Cloud Engineers make use of the HashiCorp Consul Associate certification to attest their Networking Automation Skills. You are at a plus point if you have a good understanding of the basic skills and concepts required in the building, security, and maintenance of the open-source HashiCorp Consul.
These free test questions provided here are for your assessment of the HashiCorp Consul Associate exam and help you with your preparation.
Domain: Deploy a single datacenter
Q1 : Environment variables can be used to configure the Consul client and they can be used when running other consul CLI commands that connect with a running agent.
A. True
B. False
Correct Answer: B
Explanation
Environment variables cannot be used to configure the Consul client. They can be used when running other consul CLI commands that connect with a running agent,
e.g. CONSUL_HTTP_ADDR=192.168.0.1:8500 consul members..
Reference: https://www.consul.io/docs/agent/options#environment-variables

Domain : Deploy a single datacenter
Q2 : Consider the given command and select 3 correct options:
consul agent -data-dir=/tmp/consul -dev
A. Agent will be started in the local instance
B. Agent will refer the configuration files from the directory /tmp/consul
C. Agent will work in the development server mode
D. Agent state data will be stored in the directory /tmp/consul
E. Agent details will be persisted in the local instance
Correct Answers: A, C and D
Explanation
The given command will start an agent in dev mode and stores agent state data in the tmp/consul directory
Option A is correct. The agent will be started in the local instance using the command consul agent.
Option B is incorrect. The –config-dir flag is used to mention the directory that will have the configuration files to load. But –data-dir is used in the provided command.
Option C is correct. The –dev flag will enable development server mode.
Option D is correct. The –data-dir flag provides a data directory for the agent to store state. This is required for all agents.
Option E is incorrect. The –dev flag is useful for quickly starting a Consul agent with all persistence options turned off, enabling an in-memory server. This mode is not intended for production use as it does not write any data to disk.
Reference: https://www.consul.io/docs/agent#starting-the-consul-agent
Domain: Deploy a single datacenter
Q3 : Which of the following options is used to control the script checks defined in the local configuration files?
A. enable_script_checks
B. enable_local_script_checks
C. allow_script_checks
D. allow_local_script_checks
Correct Answer: B
Explanation
The option enable_local_script_checks is used to enable script checks defined in local config files. Script checks defined via the HTTP API are not allowed.
Option A is incorrect. The option enable_script_checks controls whether health checks that execute scripts are enabled on this agent, and defaults to false so operators must opt-in to allowing these.
Option B is correct. The option enable_local_script_checks is used to enable script checks defined in local config files. Script checks defined via the HTTP API will not be allowed.
Option C is incorrect. There is no such option called allow_script_checks for the command consul agent.
Option D is incorrect. There is no such option called allow_local_script_checks for the command consul agent.
Reference: https://www.consul.io/docs/agent/options#_enable_local_script_checks
Domain : Deploy a single datacenter
Q4 : You are attempting to connect to a Consul agent and you are getting the below error:
Error querying agent: malformed HTTP response
Net/http: HTTP/1.x transport connection broken: malformed HTTP response “\x15\x03\x01\x00\x02\x02”
Which of the following option(s) can be used to fix the issue?
A. By specifying “https” in the -http-addr flag
B. By specifying “https” in the CONSUL_HTTP_ADDR environment variable
C. By specifying “https” in the CONSUL_HTTP_SSL environment variable
D. By changing the URI scheme to “https”
E. By specifying “https” in the CONSUL_HTTP_AUTH environment variable
Correct Answers: A, B and D
Explanation
These errors will occur when we try to connect to a Consul agent with HTTP on a port that has been configured for HTTPS.
These errors could be fixed by following any one of the below mentioned ways:
- By specifying “https” in the -http-addr flag or the CONSUL_HTTP_ADDR environment variable in terms of Consul CLI.
- By changing the URI scheme to “https” in terms of Consul API.
Option A is correct. –http-port is used to specify the address and port of the Consul HTTP agent. The value can be an IP address or DNS address, but it must also include the port. In order to access the port that has been configured for HTTPS, “https” should be specified.
Option B is correct. This is the HTTP API address to the local Consul agent (not the remote server) specified as a URI with optional scheme. Example: CONSUL_HTTP_ADDR=127.0.0.1:8500 .
In order to access the port that has been configured for HTTPS, “https” should be specified in the CONSUL_HTTP_ADDR environment variable.
Option C is incorrect. CONSUL_HTTP_SSL is a boolean value (default is false) that enables the HTTPS URI scheme and SSL connections to the HTTP API. Example: CONSUL_HTTP_SSL=true.
We can set only the boolean option for the CONSUL_HTTP_SSL environmental variable.
Option D is correct. In order to access the port via API that has been configured for HTTPS, the default http URI scheme should be changed to “https”.
Option E is incorrect. CONSUL_HTTP_AUTH environment variable is used to specify HTTP basic access credentials as a username:password pair.
