- Conditional Access in Microsoft Entra ID Enhances Security - January 9, 2025
- Why Use Azure Key Vault for Key Management & Data Protection - January 7, 2025