References: https://www.consul.io/docs/troubleshoot/common-errors#http-instead-of-https, https://www.consul.io/commands#consul_http_ssl, https://www.consul.io/commands#consul_http_auth
Domain : Deploy a single datacenter
Q5 : Which of the following commands is used to allow a Consul agent to automatically join a Consul datacenter using cloud metadata?
A. consul join <ip_address of the datacenter> -metadata=”provider=my-cloud config=val”
B. consul agent -retry-join “consul.domain.internal” -retry-join “<ip_address of the datacenter>”
C. consul agent -retry-join ‘provider=my-cloud config=val config2=some other val’
D. consul agent -join <ip_address of the datacenter> -metadata=”provider=my-cloud config=val”
Correct Answers: C
Explanation
As of Consul 0.9.1, retry-join accepts a unified interface using the go-discover library for automatically joining a Consul datacenter using cloud metadata.
To use retry-join with a supported cloud provider, specify the configuration on the command line or configuration file as a key=value key=value … string.
Option A is incorrect. Consul join command tells a Consul agent to join an existing cluster. But there is no such option called –metadata.
Option B is incorrect. –retry-join option allows retrying the Consul agent to join with another agent until it is successful. Once it joins successfully to a member in a list of members it will never attempt to join again.
Option C is correct. The command consul agent -retry-join ‘provider=my-cloud config=val config2=some other val’ is used for automatically joining a Consul datacenter using cloud metadata.
Example:
consul agent -retry-join “provider=aws tag_key=… tag_value=…”
This returns the first private IP address of all servers in the given region which have the given tag_key and tag_value.
Option D is incorrect. There is no such option called –join and –metadata for the command Consul agent.
Reference: https://www.consul.io/docs/install/cloud-auto-join#cloud-auto-join
Domain : Deploy a single datacenter
Q6 : You have been provided with a task to join the Consul agent to an existing cluster with the IP addresses as follows: 52.10.110.11, 52.10.110.12, 52.10.110.13.
Identify the correct agent configuration options that are suitable for to add/join additional servers in production environments.
A. consul agent -retry-join=52.10.110.11 -retry-join=52.10.110.12 -retry-join=52.10.100.13
B. bootstrap = false,
bootstrap_expect = 3,
server = true,
retry_join = [“52.10.110.11”, “52.10.110.12”, “52.10.100.13”]
C. {
“bootstrap”: false,
“bootstrap_expect”: 3,
“server”: true,
“retryjoin”: [“52.10.110.11”, “52.10.110.12”, “52.10.100.13”]
}
D. consul agent -join=52.10.110.11 -join=52.10.110.12 -join=52.10.100.13
E. bootstrap = false,
bootstrap_expect = 3,
server = true,
retryjoin = [“52.10.110.11”, “52.10.110.12”, “52.10.100.13”]
F.{
“bootstrap”: false,
“bootstrap_expect”: 3,
“server”: true,
“retry_join”: [“52.10.110.11”, “52.10.110.12”, “52.10.100.13”]
}
Correct Answers: A, B and F
Explanation
For production datacenters, we will likely want to use the agent configuration option to add additional servers.
In production environments, we will use the agent configuration option, retry_join. retry_join can be used as a command line flag or in the agent configuration file(in .hcl and .json format).
retry join will ensure that if any server loses connection with the datacenter for any reason, including the node restarting, it can rejoin when it comes back. In addition to working with static IPs, it can also be useful for other discovery mechanisms, such as auto joining based on cloud metadata and discovery. Both servers and clients can use this method.
Option A is correct. Via CLI, the command consul agent -retry-join=52.10.110.11 -retry-join=52.10.110.12 -retry-join=52.10.100.13 is used to join the Consul agent to the provided clusters.
Option B is correct. The provided agent configuration stanza (in the .hcl format) is used to join the Consul agent to the provided clusters.
Option C is incorrect. The provided agent configuration stanza is in the .hcl format but the option retry_join is misspelled as “retryjoin”.
Option D is incorrect. The consul join command tells a Consul agent to join an existing cluster.
Option E is incorrect. The provided agent configuration stanza is in the .json format but the retry_join is misspelled as “retryjoin”.
Option F is correct. The provided agent configuration stanza (in the .json format) is used to join the Consul agent to the provided clusters.
Domain : Secure services with basic access control lists (ACL)
Q7 : Consider the below given HTTP API request:
curl –request GET http://127.0.0.1:8500/v1/acl/———-
Fill in the blank with the correct endpoint to get the below response:
{
“Enabled”: true,
“Running”: true,
“SourceDatacenter”: “dc1”,
“ReplicationType”: “tokens”,
“ReplicatedIndex”: 1976,
“ReplicatedTokenIndex”: 2018,
“LastSuccess”: “2018-11-03T06:28:58Z”,
“LastError”: “2016-11-03T06:28:28Z”
}
A. replicate
B. replication
C. replica
D. auth/replicate
Correct Answer: B
Explanation
/acl/replication endpoint returns the status of the ACL replication processes in the datacenter. This is intended to be used by operators or by automation checking to discover the health of ACL replication.
Option A is incorrect. There is no such endpoint called replicate in Consul ACL HTTP API
Option B is correct. The replication endpoint returns the status of the ACL replication processes in the datacenter.
Option C is incorrect. There is no such endpoint called replica in Consul ACL HTTP API.
Option D is incorrect. There is no such endpoint called auth/replicate in Consul ACL HTTP API.
Reference: https://www.consul.io/api-docs/acl#check-acl-replication
Domain : Secure services with basic access control lists (ACL)
Q8 : Which of the following methods are the possible ways to pass the Consul token(Secret ID) with each API request?
A. Consul-Token : <consul token>
B. Authorization : Bearer <consul token>
C. ?token = query parameter
D. X-Consul-Token : <consul token>
E. Authorization : Token <consul token>
Correct Answers: B, C and D
Explanation
The token Secret ID is passed along with each RPC request to the servers. Consul’s HTTP endpoints can accept tokens via the token query string parameter, the X-Consul-Token request header, or an RFC6750 authorization bearer token.
Previously this was provided via a ?token= query parameter. This functionality exists on many endpoints for backwards compatibility, but its use is highly discouraged, since it can show up in access logs as part of the URL.
Option A is incorrect. There is no such option called Consul-Token : <consul token>.
Option B is correct. When authentication is enabled, a Consul token should be provided to API requests with the Bearer scheme in the authorization header.
curl –header “Authorization: Bearer <consul token>” http://127.0.0.1:8500/v1/agent/members
Option C is correct. This was provided via a ?token= query parameter. This functionality exists on many endpoints for backwards compatibility, but its use is highly discouraged, since it can show up in access logs as part of the URL.
Option D is correct. When authentication is enabled, a Consul token should be provided to API requests using the X-Consul-Token header.
curl –header “X-Consul-Token: <consul token>” http://127.0.0.1:8500/v1/agent/members
Option E is incorrect. The provided Authorization header is not syntactically correct. There is no such keyword called “Token” associated with RFC6750 authorization bearer.
- Incorrect method: Authorization : Token <consul token>
- Correct method: Authorization : Bearer <consul token>
Instead of the keyword “Token”, the keyword “Bearer” should be used.
References: https://www.consul.io/api#authentication, https://www.consul.io/docs/security/acl/acl-system#authorization
Domain : Secure services with basic access control lists (ACL)
Q9 : How will the Consul accept the token Secret ID via environment variable?
A. CONSUL_HTTP_TOKEN_FILE
B. CONSUL_SECRET_TOKEN
C. CONSUL_HTTP_AUTH
D. CONSUL_HTTP_TOKEN
Correct Answer: D
Explanation
Via CONSUL_HTTP_TOKEN, we can store the API access token required when access control lists (ACLs) are enabled.
Option A is incorrect. CONSUL_HTTP_TOKEN_FILE is a path to a file containing the API access token required when access control lists (ACLs) are enabled.
Example: CONSUL_HTTP_TOKEN_FILE=/path/to/consul.token
Option B is incorrect. There is no such environment variable called CONSUL_SECRET_TOKEN.
Option C is incorrect. CONSUL_HTTP_AUTH specifies HTTP Basic access credentials as a username:password pair
Example: CONSUL_HTTP_AUTH=my_username:my_password@123
Option D is correct. CONSUL_HTTP_TOKEN is the API access token required when access control lists (ACLs) are enabled
Example: CONSUL_HTTP_TOKEN=785gerd5-123a-987b-45er-6xyt7ac44st
References: https://www.consul.io/commands#consul_http_token, https://www.consul.io/docs/security/acl/acl-system#authorization
Domain : Secure services with basic access control lists (ACL)
Q10 : By default, Consul assigns the global-management policy to the bootstrap token, which has some restricted privileges which cannot be modified.
A. True
B. False
Correct Answer: B
Explanation:
Once the ACLs have been enabled, a token is needed to complete any operation in Consul. consul acl bootstrap command is used to bootstrap and generate the first master token.
By default, Consul assigns the global-management policy to the bootstrap token, which has unrestricted privileges.
The bootstrap token is a management token with unrestricted privileges which is used in case of emergencies.
Domain : Secure services with basic access control lists (ACL)
Q11 : As a Consul engineer, what will you do in order to save the ACL tokens permanently with an agent?
A. By enabling the flag acl_token_replication as true.
B. By enabling the flag enable_token_replication as true.
C. By enabling the flag enable_token_persistence as true.
D. By enabling the flag acl_token_persistence as true.
E. By enabling the flag acl_enable_token_replication as true.
Correct Answer: C
Explanation
Tokens are not persisted unless acl.enable_token_persistence is true, so tokens will need to be updated again if that option is false and the agent is restarted.
Option A is incorrect. There is no such flag called acl_token_replication in Consul agent configuration.
Option B is incorrect. The flag enable_token_replication will enable ACL token replication and allow for the creation of both local tokens and auth methods in connected secondary datacenters.
Option C is correct. By setting the flag enable_token_persistence as true, the tokens set using the API will be persisted to disk and reloaded when an agent restarts.
Option D is incorrect. There is no such flag called acl_token_persistence in Consul agent configuration.
Option E is incorrect. There is no such flag called acl_enable_token_replication in Consul agent configuration.
Reference: https://www.consul.io/docs/agent/options#acl_enable_token_persistence
Domain : Secure agent communication
Q12 : While configuring the TLS certificates in client and server, you are getting the below errors.
-
Remote error: tls: bad certificate
-
X509: certificate signed by unknown authority
What are the steps that you will consider to troubleshoot/solve these errors?
A. Verifying that the Consul clients and servers are using the correct certificates.
B. Verifying that the certificates are placed in the directory /etc/consul/directories with correct permissions
C. Verifying the details of the certificates using the command consul tls cert verify by passing the client’s and server’s IP address or domain name
D. Verifying that the certificates have been signed by the same CA.
E. Verifying that the server certificates include the special name server.dc1.consul in the Subject Alternative Name (SAN) field.
Correct Answers: A, D and E
Explanation
Below are the steps that need to be followed to troubleshoot the incorrect certificate or certificate name issues:
- Verifying that the Consul clients and servers are using the correct certificates, and that they’ve been signed by the same CA.
- Verifying that the server certificates include the special name server.dc1.consul in the Subject Alternative Name (SAN) field.
Option A is correct. Verifying whether the Consul clients and servers are using the correct certificates or not is one of the correct steps.
Option B is incorrect. The provided step is not the correct one.
Option C is incorrect. The provided step is not the correct one.
Option D is correct. Verifying that the certificates have been signed by the same CA is one of the correct steps.
Option E is correct. Verifying that the server certificates include the special name server.dc1.consul in the Subject Alternative Name (SAN) field is one of the correct steps.
Reference: https://www.consul.io/docs/troubleshoot/common-errors#incorrect-certificate-or-certificate-name
Domain : Secure agent communication
Q13 : You have been provided with the task of enabling the built-in CA in Consul. Identify the correct default configuration to implement the same.
A. /opt/consul.d/config.hcl
# …
connect {
enabled = true
}
B. /etc/consul.d/config.hcl
# …
connect {
enabled = true
}
C. /opt/consul.d/config.hcl
# …
certificate_authority {
enabled = true
}
D. /etc/consul.d/config.hcl
# …
certificate_authority {
enabled = true
}
Correct Answers: B
Explanation
The built-in CA provider has no required configuration. Enabling Connect alone will configure the built-in CA provider, and will automatically generate a root certificate and private key.
Option A is incorrect. The provided configuration is not a valid one as it is using /opt directory.
Option B is correct. The provided configuration is the valid configuration for enabling the built-in CA in Consul.
Option C is incorrect. The provided configuration is not a valid one as it is using /opt directory and wrong option “certificate_authority”.
Option D is incorrect. The provided configuration is not a valid one as it is using the wrong option “certificate_authority”.
Reference: https://www.consul.io/docs/connect/ca/consul#built-in-ca
Domain : Secure agent communication
Q14 : Identify the files that will be generated/saved as a result of executing the below mentioned command:
consul tls cert create -server -dc dc1
A. dc1-server-consul-0.pem
B. server-consul-0.pem
C. dc1-server-consul-0-key.pem
D. server-consul-0-key.pem
Correct Answers: A and C
Explanation
The below mentioned files will be generated as the result of executing the mentioned command:
- dc1-server-consul-0.pem
- dc1-server-consul-0-key.pem
Output:
consul tls cert create -server -dc dc1
==> WARNING: Server Certificates grants authority to become a
server and access all state in the cluster including root keys
and all ACL tokens. Do not distribute them to production hosts
that are not server nodes. Store them as securely as CA keys.
==> Using consul-agent-ca.pem and consul-agent-ca-key.pem
==> Saved dc1-server-consul-0.pem
==> Saved dc1-server-consul-0-key.pem
Option A is correct. dc1-server-consul-0.pem will be generated and this is the Consul server node public certificate for the dc1 datacenter.
Option B is incorrect. This is not the correct file name as the datacenter name is not given as part of the file name.
Option C is correct. dc1-server-consul-0-key.pem will be generated and this is the Consul server node private key for the dc1 datacenter.
Option D is incorrect. This is not the correct file name as the datacenter name is not given as part of the file name.
Reference: https://learn.hashicorp.com/tutorials/consul/tls-encryption-secure#create-the-server-certificates
Domain : Secure agent communication
Q15 : Which command needs to be executed to generate a client certificate with the validity of 3 months(considering 30 days in each month)?
A. consul tls cert create -client –months=3
B. consul tls cert generate -client –days=90
C. consul tls cert generate -client –months=3
D. consul tls cert create -client –days=90
Correct Answer: D
Explanation
The command consul tls cert create -client -days=90 will generate the client certifications with the validity of 90 days a.k.a 3 months.
-days=<int> – Provide the number of days the certificate is valid from now on. Defaults to 1 year.
Option A is incorrect. There is no such option called –month in Consul tls cert create command.
Option B is incorrect. There is no such command called consul tls cert generate even though the provided option –days is correct.
Option C is incorrect. There is no such command called consul tls cert generate.
Option D is correct. The command consul tls cert create -client -days=90 will generate the client certifications with the validity of 90 days
Reference: https://www.consul.io/commands/tls/cert#days
Domain : Register services and use service discovery
Q16 : Consider the below given payload and identity whether this is valid or not.
curl http://127.0.0.1:8500/v1/query \
–request POST \
–data @- << EOF
{
“Name”: “”,
“Template”: {
“Type”: “name_prefix_match”
},
“Service”: {
“Service”: “{name.full}”,
“Failover”: {
“NearestN”: 2
}
}
}
EOF
A. True
B. False
Correct Answer: B
Explanation:
The given payload is an example for a prepared query template but the syntax is not correct.
Instead of {name.full}, ${name.full} should be used to refer to the entire name.
References: https://learn.hashicorp.com/tutorials/consul/automate-geo-failover#prepared-query-template, https://www.consul.io/api/query#prepared-query-templates
Domain : Register services and use service discovery
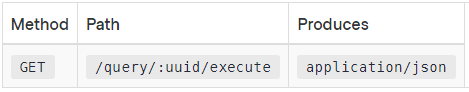
Q17 : Which of the below endpoints is used to run an existing prepared query (for example: 1ab2c3d4-ade3-gg77-5b48-8ec93abf3e05)?
A. /execute
B. /create
C. /run
D. /produce
E. /build
Correct Answer: A
Explanation
The endpoint /execute is used to execute/run an existing prepared query. If no query exists by the given ID, an error is returned.
Option A is correct. Using the endpoint /execute, we can execute an existing prepared query.
Example:
curl http://127.0.0.1:8500/v1/query/1ab2c3d4-ade3-gg77-5b48-8ec93abf3e05/execute?near=_agent
Option B is incorrect. The endpoint /create is used to create a new prepared query and returns its ID if it is created successfully.
Option C is incorrect. There is no endpoint called /run in Consul.
Option D is incorrect. There is no endpoint called /produce in Consul.
Option E is incorrect. There is no endpoint called /build in Consul.
Reference: https://www.consul.io/api/query#execute-prepared-query
Domain : Register services and use service discovery
Q18 : Is it possible to register multiple services via the HTTP API?
A. True
B. False
Correct Answer: B
Explanation
Multiple services definitions can be provided at once when registering services via the agent configuration by using the plural services key.
Multiple services can’t be registered via the HTTP API.
Reference: https://www.consul.io/docs/discovery/services#multiple-service-definitions
Domain : Register services and use service discovery
Q19 : What is the parameter that needs to be passed with the endpoint /agent/check/register to deregister the service after the specified time duration?
A. DeregisterCriticalServiceAfter
B. DeregisterCriticalServiceAfterDuration
C. DeregisterServiceAfterDuration
D. DeregisterServiceAfter
Correct Answer: A
Explanation
The parameter DeregisterCriticalServiceAfter specifies that checks associated with a service should deregister after this time. This is specified as a time duration with a suffix like “10m”.
If a check is in the critical state for more than this configured value, then its associated service (and all of its associated checks) will automatically be deregistered.
Option A is correct. The parameter DeregisterCriticalServiceAfter is used to mention the time duration to deregister the service.
Option B is incorrect. There is no such parameter named DeregisterCriticalServiceAfterDuration for the endpoint /agent/check/register
Option C is incorrect. There is no such parameter named DeregisterServiceAfterDuration for the endpoint /agent/check/register
Option D is incorrect. There is no such parameter named DeregisterServiceAfter for the endpoint /agent/check/register
References: https://www.consul.io/api/agent/check#deregistercriticalserviceafter, https://www.consul.io/commands/services/register#usage
Domain : Register services and use service discovery
Q20 : Which of the following actions will happen when a service is placed into maintenance mode?
A. The service will be marked as unavailable
B. The service will be present in DNS or API queries
C. The service will not be present in DNS or API queries
D. The service will be restored after the default downtime
E. The service will be automatically restored on agent restart.
Correct Answers: A, C and E
Explanation
The endpoint /agent/service/maintenance/:service_id places a given service into “maintenance mode”.
- During maintenance mode, the service will be marked as unavailable and will not be present in DNS or API queries. This API call is idempotent.
- Maintenance mode is persistent and will be automatically restored on agent restart.
Option A is correct. During maintenance mode, the service will be marked as unavailable.
Option B is incorrect. During maintenance mode, the service will be present in DNS or API queries. The provided option is wrong.
Option C is correct. During maintenance mode, the service will be present in DNS or API queries.
Option D is incorrect. There is no default downtime associated with the maintenance mode. The provided option is wrong.
Option E is correct. During maintenance mode, the service will be automatically restored on agent restart.
Reference: https://www.consul.io/api-docs/agent/service#enable-maintenance-mode
Domain : Access the Consul key/value (KV)
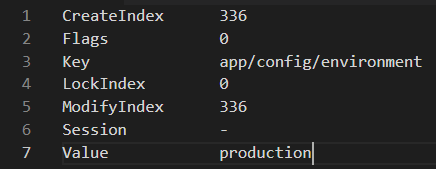
Question 21 : Fill in the blank with the correct command to achieve the mentioned output.
consul kv get _________ app/config/environment 
A. -recurse
B. -detailed
C. -detail
D. -keys
Correct Answer: B
Explanation
The option -detailed provides additional metadata about the key in addition to the value such as the ModifyIndex and any flags that may have been set on the key. The default value is false.
Option A is incorrect. The option -recurse will recursively look at all keys prefixed with the given path. The default value is false.
Option B is correct. -detailed command line flag will retrieve some additional metadata about the key-value pair.
Option C is incorrect. There is no such command line flag called -detail.
Option D is incorrect. The option -keys list keys which start with the given prefix, but not their values
References: https://www.consul.io/commands/kv/get#detailed, https://learn.hashicorp.com/tutorials/consul/get-started-key-value-store#query-data
Domain : Access the Consul key/value (KV)
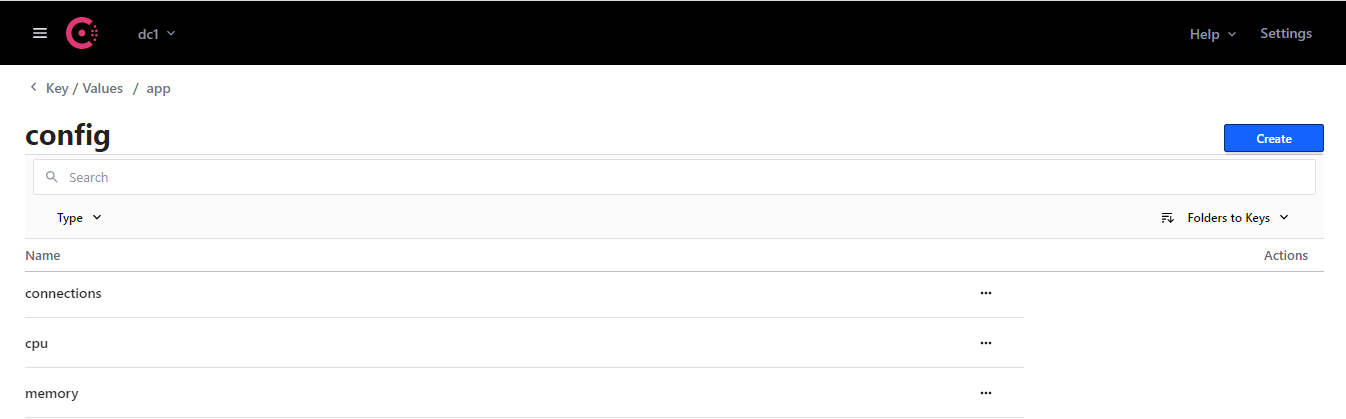
Q22 : Consider the following screenshot and select the valid command to list all the keys. 
A. consul kv get –keys app/
B. consul kv get –keys Key/Values/app/
C. consul kv get –keys app/config/
D. consul kv get –onlykeys app/
E. consul kv get –onlykeys Key/Values/app/
F. consul kv get –onlykeys app/config/
Correct Answer: C
Explanation
The -keys option is used to just list the keys which start with the specified prefix.
This is especially useful if you only need the key names themselves.
Sample Output:
consul kv get -keys app/config/
app/config/connections
app/config/cpu
app/config/memory
Option A is incorrect. The command “consul kv get –keys app/” will return only the key called config.
Option B is incorrect. The prefix path in the provided command “consul kv get –keys Key/Values/app/” is wrong.
Option C is correct. The command “consul kv get -keys app/config/” is used to list down the keys in the given prefix.
Option D is incorrect. There is no such command-line option called –onlykeys for the consul kv get command even though the prefix is valid.
Option E is incorrect. There is no such command line option called –onlykeys for the consul kv get command and the prefix is also wrong.
Option F is incorrect. There is no such command line option called –onlykeys for the consul kv get command even though the prefix is valid.
Reference: https://www.consul.io/commands/kv/get#listing-keys
Domain : Access the Consul key/value (KV)
Q23 : As a consul associate, you have stored a secret configuration value in the KV path app/config/secret/. Also, you want to implement a monitoring mechanism that will invoke the script /usr/bin/key-handler.sh whenever an update is detected.
Identify the correct command to achieve the same.
A. consul watch -type=key -key=app/config/secret/ /usr/bin/key-handler.sh
B. consul watch -type=keyprefix -key= app/config/secret/ /usr/bin/key-handler.sh
C. consul watch -type=key -key=app/config/secret/ -args=/usr/bin/key-handler.sh
D. consul watch -type=keyprefix -key=foo/bar/baz -args=/usr/bin/key-handler.sh
Correct Answer: A
Explanation
Consul KV can also be extended with the use of watches.
Watches are a way to monitor data for updates.
When an update is detected, an external handler is invoked. To use watches with the KV store the key watch type should be used.
Option A is correct. The command “consul watch -type=key -key=app/config/secret/ /usr/bin/key-handler.sh” is used to watch the key app/config/secret/ in the KV store.
Option B is incorrect. The provided command is used to watch a prefix of keys in the KV store, not the specific key.
Option C is incorrect. The provided command is wrong as there is no command line flag called -args
Option D is incorrect. The provided command is wrong as there is no command line flag called –args and also the type is keyprefix not the key.
References: https://www.consul.io/docs/dynamic-app-config/watches#watches, https://www.consul.io/docs/dynamic-app-config/watches#key, https://www.consul.io/docs/dynamic-app-config/kv#watches
Domain : Access the Consul key/value (KV)
Q24 : A third party application wants the data from Consul’s KV store for its own processing. But due to security limitations, direct access has been restricted. Which of the following tools could be used for this scenario?
A. EnvConsul
B. Consul Replicate
C. Consul Environment
D. Consul Migrate
E. Consul Access
Correct Answer: A
Explanation
Envconsul provides a convenient way to launch a subprocess with environment variables populated from HashiCorp Consul and Vault.
Environment variables are dynamically populated from Consul or Vault, but the application is unaware; applications just read environment variables. This enables extreme flexibility and portability for applications across systems.
Option A is correct. Envconsul provides a convenient way to launch a subprocess with environment variables populated from HashiCorp Consul and Vault. The 3rd party application can access the values from the environment variables.
Option B is incorrect. The daemon consul-replicate integrates with Consul to perform cross-data-center K/V replication.
Option C is incorrect. There is no such tool called “Consul Environment”.
Option D is incorrect. consul-migrate is a Go package and CLI utility to perform very specific data migration for Consul servers nodes.
Option E is incorrect. There is no such tool called “Consul Access”.
References: https://www.consul.io/docs/download-tools#download-consul-tools, https://github.com/hashicorp/envconsul/blob/master/README.md
Domain : Access the Consul key/value (KV)
Q25 : You have been provided with the task of discovering all the services running in the Consul datacenter in a single run. Fill in the blank with the correct command line flag to achieve the requirement.
consul-template -template=”all-services.tpl:all-services.txt” _____________
A. -one
B. -single-run
C. -once
D. -all
Correct Answer: C
Explanation
In Once mode, Consul Template will wait for all dependencies to be rendered. If a template specifies a dependency (a request) that does not exist in Consul, once mode will wait until Consul returns data for that dependency.
Option A is incorrect. There is no such command line flag called –one.
Option B is incorrect. There is no such command line flag called –single-run.
Option C is correct. The -once flag will tell the process to run once and then quit.
Option D is incorrect. There is no such command line flag called –all.
References: https://learn.hashicorp.com/tutorials/consul/consul-template#use-case-discover-all-services, https://github.com/hashicorp/consul-template/blob/master/docs/modes.md#once-mode
Domain: Explain Consul Architecture
Question 26. Which of the following ports are used for DNS-related queries in Consul?
A. 8502 TCP
B. 8600 TCP
C. 8301 TCP
D. 8502 UDP
E. 8600 UDP
Correct Answers: B, E
Explanation:
Consul is using the ports 8600 TCP & 8600 UDP to resolve the DNS queries. Before running Consul, the consul engineer should ensure the respective bind ports are accessible.
Option A is incorrect as this port is used by the gRPC API. Currently, gRPC is only used to expose the xDS API to Envoy proxies. It is off by default, but port 8502 is a convention used by various tools as the default. Defaults to 8502 in -dev mode.
Option B is correct as this port is used by the DNS interface to resolve DNS queries.
Option C is incorrect as this port is the Serf LAN port. This is used to handle gossip in the LAN. Required by all agents.
Option D is incorrect as this port is used by the gRPC API. Currently, gRPC is only used to expose the xDS API to Envoy proxies. It is off by default, but port 8502 is a convention used by various tools as the default. Defaults to 8502 in -dev mode.
Option E is correct as this port is used by the DNS interface to resolve DNS queries.
Reference:
https://learn.hashicorp.com/tutorials/consul/reference-architecture#network-connectivity
https://www.consul.io/docs/install/ports
Domain: Explain Consul Architecture
Question 27. Which of the following combinations (of port(s) and protocol(s)) needs to be enabled in the network configuration to permit the server agents to communicate between datacenters(multi-cluster environment)?
A. WAN GOSSIP TCP/UDP/8301
B. LAN GOSSIP TCP/UDP/8301
C. WAN GOSSIP TCP/UDP/8302
D. LAN GOSSIP TCP/UDP/8302
E. LAN GOSSIP TCP 8300
Correct Answers: C
Explanation:
Consul is using the Serf WAN port 8302 (both TCP and UDP protocols) to gossip over the WAN, to other servers
All the agents that are in a datacenter participate in a gossip protocol. This means there is a gossip pool that contains all the agents for a given datacenter.
Here we are discussing the communication between servers. Thus the server agents operate as part of a WAN gossip pool. This pool is different from the LAN pool as it is optimized for the higher latency of the internet and is expected to contain only other Consul server agents.
The purpose of this pool is to allow datacenters to discover each other in a low-touch manner.
Option A is incorrect as this port is used to handle gossip in the LAN not in the WAN gossip.
Option B is incorrect as this port is the Serf LAN port. This is used to handle gossip in the LAN which is required by all agents.
Option C is correct as this port is the Serf WAN port. This is used by servers to gossip over the WAN, to other servers. These ports are only used in multi-cluster environments.
Option D is incorrect as this port is used to handle WAN gossip, not in the LAN gossip.
Option E is incorrect as this port is used for Server RPC communication which in turn is used by servers to handle incoming requests from other agents.
Reference:
https://www.consul.io/docs/architecture#10-000-foot-view
Domain: Explain Consul Architecture
Question 28. By default, the data is not replicated between different Consul datacenters in the organization’s architecture.
A. True
B. False
Correct Answers: A
Explanation:
In general, data is not replicated between different Consul datacenters.
When a request is made for a resource in another datacenter, the local Consul servers forward an RPC request to the remote Consul servers for that resource and return the results. If the remote datacenter is not available, then those resources will also not be available, but that won’t otherwise affect the local datacenter.
There are some special situations where a limited subset of data can be replicated, such as with the Consul’s built-in ACL replication capability, or external tools like consul-replicate.
Reference:
https://www.consul.io/docs/architecture#10-000-foot-view
Domain: Access the Consul key/value (KV)
Question 29. The size limit of the Consul’s key/value store can be increased with the —————– configuration option
A. kv_maximum_value_limit
B. kv_max_value_size
C. kv_max_value_limit
D. kv_maximum_value_size
Correct Answers: B
Explanation:
The limit can be increased by using the kv_max_value_size configuration option. This configures the maximum number of bytes for a kv request body to the /v1/kv endpoint. This limit defaults to the raft’s suggested max size (512KB).
Option A is incorrect as there is no such configuration option as kv_maximum_value_limit.
Option B is correct as this configuration option is used to increase the limit.
Option C is incorrect as there is no such configuration option as kv_max_value_limit.
Option D is incorrect as there is no such configuration option as kv_maximum_value_size.
Reference:
Domain: Access the Consul key/value (KV)
Question 30. What is the maximum restricted size limit for an object stored in a Consul’s key/value store?
A. 1024 KB
B. 256 KB
C. 512 KB
D. 128 KB
Correct Answers: C
Explanation:
The main restriction on an object is size – the maximum is 512 KB.
Option A is incorrect as the correct value is 512 KB, not 1024 KB.
Option B is incorrect as the correct value is 512 KB, not 256 KB.
Option C is correct. The maximum restricted size limit for an object stored in a Consul’s key/value store is 512 KB.
Option D is incorrect as the correct value is 512 KB, not 128 KB.
Reference:
https://www.consul.io/docs/dynamic-app-config/kv#using-consul-kv
Summary
Hope these HashiCorp Consul Associate exam questions have provided you with clarity on the mentioned concepts and pushed you to gear up your preparations at another level.
For more such questions and content, just go through the HashiCorp Certified Consul Associate Practice Tests, and pass the certification exam on the very first attempt.
- Study Guide DP-600 : Implementing Analytics Solutions Using Microsoft Fabric Certification Exam - June 14, 2024
- Top 15 Azure Data Factory Interview Questions & Answers - June 5, 2024
- Top Data Science Interview Questions and Answers (2024) - May 30, 2024
- What is a Kubernetes Cluster? - May 22, 2024
- Skyrocket Your IT Career with These Top Cloud Certifications - March 29, 2024
- What are the Roles and Responsibilities of an AWS Sysops Administrator? - March 28, 2024
- How to Create Azure Network Security Groups? - March 15, 2024
- What is the difference between Cloud Dataproc and Cloud Dataflow? - March 13, 2024